Red Hat Blog
Why audits aren't enough
Compliance and security management are interdependent. Compliance depends on security rules for enforcement. Security depends on clear compliance guidelines. Any lack of visibility to the enforcement of security policies as related to specific regulations can expose an organization to risk. With increased regulation, new business processes due to COVID, and reduced budgets, CIOs, compliance officers, system administrators and legal teams are seeking ways to work together to reduce risk.
Organizations routinely conduct audits to identify gaps as regulations increase, but audits are not the best way to discover issues. Audits create stress for all. Red Hat Insights for Red Hat Enterprise Linux (RHEL) simplifies the management of compliance and security. Insights helps organizations address compliance in a systematic fashion and reduce operational costs. Insights can help enforce a variety of cybersecurity policies, (including PCI-DSS, HIPAA, CIS, etc.) that your organization needs to meet.
Automating compliance delivers transparency
Transparency is one of the main challenges as organizations implement their policies and then work cross-functionally to ensure compliance.
How do they communicate exceptions, changes or customizations? One approach is to use the Security Content Automation Protocol (SCAP) for accurate reporting for each of the systems defined in the compliance policies. The National Institute of Standards and Technology (NIST) defines SCAP as “a suite of specifications for exchanging security automation content used to assess configuration compliance and to detect the presence of vulnerable versions of software.”
Let’s review these challenges in detail to understand them further.
-
Transparency is critical to any regulatory compliance program. Today, customers using OpenSCAP with RHEL on their own are expected to manage and ensure the SCAP Security Guide (SSG) version is correctly configured for the RHEL system it is deployed on. It is an arduous and manual task to ensure proper configuration. misconfiguration. In larger environments, this problem is amplified, leading to confusion.
-
Accurate reporting is another key aspect of a solid compliance program. Oftentimes the lack of transparency cited above can lead to inaccurate reporting. Inaccurate reporting can lead to security gaps due to misconfigurations and non-compliance. If the correct version of the SCAP Security Guide (SSG) is not deployed on the system then there can be a misrepresentation of compliance. Attention to detail and transparence is crucial to ensure adherence to the appropriate level of policy.
Insights: Another pair of eyes
The Compliance service within Red Hat Insights enables users to configure, monitor, remediate, and report on regulatory compliance policies that are pertinent to their organization via OpenSCAP.
Insights reflects the extensive Red Hat vendor knowledge and experience with the RHEL platform for which it was built. Red Hat Insights is an operational, business, security and compliance risk management solution that provides continuous, in-depth analysis of registered Red Hat Enterprise Linux systems. Some users have referred to Insights as "like having an extra pair of eyes."
The extra eyes are included in your RHEL subscription. The Compliance service works in synchronicity with other Insights services such as Advisor, Vulnerabilities and Patch to help organizations access and prioritize risk.
The Compliance service now provides “X-ray” vision into your policies and allows you to tailor them.
-
Create and monitor: Users have the ability to configure and tailor compliance policies supported with Red Hat Enterprise Linux with the click of a few buttons and directly from within the compliance service. The compliance service works behind the scenes with OpenSCAP to assess systems defined within the policy and provide reporting that enables customers to understand where any gaps may exist.
More detail on how to address compliance challenges can be found in a previous post “Managing the security of your Red Hat Enterprise Linux environment with Red hat Insights.” This post provides more detail on how the Insights Compliance service helps customers with managing regulatory compliance in large environments using OpenSCAP with RHEL.
Unsupported or mis-configured OpenSCAP
The Compliance service now enforces the supported versions of SSG used on your systems with OpenSCAP on RHEL. With this change, users will be able to determine which version of the SSG they are running on any system and see quickly if it is misconfigured.
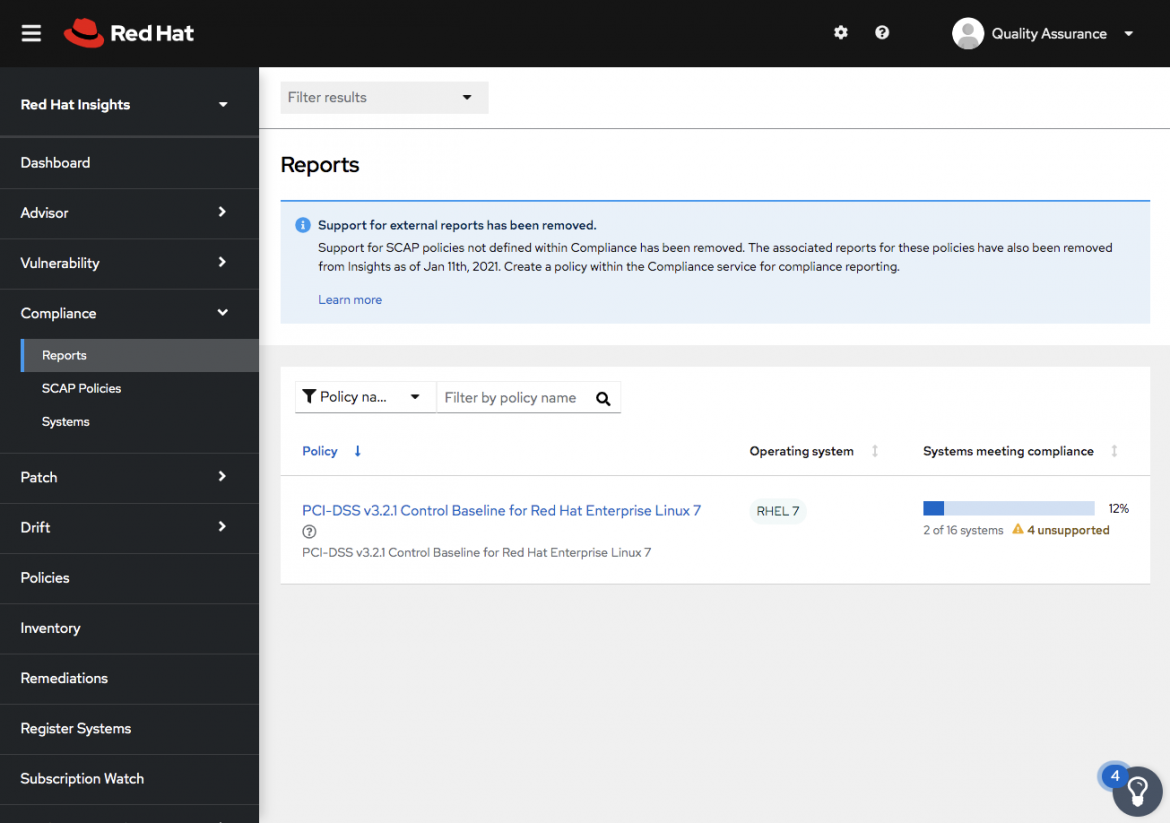
Figure 1. Compliance reports highlights 4 systems running unsupported configs in this view
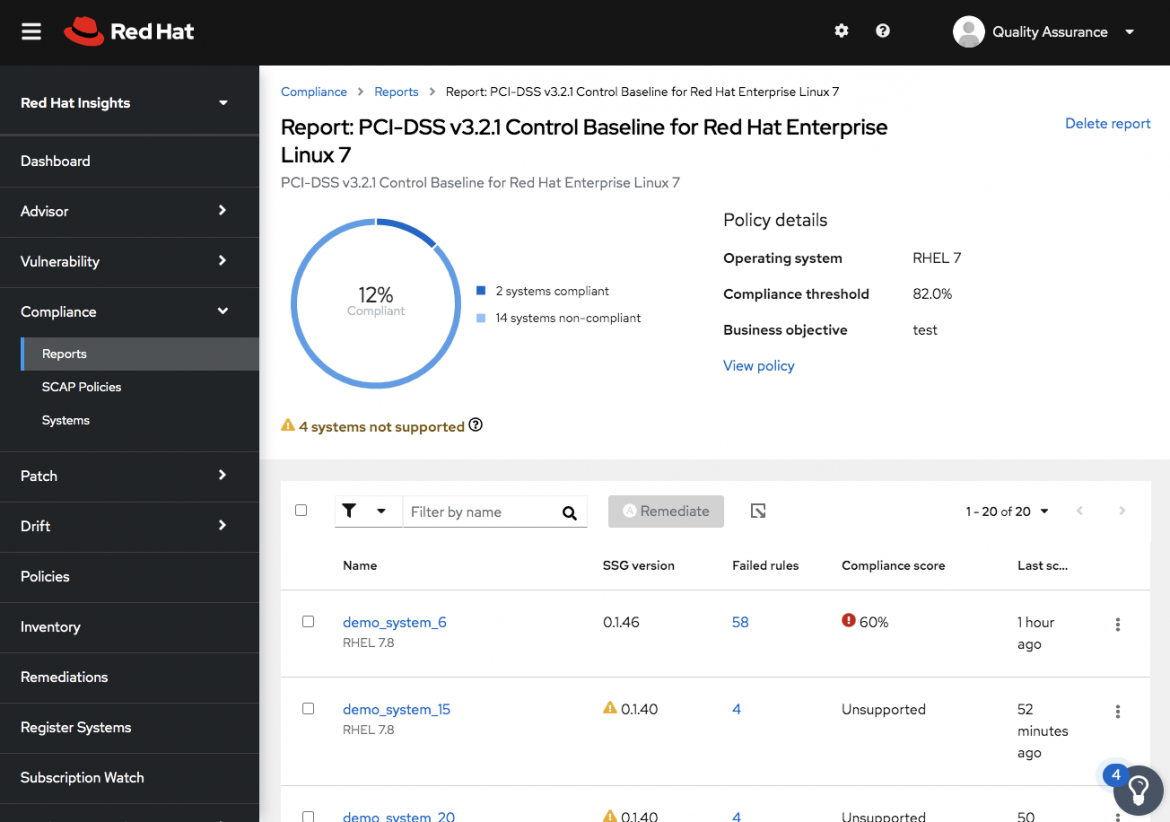
Figure 2. Compliance now highlights unsupported configurations in the Policy Reports views
For accurate reporting, customers will need to have the correct, specified SSG versions deployed on the system per the specs in Table 1.1. Not only does this meet the transparency and accuracy needs but it helps to reduce operational costs for managing the compliance program. (See Figures 1, 2, and 3)
 Figure 3. System reports pages provides a "best guess" result and highlights a misconfiguration
Figure 3. System reports pages provides a "best guess" result and highlights a misconfiguration
Compliance is a Journey
The functionality that’s defined within the compliance service of Insights continues to evolve with feature rich developments underway. We recognize that reporting, usability and integration to third party ticketing systems to further automate are crucial for customers to address compliance challenges. As the Red Hat team accompanies customers on their compliance journey we continue to simplify the tasks associated with compliance and face the challenges head-on with transparency and clarity.
Reporting, usability improvements, and integration to third party ticketing systems to further automate and make the workflows within your organization more seamless are on the roadmap.
Connecting is easier
Customers with a subscription to Red Hat Smart Management will also have access to push-button functionality available with the “Cloud Connector” within Red Hat Insights. The Cloud Connector provides a simpler way to connect and immediately take advantage of the recommendations in Red Hat Insights to remediate at scale across on-premise and cloud instances for RHEL. (See Figure 4)
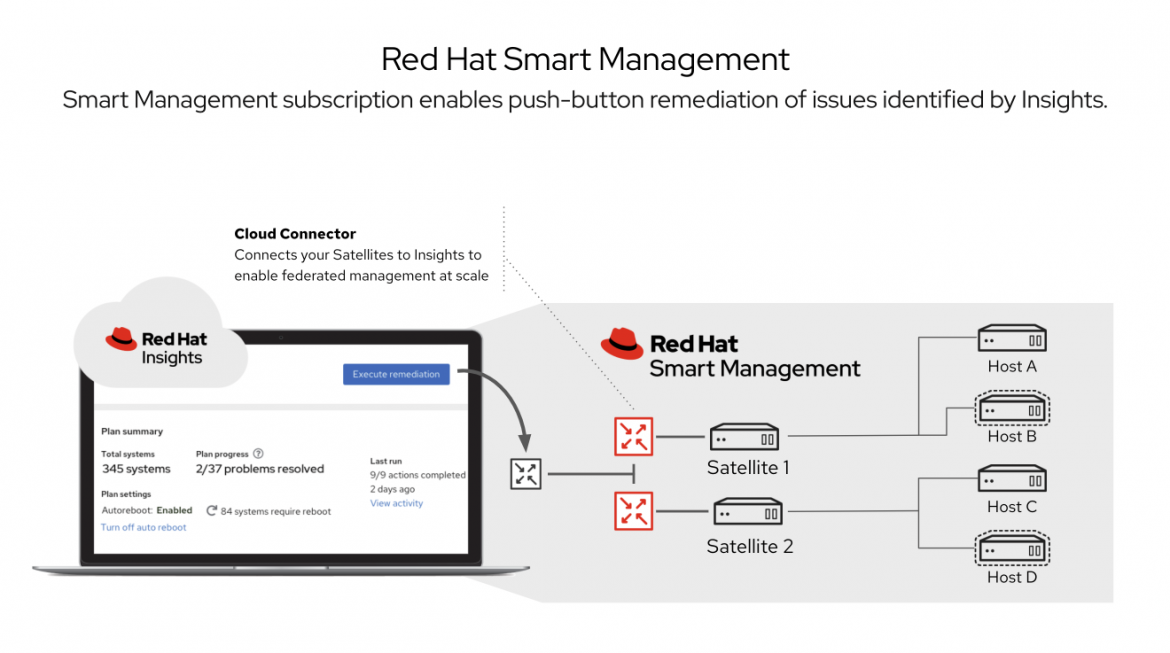
Figure 4. Cloud Connector via Red Hat Insights.
Want more information?
We held a Red Hat Insights webinar about managing security and compliance risk recently that included a short demonstration of the Vulnerability and Compliance services as part of Red Hat Insights. You can watch its recording on-demand here. I encourage you to also check out the Red Hat Insights Ask Me Anything Webinar Library which includes access to webinars on other aspects of Insights.
Red Hat Insights is included as part of your RHEL subscription - find more information and get started today by visiting Red Hat Insights.
Über den Autor
Mohit Goyal is a Senior Principal Product Manager for Red Hat Insights. Mohit brings a wealth of experience and skills in enterprise software having held roles as a software engineer, project manager, and as a product manager across software and travel industries. Goyal has a bachelor's degree in Computer Science from the Institute of Technology, University of Minnesota and a MBA from the Carlson School of Management, University of Minnesota. With his technical skills and business acumen, he helps build products to address problems faced by enterprises, with a focus on security, user experience, and cloud computing. When he's not writing user requirements, engaging with customers, or building product roadmaps, Mohit can be found running, cooking, or reading.
