Ansible is a configuration management tool. While working with Ansible, you can create various playbooks, inventory files, variable files, etc. Some of the files contain sensitive and important data like usernames and passwords. Ansible provides a feature named Ansible Vault that prevents this data from being exposed. It keeps passwords and other sensitive data in an encrypted file rather than in plain text files. It provides password-based authentication.
[ Editor Note: Ansible Vault is one tool that one might use, but not necessarily what most sysadmins run in production. Red Hat Ansible Automation Platform is enterprise-grade and it can also work with existing tools that most enterprises have. ]
[ You might also enjoy: Handling secrets in your Ansible playbooks ]
Ansible Vault performs various operations. Specifically, it can
- Encrypt a file
- Decrypt a file
- View an encrypted file without breaking the encryption
- Edit an encrypted file
- Create an encrypted file
- Generate or reset the encrypted key
Create an encrypted file
The ansible-vault create command is used to create the encrypted file.
# ansible-vault create vault.yml
After typing this command, it will ask for a password and then ask where to put your content. To check that the file has been encrypted, use the cat command.

The following command is used to create encrypted files with --vault id.
# ansible-vault create --vault-id password@prompt vault.yml

Editing the encrypted file
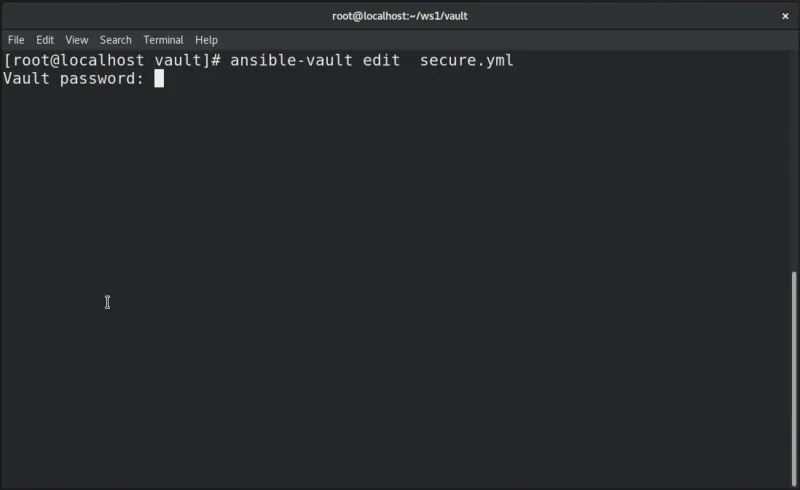
If the file is encrypted and changes are required, use the edit command.
# ansible-vault edit secure.yml

Decrypting a file
The ansible-vault decrypt command is used to decrypt the encrypted file.
# ansible-vault decrypt secure.yml

Decrypt a running playbook
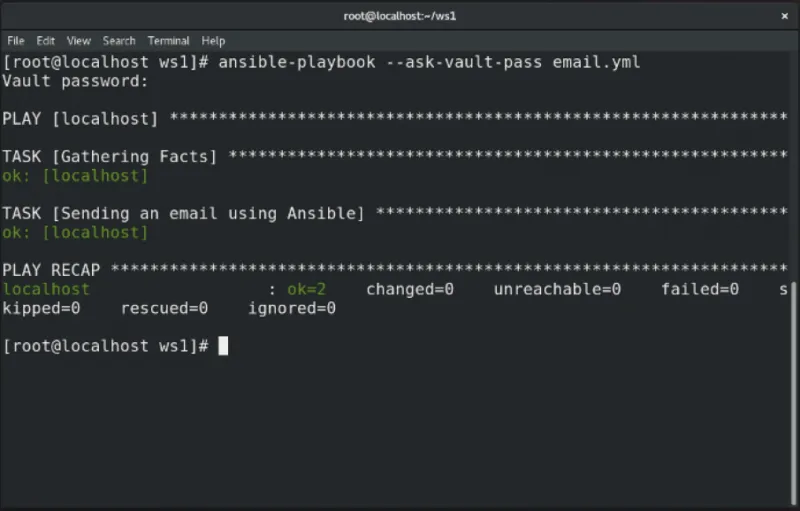
To decrypt the playbook while it is running, you usually ask for its password.
# ansible-playbook --ask-vault-pass email.yml
Reset the file password
Use the ansible-vault rekey command to reset the encrypted file password.

Here is the email.yml file contents:
---
- hosts: localhost
vars_files: secret.yml
tasks:
- name: Sending an email using Ansible
mail:
host: smtp.gmail.com
port: 587
username: 500069614@stu.upes.ac.in
password: "{{ p }}"
to: mrsarthak001@gmail.com
subject: Email By Ansible
body: Test successful
delegate_to: localhost
[ Need more on Ansible? Take a free technical overview course from Red Hat. Ansible Essentials: Simplicity in Automation Technical Overview. ]
Wrap up
In this article, you learned about Ansible Vault, which is an Ansible feature that helps you encrypt confidential information in a file without compromising security. You also learned about decrypting files, editing encrypted files, and resetting Ansible Vault passwords. This feature is especially useful if you have some confidential data that you want to secure and prevent from being publicly exposed.
Remember that Ansible Vault is generally viewed as a tool for junior-level sysadmins and is not considered to be enterprise-grade. For an enterprise solution, refer to Red Hat Ansible Automation Platform.
저자 소개
Sarthak Jain is a Pre-Final Year Computer Science undergraduate from the University of Petroleum and Energy Studies (UPES). He is a cloud and DevOps enthusiast, knowing various tools and methodologies of DevOps. Sarthak also Mentored more than 2,000 students Regarding the Latest Tech trends through their community Dot Questionmark.
채널별 검색
오토메이션
기술, 팀, 인프라를 위한 IT 자동화 최신 동향
인공지능
고객이 어디서나 AI 워크로드를 실행할 수 있도록 지원하는 플랫폼 업데이트
오픈 하이브리드 클라우드
하이브리드 클라우드로 더욱 유연한 미래를 구축하는 방법을 알아보세요
보안
환경과 기술 전반에 걸쳐 리스크를 감소하는 방법에 대한 최신 정보
엣지 컴퓨팅
엣지에서의 운영을 단순화하는 플랫폼 업데이트
인프라
세계적으로 인정받은 기업용 Linux 플랫폼에 대한 최신 정보
애플리케이션
복잡한 애플리케이션에 대한 솔루션 더 보기
가상화
온프레미스와 클라우드 환경에서 워크로드를 유연하게 운영하기 위한 엔터프라이즈 가상화의 미래
