红帽博客
As many specialists in the security world know - the RSA Security Conference is one of the biggest security conferences in North America. This year it was once again held in San Francisco at the Moscone Center. Every year the conference gets bigger and bigger, bringing in more and more people and companies from all over the world.
If you attended - you may have noticed that Red Hat had a booth this year. Located in the corner of the main expo floor (not far from some of the “big guys” like: IBM, Microsoft, EMC, CA Technologies, and Oracle) we were in a great location - receiving no shortage of traffic. In fact, despite staffing the booth with six Red Hatters we didn’t have any “down time” - everyone seemed to be interested in what Red Hat has to offer in security.
Over the course of the conference I made a few interesting observations...
More than Just Linux
While many conference attendees know about Red Hat in general and Linux in particular - most were not familiar with our whole portfolio of products. Many perceived Red Hat solely as "the Linux vendor" and nothing more. People at the conference were pleasantly surprised to hear that the Red Hat portfolio includes the whole stack as shown in the picture below:
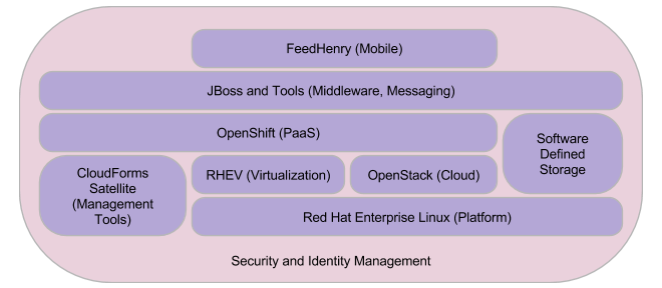 Booth Size Does Not Correlate to Quality or Competitiveness of Offering
Booth Size Does Not Correlate to Quality or Competitiveness of Offering
Many conference attendees were surprised by the small size of our booth. Well, as mentioned above, what they might not have realized is that Red Hat brings the whole stack to the table. It has security and identity management products and projects but they are just a fundamental part of a bigger picture - not something that Red Hat sees as stand-alone products or opportunities to compete with other security vendors.
Actually, what we do is more “matter of fact” security. Nevertheless, we were proud to answer the question; “Red Hat? So what are you showcasing here?” with a good story about our Identity Management (IdM) offerings (based on the FreeIPA and SSSD open source technologies).
The fact that these security features are delivered as components of Red Hat Enterprise Linux without extra charge was a surprising fact to many. The functionality provided by Identity Management (IdM) is competitive in the market as it combines a whole slew of authentication, authorization, privilege escalation, and single-sign-on capabilities that few other vendors can offer in the operating system.
On one side IdM “speaks” native protocols and acts as a central authority for Linux and UNIX clients. On the other it is a gateway between Linux/UNIX environments and Windows-based Active Directory-centric parts of the infrastructure. Many attendees, after hearing about our built-in capabilities, found our identity management an attractive, low cost identity management solution.
Interest Unbound
I mentioned the high level of booth traffic we received… this led to us to having many conversations with all kinds of people. At some times all of us were engaged in a conversation at once, and we were frequently involved with more than one person at a time. It was a pleasure to see how the lights were turning on in the eyes of visitors when they realized what kinds of opportunities our Identity Management technologies could bring to their environment; including, but not limited to, streamlining their infrastructure, cutting costs, and making it easier to support compliance.
At the end of the day, the RSA Security Conference 2015 was time well spent. Red Hat received a lot of positive feedback about our software, validated our strategic direction, and established a number of new contacts and partnerships.
I am really looking forward to going again next year. In the meantime, if you have questions or comments about Red Hat’s IdM offering - don’t hesitate to reach out using the comments section below.
