Red Hat ブログ
As a Product Manager at Red Hat, I speak with customers to understand the challenges they seek to address and recommend Red Hat technologies that can help maximize efficiency and productivity in their environments.
Although no two organizations are the same, some of their most cited challenges include (1) managing the sprawl of their infrastructure footprint in an open-hybrid cloud environment (2) lacking resources to manage it with and (3) an increasing focus on security and compliance concerns.
Red Hat Insights for Red Hat Enterprise Linux is designed and built to help customers address concerns across management of compliance and security. For managing security vulnerabilities on their estate of servers, Insights has a Vulnerability service that helps customers identify, assess, and triage Common Vulnerability and Exposures (CVEs), remediate them with Red Hat Ansible Automation Platform, and report on the health of the servers across hybrid cloud footprint for any systems registered with Insights.
Given trends (1) and (2) mentioned above, having actionable threat intelligence is key to staying ahead and prioritizing CVEs to minimize risk for the organization.
Introducing the “Known Exploit” flag
The Insights Vulnerability service already has the following data points to help customers triage/prioritize CVEs:
-
Severity (Red Hat’s rating of the CVE).
-
CVSS base score.
-
Number of systems exposed.
-
Publish date.
-
Business risk (a user-defined field once risk has been identified).
-
Status (a user-defined field to track where a CVE is in it’s life cycle).
As of April 2021, the Insights Vulnerability service reports out threat intelligence about CVEs that are known to publicly have any exploit code or have, in fact, been exploited. A label called “Known Exploit” will appear next to CVEs that are deemed by Red Hat to have been publicly exploited (See Figure 1).
It’s important to note the “Known Exploit” flag does not reflect your environment.
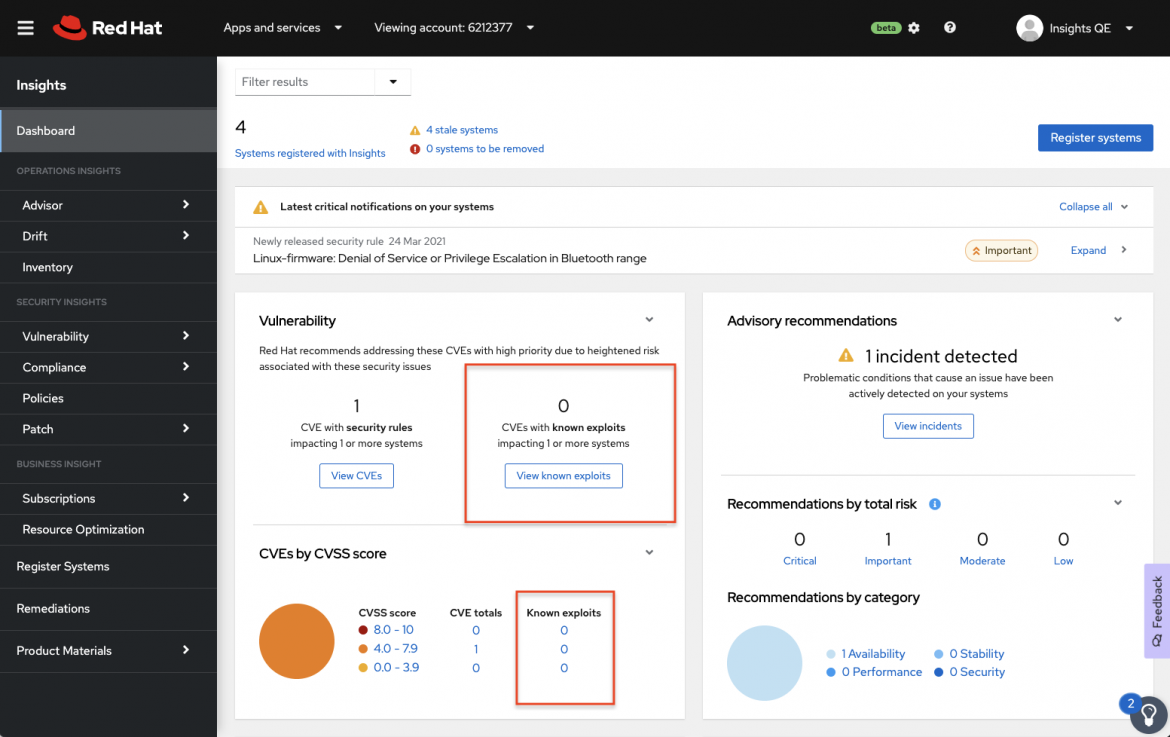 Figure 1. Any CVEs with the Known Exploit flag are now shown in the Insights Dashboard
Figure 1. Any CVEs with the Known Exploit flag are now shown in the Insights Dashboard
Why is threat intelligence important?
Many customers have often cited the need for deeper threat intelligence that was relevant to their environments to help them with prioritizing and ranking thousands of CVEs to keep their organization secure.
According to SANS, one of the top five questions to ask as you gather threat intelligence for your organization is “What type of attacks/threats does your organization fear most?”
-
DDoS attacks.
-
Banking Trojan.
-
Drive-by / EK.
-
Credentials' Phishing.
-
Intellectual Property (IP) exfiltration.
-
Etc.
Understanding and recognizing the type of exploits that pose the highest threat to your organization is always challenging with new vulnerabilities identified daily and more aggressive tactics and sophisticated exploits. Recognizing when your organization is vulnerable to a particular exploit is not easy.
It is widely agreed that CVEs that have been exploited in the field pose a higher level of risk. Now, Red Hat Insights is providing additional correlation between vulnerabilities and exploits. Vulnerabilities with known exploits will reflect the additional level of risk based on the nature of the exploit and will be flagged as having been used in a particular known exploit or multiple exploits.
Flagging Known Exploits
Red Hat wants you to be aware of your organization’s exposure to particular exploits. Red Hat Insights can highlight vulnerabilities with a Known Exploit flag when the vulnerability has been used by threat actors within a particular exploit.
If a CVE is flagged with a Known Exploit flag, the CVE should be reviewed with a sense of urgency to determine the risk to the organization and next steps to remediate and patch it.
The status of the “Known Exploit” flag will appear in a few different places within Red Hat Insights:
-
Insights Dashboard - The Vulnerability section (Figure 1) of the Insights Dashboard will show any CVEs that have been identified with the flag.
-
CVE List View - The view (Figure 2) of the CVEs will clearly show any CVEs with this flag. This is where users triage and assess their systems for CVEs.
-
CVE Details Page - This is the details page (Figure 3) for a specific CVE. If a CVE has met this criteria, the flag will be shown.
-
Reporting - The Executive Report and PDF custom reports will both show any CVEs that meet this criteria.
 Figure 2. CVE List View within Vulnerability where users triage their CVEs
Figure 2. CVE List View within Vulnerability where users triage their CVEs
 Figure 3. CVE Detail Page now shows if a specific CVE has has known public exploit
Figure 3. CVE Detail Page now shows if a specific CVE has has known public exploit
Making threat intelligence actionable
Making threat intelligence actionable is a journey and SANS literature can help educate you and your team on how to identify sources of threat intelligence like data feeds. Yet no matter how many data feeds you receive, you will need to correlate them to your environment and determine what your organization’s weaknesses are.
This is where Red Hat Insights can help your organization prepare for different types of threat vectors. It is constantly evaluating your environment, not only for vulnerabilities, but now, for known exploits that may make you more vulnerable to threat actors that may try to capitalize on those vulnerabilities. It flags the known exploits and provides you with your custom threat analysis.
This information can help your team prioritize risks and mobilize your organization to reduce risk. Learn more about how to use Red Hat Insights to help secure your Red Hat Enterprise Linux (RHEL) operations and get your personalized threat analysis.
Want more information?
I encourage you to check out the Red Hat Insights Ask Me Anything Webinar Library which includes access to webinars on other aspects of Insights.
Red Hat Insights is included as part of your RHEL subscription. Find more information and get started today by visiting Red Hat Insights.
About the author
Mohit Goyal is a Senior Principal Product Manager for Red Hat Insights. Mohit brings a wealth of experience and skills in enterprise software having held roles as a software engineer, project manager, and as a product manager across software and travel industries. Goyal has a bachelor's degree in Computer Science from the Institute of Technology, University of Minnesota and a MBA from the Carlson School of Management, University of Minnesota. With his technical skills and business acumen, he helps build products to address problems faced by enterprises, with a focus on security, user experience, and cloud computing. When he's not writing user requirements, engaging with customers, or building product roadmaps, Mohit can be found running, cooking, or reading.
