A new series of vulnerabilities in Intel processors, known as Microarchitectural Data Sampling, or more simply MDS, was recently made public and Red Hat released information about how the vulnerabilities affect our software and how to protect your organization.
In the simplest terms, MDS is a vulnerability in Intel processors similar to Spectre and Meltdown; it allows a guest to read protected memory from anywhere on the host or guest. To mitigate the risks exposed by MDS, a combination of updated microcode, updated kernel(s), patches, and administrator action will need to be taken for both the hypervisors and virtual machines in your Red Hat Virtualization deployment. Unlike some similar vulnerabilities, simply disabling SMT and/or hyper-threading is not enough to protect your applications.
Protecting your applications
The Red Hat Virtualization team released updates for both 4.2 and 4.3, implementing code-based mitigations. For addressing MDS vulnerabilities when using versions 4.1 or earlier, disabling multithreading (SMT) using the server BIOS is the recommended method.
If you are using Red Hat Virtualization 4.2, please be aware it is considered part of the extended update services (EUS) channel since Red Hat Virtualization 4.3 became generally available (GA) on May 10, 2019. This means you will need to update the repositories to enable the EUS channel on the hosts before the newest updates are visible.
In addition to updating Red Hat Virtualization Manager to the latest version, there are several additional steps which may be taken for hosts and guests:
For hypervisor hosts:
-
Updated microcode and BIOS should be utilized. Red Hat Virtualization and RHEL include updates from Intel for microcode; you should also work with your hardware vendor to determine if you’re running the recommended microcode and BIOS.
-
Update the kernel to the latest available for your version of RHEL.
-
Apply the most recent Red Hat Virtualization Host and/or RHEL updates.
-
Disable multithreading using kernel boot parameters from the Red Hat Virtualization Manager interface.

For virtual machines:
-
Use the “MDS” CPU type. After updating your Red Hat Virtualization deployment, apply the MDS mitigations, and update the cluster CPU type to “Intel XXX IBRS SSBD MDS Family” CPU type for your cluster. This will apply mitigations for Spectre, Meltdown, and MDS.
-
Update the kernel and other packages to the latest available and follow the recommendations from Red Hat and/or Microsoft for your guest operating system.
-
Disable guest hyperthreading. This can be done by setting the number of threads per core to one for the virtual machines. This is the default value.
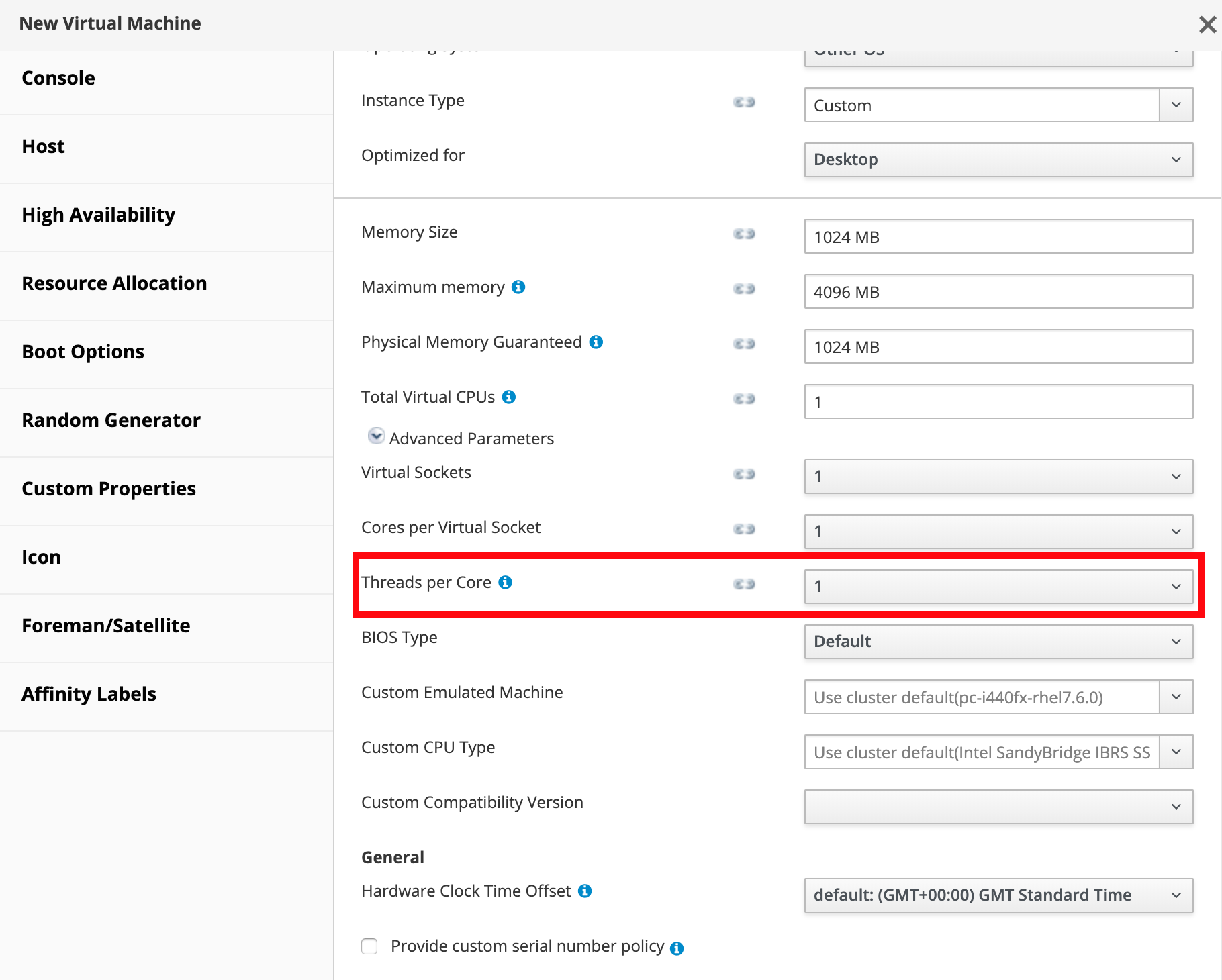
The standard update and upgrade procedures should be used when applying the MDS mitigation updates. If you’re using the self-hosted Red Hat Virtualization manager, be sure to run engine-setup again afterward so that the cluster CPU options are updated.
Knowledge is power
MDS is only one of the latest major vulnerabilities which broadly affects many IT systems. Be sure to read Red Hat’s Vulnerability Response article documenting the issues. Also a very helpful explanation from Jon Masters about what MDS is, and how it is exploited to get data from hosts with a technical deep dive in this 17 minute video that provides a detailed look into MDS and similar vulnerabilities.
Sobre o autor
Mais como este
Navegue por canal
Automação
Saiba o que há de mais recente nas plataformas de automação incluindo tecnologia, equipes e ambientes
Inteligência artificial
Descubra as atualizações nas plataformas que proporcionam aos clientes executar suas cargas de trabalho de IA em qualquer ambiente
Serviços de nuvem
Aprenda mais sobre nosso portfólio de serviços gerenciados em nuvem
Segurança
Veja as últimas novidades sobre como reduzimos riscos em ambientes e tecnologias
Edge computing
Saiba quais são as atualizações nas plataformas que simplificam as operações na borda
Infraestrutura
Saiba o que há de mais recente na plataforma Linux empresarial líder mundial
Aplicações
Conheça nossas soluções desenvolvidas para ajudar você a superar os desafios mais complexos de aplicações
Programas originais
Veja as histórias divertidas de criadores e líderes em tecnologia empresarial
Produtos
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Red Hat Cloud Services
- Veja todos os produtos
Ferramentas
- Treinamento e certificação
- Minha conta
- Recursos para desenvolvedores
- Suporte ao cliente
- Calculadora de valor Red Hat
- Red Hat Ecosystem Catalog
- Encontre um parceiro
Experimente, compre, venda
Comunicação
- Contate o setor de vendas
- Fale com o Atendimento ao Cliente
- Contate o setor de treinamento
- Redes sociais
Sobre a Red Hat
A Red Hat é a líder mundial em soluções empresariais open source como Linux, nuvem, containers e Kubernetes. Fornecemos soluções robustas que facilitam o trabalho em diversas plataformas e ambientes, do datacenter principal até a borda da rede.
Selecione um idioma
Red Hat legal and privacy links
- Sobre a Red Hat
- Oportunidades de emprego
- Eventos
- Escritórios
- Fale com a Red Hat
- Blog da Red Hat
- Diversidade, equidade e inclusão
- Cool Stuff Store
- Red Hat Summit

