Red Hat Blog
Davie Street Enterprises, our fictional Red Hat customer that is working its way through real-world digital transformation problems, is automating DevSecOps tooling across their hybrid cloud infrastructure using Red Hat Advanced Cluster Management.
Ok, let’s see it for real.
Last we saw Zachary L. Tureaud, he was in the early days of his promotion by Monique Wallace to lead Davie Street Enterprises' (DSE’s) shift towards DevSecOps. Tureaud laid out a comprehensive DevSecOps solution that includes Red Hat and its security partner ecosystem and is designed to shift security left in the DevOps life cycle. His goal is to not let security slow DSE’s application delivery down.
Wallace was impressed with Tureaud’s solution, but was concerned about the complexities of deployment. She asked Tureaud to test his vision on a new development project, code name “J.A.R.V.I.S”, for the DSE Smart Widget. The project allows the DSE Smart Widget’s speech capabilities to be customized to sound like the voices of superheroes. Wallace knew this project’s characteristics presented low security risk to the company, so it was a great opportunity for Tureaud to test these new security controls.
First things, first
The first item of business for Tureaud was to deploy the Red Hat OpenShift Container Platform.
As we saw earlier in Tureaud’s solution design, Red Hat OpenShift comes prepackaged with the necessary services for enterprise Kubernetes, including components that assist with security like SELinux, Red Hat Enterprise Linux (RHEL) CoreOS, and Security Context Constraints. These features saved Tureaud a significant amount of deployment time and costs.
Every time deploying Kubernetes crosses his mind, Tureaud remembers when he first looked at the CNCF landscape, and how he was overwhelmed with the number of choices and didn’t know how to get started. Luckily, Tureaud attended the 2021 Red Hat Security Symposium in July and learned all about Red Hat OpenShift’s default security features, which cut down the time to deploy and adopt enterprise Kubernetes from months to days.
Furthermore, Tureaud learned Red Hat recently made it very simple to install, operate and upgrade his OpenShift clusters through the OpenShift Cluster Manager (OCM). OCM is accessible by logging into Red Hat’s Hybrid Cloud Console.
On the OpenShift page, Tureaud clicked “Create Cluster,” and chose his preferred private cloud provider to run it himself. Knowing he didn’t need any significant customization of the cloud infrastructure and didn’t have any specific networking or credential requirements, Tureaud chose the installer-provisioned infrastructure (IPI) option to let the installation process automatically provision the cloud infrastructure.
Once he downloaded the pull secret and OpenShift CLI tools, Tureaud opened up his terminal and ran:
$./openshift-install create cluster
After responding to the prompts, Tureaud thought to himself, “Time for some coffee. I’ll go with a mocha this time.” He knew he could step away from the installer and let it take care of everything.
Enhance and extend with Red Hat Partners
The next step Tureaud had on his list was to deploy CyberArk, Synopsys, and Sysdig to extend and enhance the security features of his OpenShift cluster, providing the layered approach he designed for DSE. Each deployment was straightforward and Tureaud used the following resources to assist in those deployments:
CyberArk
To ensure that the J.A.R.V.I.S project didn’t have any secrets stored in Kubernetes, and that secrets weren’t stored in their code repository, Tureaud implemented CyberArk Secrets Management by first deploying the Conjur Cluster, and then by setting up the Follower inside OpenShift.
CyberArk has several options to retrieve credentials within applications. Tureaud felt the best approach for DSE was the Secretless Broker option that he learned in a Red Hat and CyberArk workshop. The Secretless approach provides the least amount of developer responsibility to manage application secrets.
Synopsys
Since DSE already had a Black Duck server for their legacy application development, all Tureaud had to do was install the Black Duck Connector for OpenShift using the Black Duck for OpenShift Operator found in the Operator Hub in their OpenShift instance.
What Tureaud was most excited about with Synopsys’ technology was a recently released product called Intelligent Orchestration, which can determine if and what application security analysis tools to run based on the committed changes in the application.
“No more wasted time running a SAST or SCA scan on code that hasn’t changed!” Tureaud thought to himself.
This would cut down build time significantly, and provide security analysis feedback faster to the developers since they don’t need to wait for the daily build that runs all the application analysis tools. As shown in the pipeline details below, Intelligent Orchestration provides the ability to determine what application security analysis to run in a parallel sequence.
 Sysdig
Sysdig
To round out Tureaud’s DevSecOps vision, he deployed the Sysdig Agent Operator, which could help to provide another layer of security.
In no time, Tureaud had his DevSecOps technology stack up and running. The very next item of business was to get the development team enabled on the functionality of these security features. He knew that Red Hat hosts hands-on workshops for CyberArk, Synopsys and Sysdig on OpenShift.
Tureaud contacted a DevSecOps expert at Red Hat, and was able to get all three workshops scheduled. The workshops accelerated the team’s ability to work with both Red Hat OpenShift and Red Hat’s partner technologies, cutting the learning curve significantly.
Within weeks, the J.A.R.V.I.S project deployed the first superhero voice customization as an additional microservice for DSE’s Smart Widgets. The deployment passed DSE’s security policies with no exceptions as most of the containers' security issues were handled during development and build. The security controls Tureaud implemented were speeding up deployment.
At Wallace’s next one-on-one meeting with Tureaud, she was impressed with the progress, but with a caveat: “Now, I want you to do this across all of our development projects, and ensure that every cluster has the same security controls.”
Tureaud replied calmly, "I’d be happy to. Have you heard of Red Hat Advanced Cluster Management for Kubernetes? It can help with our DevSecOps vision.”
Wait now, what? Red Hat Advanced Cluster Management = DevSecOps?
Looking a bit puzzled, Wallace pressed Tureaud, “Well, yes, I know about Red Hat Advanced Cluster Management, but you’ll have to explain to me why it helps DevSecOps.”
Tureaud went on to explain that DSE has hundreds of development projects. There are some that have migrated over to different flavors of Kubernetes, some that are Red Hat OpenShift, and some that still need to migrate to DSE’s DevOps process.
Susan Chin, DSE’s Senior Director of Development, and Ranbir Ahuja, DSE’s Senior Director of IT Operations, have made Red Hat Advanced Cluster Management a key component to facilitate the evolution and migration of all these development projects because of its cluster and life cycle capabilities.
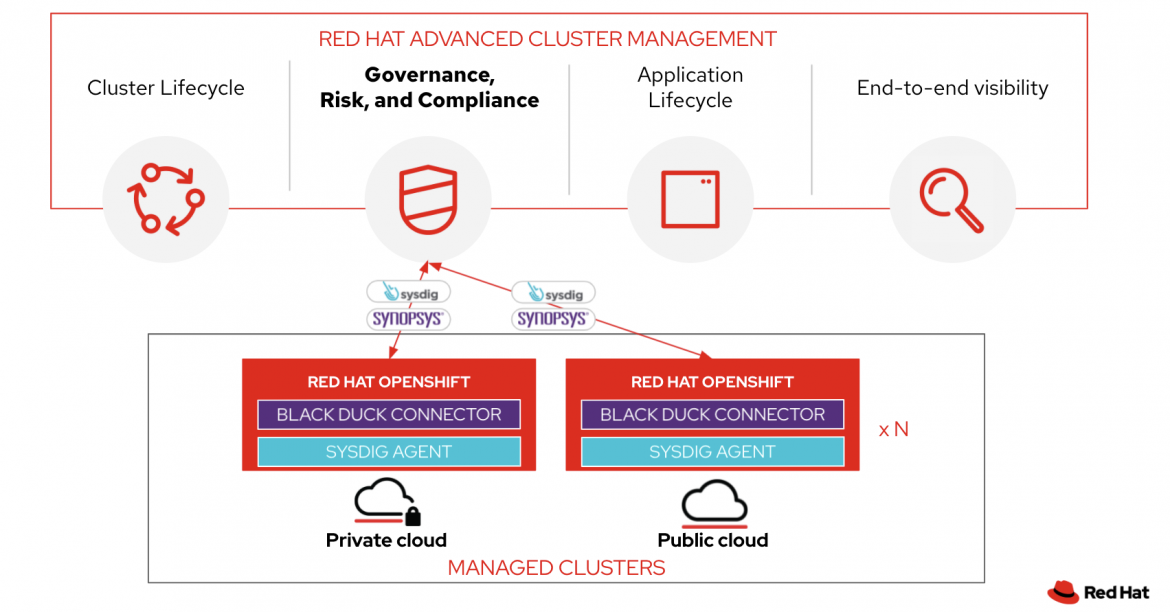 With Red Hat Advanced Cluster Management, Chin appreciated the ability to:
With Red Hat Advanced Cluster Management, Chin appreciated the ability to:
-
Easily manage and deploy DSE’s applications to specific clusters and across their entire hybrid cloud Kubernetes environment.
-
Use GitOps methodologies to deploy applications from multiple sources.
-
View a detailed graphical application topology, which shows state and relationships across all the clusters.
Ahuja, on the other hand, was excited about the unified cluster management capabilities of Red Hat Advanced Cluster Management, because it allowed him to:
-
Centrally create, update, and delete DSE’s Kubernetes clusters across their private and public clouds.
-
Search, find, and modify any Kubernetes resource.
-
Quickly troubleshoot and resolve issues across DSE’s fleet of clusters.
Wallace was about to ask Tureaud to tell her something she didn’t know, but here’s where Tureaud discussed his favorite features of Red Hat Advanced Cluster Management that provide governance across DSE’s fleet of clusters through centrally enforcing policies.
What’s even more exciting for Tureaud’s DevSecOps tooling is that Sysdig and Synopsys already have Red Hat Advanced Cluster Management policies that were collaboratively developed with Red Hat.
The Sysdig’s Red Hat Advanced Cluster Management policy checks that the Sysdig agent is deployed to the nodes on any set of clusters specified by the Sysdig Operator. The same is true with the Black Duck Red Hat Advanced Cluster Management policy, as it is there to verify that the Black Duck Connector is deployed and has the ability to show if any pod is in violation of Black Duck policies in the Red Hat Advanced Cluster Management user interface.

Trust, but verify
Tureaud didn’t have to say much more as Wallace could see there is something for everyone in a DevSecOps world with Red Hat Advanced Cluster Management. Reassured in her investment with Red Hat as well as her decision to promote Tureaud, she felt more confident about DSE’s continued path towards digital transformation.
However, DSE is a results-oriented business, and Wallace needed metrics to report up to DSE’s board next quarter. As Wallace began to conclude her one-on-one with Tureaud, she said:
“I’m impressed with what I saw here today, Zachary. This is great stuff. In our next one-on-one, I’d like to see the numbers on how your DevSecOps vision is improving our development metrics.”
“I’m on it, Monica!” said Tureaud, and the second he hung up, he sent a text to Chin and Ahuja: "My meeting with Monica went well. Time to start gathering the DevOps metrics that include the security controls. Let's chat soon."
Über den Autor
Dave Meurer currently serves as a Principal Solution Architect on the Red Hat Global Partner Security ISV team, where he owns technical relationships and evangelism with security independent software vendor partners of Red Hat. Before joining Red Hat, he spent nine years in the Application Security industry with Synopsys and Black Duck, where he served in similar roles as the director of technical alliances and sales engineering.

