The software supply chain has quickly become the latest target for malicious actors, with targeted attacks on foundational software components intended to orchestrate data breaches, initiate service outages or worse. Today, we announced the release of Red Hat Trusted Software Supply Chain for businesses to more consistently code, build and monitor a trusted supply chain within their software factory. This allows software development teams and their business leaders to maintain and grow user trust.
Why software supply chains matter
Development teams rely on open source technology to keep up with rapidly-changing customer needs. But some of these codebases also contain software components that have seen no development activity in years. As an example, the now infamous Log4j vulnerability was in place for years before being exploited. Software has potentially dozens if not hundreds of transitive dependencies that may have seen no feature upgrades, no code improvements and no security fixes for substantial periods of time, which presents—an attack surface ripe for a possible zero day exploit. This has given pause to IT security teams who are unable to continuously monitor and test for code vulnerabilities, much less be directed to perform critical security maintenance activities.
Code, build, monitor to a trusted software supply chain
From the same supply chain which Red Hat has used to more safely deliver tried, tested and trusted content into enterprise software for 30 years, customers can now do the same with just a few clicks. Our cloud service pre-integrates guardrails into each phase of the DevSecOps framework to offer teams a better security posture while also providing faster time to value. Here’s how.
Code with Red Hat Trusted Content
Red Hat Trusted Content, a service offered as part of Red Hat Trusted Software Supply Chain, helps to identify transitive dependencies and security vulnerabilities, enabling you to catch and mitigate known software risks and vulnerability exposures earlier in the development process. This helps remove manual toil and avoid costly rework.
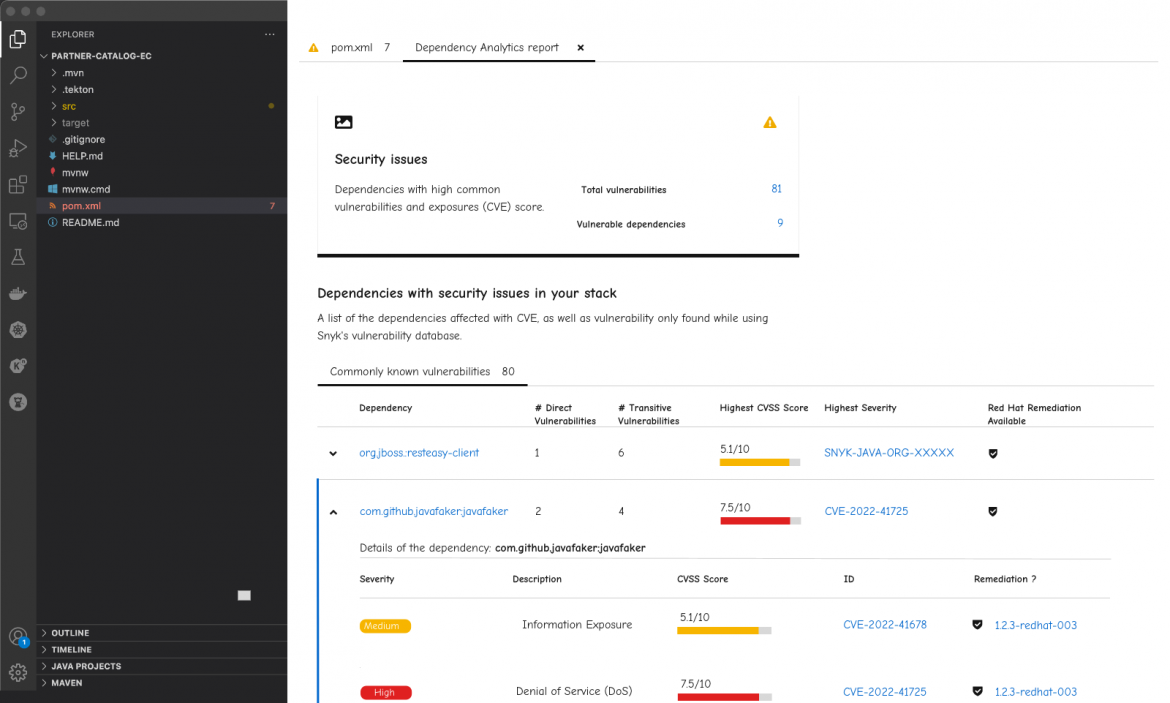
Image 1: Analyze and fix security vulnerabilities from the IDE
Developers never want to deploy anything that has a severe vulnerability, but they currently need to spend time manually tracking down malicious code instead of focusing on building new features. By using a trusted software supply chain, you can follow through on IT security best practices without incurring additional work by:
- Reducing development times through access to a trusted content repository that lets your developers choose reusable components delivered with provenance, signatures and attestation.
- More quickly identifying transitive dependencies and potential vulnerabilities in the code source by running real-time software composition analysis (SCA) directly from your local IDE.
- More readily finding Vulnerability Exploitability eXchange (VEXs) and Software Bill of Materials (SBOMs) for Red Hat products and packages.
- Gaining greater insights about dependencies and vulnerabilities by uploading your own SBOM for analysis.
Build with Red Hat Trusted Application Pipeline
The second new service offered through Red Hat Trusted Software Supply Chain, Red Hat Trusted Application Pipeline helps to improve security and compliance in pipeline orchestration with a ready-to-use, security-focused CI/CD pipeline. The service helps IT organizations stay compliant with standards and regulations without slowing down development productivity and efficiency.

Image 2: Default custom pipelines that meets SLSA level 3 standards
When safeguarding build systems, accounting for all packaged components and dependencies can be challenging. It takes a high level of manual effort and expertise to generate and maintain CI/CD pipelines. Red Hat Trusted Application Pipeline helps ease these challenges, enabling teams to build and deploy continuously through:
- Source to cloud for importing your existing Github repositories or using one of our bundled samples
- A build-ready pipeline that creates your Java, Python, Node or Go-based application into a container image, applies the appropriate attestations, cryptographic signatures and provenance via Tekton Chains
- Automatic deployment of your newly created container image into a provided development environment
- Enterprise contract-driven release plan with 43+ rules based on the rego policy language to verify that the container image meets SLSA guidelines, such as signed build provenance in auto-generated SBOMs, network isolated builds, base images pulled from appropriate registries and more
- GitOps-based continuous deployment via an embedded ArgoCD to your Kubernetes
Monitor with Red Hat Advanced Cluster Security Cloud Service
The newly-announced Red Hat Advanced Cluster Security Cloud Service helps more consistently monitor the behavior of software components for continuous improvement from runtime to build. With high-fidelity detection and fewer false positives in a timely manner, this helps IT security teams to reduce alert noise and fatigue, helping to improve response times to security issues faster.
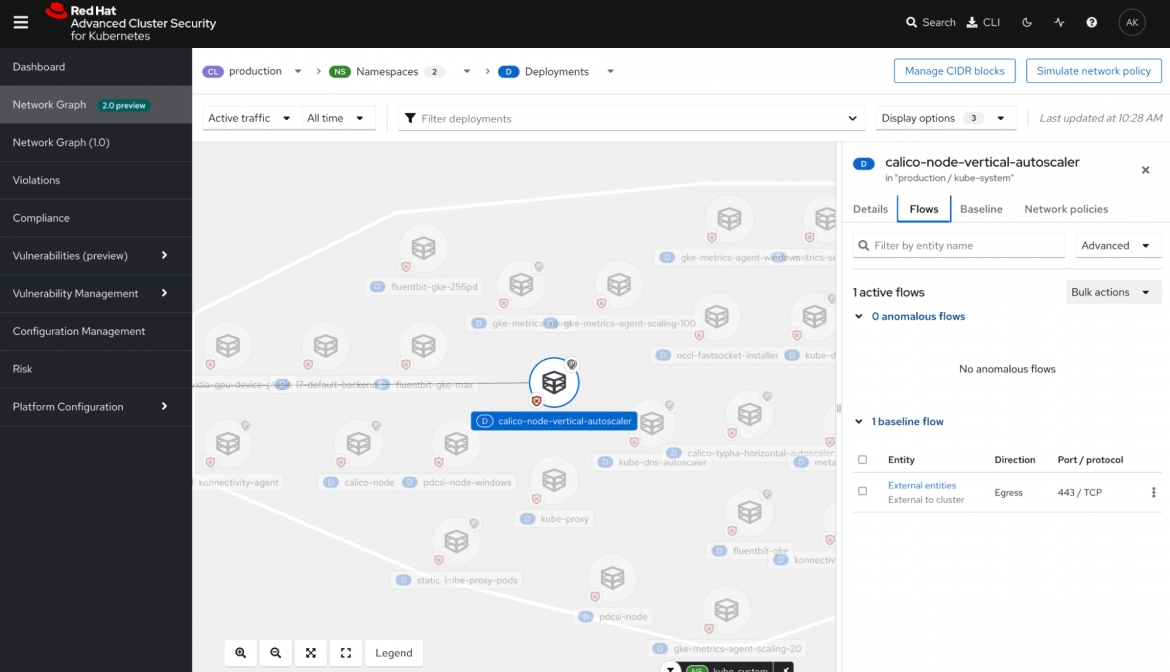
Image 3: Continuously monitor and direct on anomalous behavior
Vulnerabilities found at runtime can be extremely costly, as this causes an immediate impact on user trust. But isolating security issues in production is complicated, involving tracking a huge ecosystem of services; Red Hat Advanced Cluster Security Cloud Service helps teams move faster to address these issues by:
- Preventing high-risk workloads from being deployed or run using out-of-the-box deploy-time and runtime policies.
- Hardening workloads by enforcing network policies that adhere to the principle of least privilege.
- Allow-listing and behavioral modeling to detect anomalous application behavior indicative of a threat at runtime.
- Monitoring known good behavior to configure custom policies and alerts for anomalous and malicious behavior.
- Auditing for compliance across hundreds of controls
Take the next steps
With Red Hat Trusted Software Supply Chain, application development leaders can release applications more quickly while meeting their IT security requirements earlier. Software security is no longer an afterthought as businesses increase their supply chain resiliency to match the speed of their innovation. This means business leaders can keep and grow user trust while reducing the risks of reputational damage, customer churn and revenue loss.
To learn more, visit red.ht/trusted. Sign up for your service preview of Red Hat Trusted Content and Red Hat Trusted Application Pipeline. Then join the conversation with your peers at our coming DevNation techtalk.
关于作者
A lifelong developer advocate, community organizer and technology evangelist, Burr Sutter is a featured speaker at technology events around the globe—from Bangalore to Brussels and Berlin to Beijing (and most parts in between). He is currently Red Hat’s Chief Developer Evangelist. A Java Champion since 2005 and former president of the Atlanta Java User Group, Burr founded the DevNexus conference—now the second largest Java event in the U.S.—with the aim of making access to the world’s leading developers affordable to the developer community. When not speaking abroad, Burr is also the passionate creator and orchestrator of highly-interactive live demo keynotes at Red Hat Summit, the company’s premier annual event.
Sudir Prasad is a Product Management and Engineering leader driving Secure Software Supply Chain and Data Services. His current focus is to unburden developers and enterprises in managing the risk of their open source software dependency portfolio, reducing development time and cost by remediating issues earlier in the development cycle. He wants to help customers leverage Red Hat's experience and expertise with enterprise hardening of open source in their applications.
产品
工具
试用购买与出售
沟通
关于红帽
我们是世界领先的企业开源解决方案供应商,提供包括 Linux、云、容器和 Kubernetes。我们致力于提供经过安全强化的解决方案,从核心数据中心到网络边缘,让企业能够更轻松地跨平台和环境运营。


