Network controls and segmentation methods allow you to control, segregate, and visualize Kubernetes traffic. These methods help you isolate tenants and better secure communications flow between containerized applications and microservices.
August is “Network Controls” month in Red Hat’s monthly Security series! Since March 2021, the Red Hat Security Ecosystem team has published monthly articles and videos on DevOps Security topics to help you learn how Red Hat can help you master the practice called DevSecOps.
By explaining how to assemble Red Hat products and introducing our security ecosystem partners, we aim to aid in your journey to deploying a comprehensive DevSecOps solution.
Network controls defined
Network controls are typically implemented in a running Kubernetes cluster, and the goal is to provide a defense-in-depth approach to protect Kubernetes network traffic. The following security methods make up the Network Controls category:
-
CNI / SDN: Software-defined networking (SDN), which provides a programmable, adaptable network fabric that is provisioned in real-time to support dynamic networking security requirements and is typically implemented with a container networking interface (CNI).
-
Network Policies: control traffic flows at the IP address or port level, and can be enhanced with cluster ingress and egress traffic controls, logging and network visualization.
-
Ingress, Egress Traffic Controls: provide protection of network traffic within a running cluster between pods.
-
Hardening Service Mesh: includes network segmentation, authentication and authorization for containerized applications and microservices.
-
Network Visualization: provides a graphical user interface showing the network traffic and relationships in order to control and identify suspicious activity.
-
Packet Analysis: capturing live pod network traffic to typically debug issues in the communication between services.
-
API Management: controlling access to APIs and securing API traffic.
Network controls integrated in DevSecOps
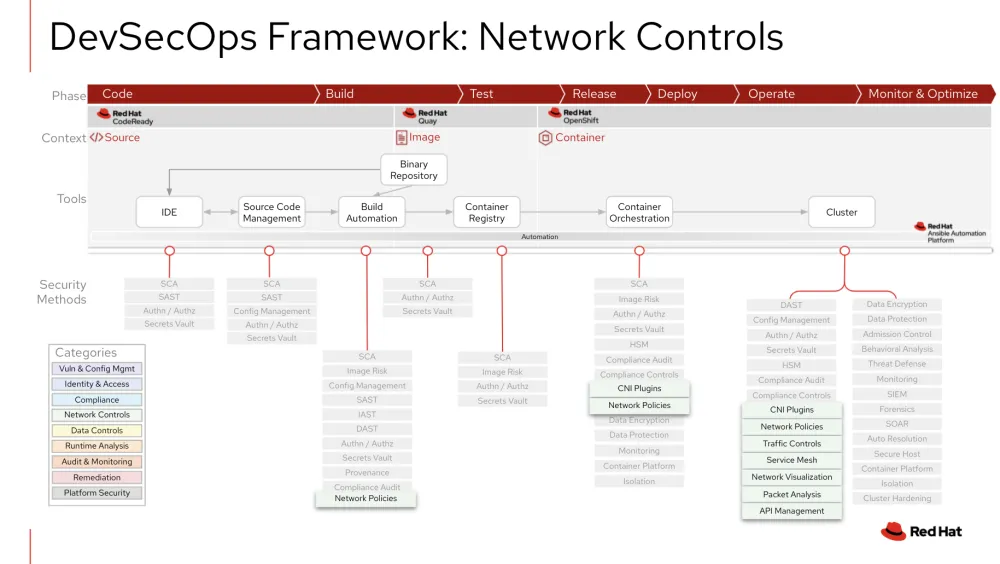
As pictured in the DevSecOps framework below, network controls integrations are typically found on the right side of the DevSecOps life cycle in a running cluster. The table that follows details some, but not all, of the common integrations to consider for network controls.
|
Integration Point |
Description |
|
Build Automation |
While most network controls are integrated in the running cluster, Kubernetes Network Policies provide an Infrastructure-as-code (IaC) approach to network configuration, which is key to adopting DevSecOps. Adding Network Policies within a GitOps and CI/CD process allows you to know who has access to what, audit changes and manage network policy drift. |
|
Container Orchestration |
Network Policies and CNI plugins help to set up Kubernetes networking during pod creation. |
|
Running Cluster |
Implementing network controls in the running cluster is the key integration for this category in order to achieve the defined features in each security method above. Some benefits include controlling access to endpoints outside of your Kubernetes cluster, automating compliance checks, monitoring all traffic within your cluster, and alerting on suspicious activity. Proper network controls configurations will also help provide a Zero Trust Architecture approach to networking, which assumes networks and network traffic is untrusted by default. Both Red Hat and our Security ISV Ecosystem provide capabilities in this category to add to a defense-in-depth approach to DevSecOps. |
Enhance and extend Network Controls with Red Hat partners
Combining Red Hat OpenShift Container Platform Network Control features with Red Hat’s certified ecosystem security partners can help your organization's DevSecOps practice.
If you are looking to enhance and extend Red Hat’s security capabilities in Network Controls, take a look at the following Red Hat Partners:
-
Aqua Security free trial and Operator.
-
Palo Alto Prisma Cloud Compute Edition and webinar.
-
Sysdig free trial and webinar.
-
Tigera Calico Enterprise and Operator.
For more information, visit "Modernize and secure applications with DevSecOps," or begin your discussion with us on enhancing container security and adopting DevSecOps. For similar blog posts on Red Hat’s DevSecOps Framework, search for previous months’ categories (Data Controls, Compliance, Identity and Access and Application Analysis) and stay tuned for upcoming posts.
저자 소개
Dave Meurer currently serves as a Principal Solution Architect on the Red Hat Global Partner Security ISV team, where he owns technical relationships and evangelism with security independent software vendor partners of Red Hat. Before joining Red Hat, he spent nine years in the Application Security industry with Synopsys and Black Duck, where he served in similar roles as the director of technical alliances and sales engineering.
Meurer also worked for Skyway Software, HSN.com, and Accenture in various management and application development roles. When he’s not thinking about Kubernetes, security, and partners, he enjoys being the VP Sales of North Central Tampa for his wife (the CEO) and 5 kids (Inside Sales).
유사한 검색 결과
What’s new in post-quantum cryptography in RHEL 10.1
Introducing OpenShift Service Mesh 3.2 with Istio’s ambient mode
Data Security And AI | Compiler
Data Security 101 | Compiler
채널별 검색
오토메이션
기술, 팀, 인프라를 위한 IT 자동화 최신 동향
인공지능
고객이 어디서나 AI 워크로드를 실행할 수 있도록 지원하는 플랫폼 업데이트
오픈 하이브리드 클라우드
하이브리드 클라우드로 더욱 유연한 미래를 구축하는 방법을 알아보세요
보안
환경과 기술 전반에 걸쳐 리스크를 감소하는 방법에 대한 최신 정보
엣지 컴퓨팅
엣지에서의 운영을 단순화하는 플랫폼 업데이트
인프라
세계적으로 인정받은 기업용 Linux 플랫폼에 대한 최신 정보
애플리케이션
복잡한 애플리케이션에 대한 솔루션 더 보기
가상화
온프레미스와 클라우드 환경에서 워크로드를 유연하게 운영하기 위한 엔터프라이즈 가상화의 미래
