This is a guest post by nCipher's senior sales engineer, Oli Wade.
The purpose of the blog is to introduce you to incorporating high assurance cryptographic security with hardware security modules (HSMs) into your Red Hat OpenShift projects. Since this might be new territory for some in the developer community, I’ll take a moment to explain what an HSM is.
An HSM is a specialized hardware device that is designed for the purpose of protecting encryption keys and conducting cryptographic processes such as creating digital signatures. Keys are generated according to strict security standards and based on an internal high-quality entropy source. HSMs are robust, tamper-resistant devices that incorporate innovative security features to ensure the protection of sensitive key material.
The alternative to using an HSM is to store encryption keys in software – which can be risky since skilled attackers can identify critical key material based on its unique, random characteristics. High value keys should be protected to the best achievable standards, since their loss might cause considerable financial and reputational damage – as well as a compliance violation. HSMs provide this protection and many are certified to internationally-recognized standards like FIPS 140-2 and Common Criteria, while also being recognized by security auditors as an effective tool to mitigate cyber risk.
Applications in a containerized architecture are built, deployed and operated with contemporary methods including orchestration and dynamic scalability. These advancements bring challenges when it comes to including integration with HSMs, in a way that is compatible with this type of modern workflow. This is because applications that rely on HSMs historically require installation of special supporting software and libraries, plus manual configuration of both the server and the HSM to enable secure connections to be made between them.
Now, thanks to the integration of nCipher nShield HSMs with OpenShift, it is possible to easily incorporate highly scalable crypto operations into your containerized application architecture.
Before discussing how to integrate nShield HSMs with OpenShift, it may be instructive to consider visually where the HSM fits in the context of the OpenShift platform:
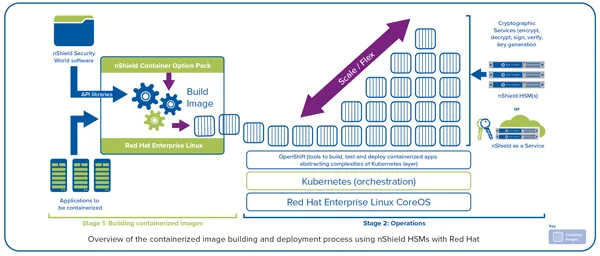
As depicted in the diagram above, the nShield HSM is an external component accessed over the network. It provides highly available and scalable certified crypto offload for protecting valuable key material – so that it is never exposed within the containerized architecture or platform (where it might be observed or captured by systems administrators).
Building Container Images
Implementing cryptographic operations to enhance application security can be complex. Developers benefit from tools which make this task easier, and that provide an approved reference architecture to follow. Therefore, nCipher provides a set of standard scripts that enable supported integration with and connection to certified nShield HSMs in a streamlined and repeatable way. This reduces development times while using a tested process for delivering high assurance application security.
With these scripts, application developers can easily include the necessary nShield libraries for use with their PKCS11 or Java programs inside container images. Alternatively, off-the-shelf container images provided by third parties can be extended to include such libraries to enable their use with nShield HSMs. Typically this would form part of a CI/CD (continuous integration, delivery and deployment) pipeline so as to allow new versions or iterations of applications to be created with the same capabilities integrated.
Another container image is built with the nShield hardserver to enable and manage the connection to one or more nShield HSMs. These standardized images are stored in the normal enterprise container registry, and can be launched into any compatible container runtime.
Running Containerized Applications in OpenShift
One or more application containers are deployed into a pod alongside an instance of the hardserver container. The latter is supplied with details of the nShield HSM(s) to connect to (which can be in private or co-located hosting, or nShield as a service); while the application containers mount the corresponding Security World files from suitable persistent volume storage. Security World is nShield’s unique key management architecture, which establishes a logical security boundary for deploying and operating a group of nShield HSMs. This ensures interoperability across the organization’s HSM estate and affords rapid scalability.
Different applications and/or versions of the same application can share HSMs in the same Security World, making use of the same or their own application keys – which can be permanent or temporary depending on the volume/storage mapping configured.
nShield HSMs can support OpenShift development at any scale and with flexible or dynamic provisioning. Rather than upgrading servers or virtual machines, new application versions are deployed typically alongside and then instead of older versions with traffic distributed using included or external load balancers.
Increased application security
Using the nShield container option pack with Red Hat OpenShift, developers and operations teams can easily integrate their new or existing applications with nShield HSMs in a way that is straightforwardly accessible from contemporary containerized deployments. There is no need to install or configure software and appliances, meaning a much faster “time-to-security.” Instead of leaving potentially valuable application keys vulnerable, they are safely generated and used only within the HSM’s protected and certified boundary.
nShield HSMs are also highly scalable, which make them a good companion for use with large or dynamically deployed containerized application architectures and allows developers to increase capacity with confidence. For implementations leveraging the subscription-based nShield-as-a-Service, the maintenance and management of the HSM itself is offloaded from the IT team.
The integration of the nCipher nShield with Red Hat OpenShift enables projects to be implemented with a new level of security that delivers the scale and flexibility needed for today’s enterprise applications.
저자 소개
Red Hatter since 2018, technology historian and founder of The Museum of Art and Digital Entertainment. Two decades of journalism mixed with technology expertise, storytelling and oodles of computing experience from inception to ewaste recycling. I have taught or had my work used in classes at USF, SFSU, AAU, UC Law Hastings and Harvard Law.
I have worked with the EFF, Stanford, MIT, and Archive.org to brief the US Copyright Office and change US copyright law. We won multiple exemptions to the DMCA, accepted and implemented by the Librarian of Congress. My writings have appeared in Wired, Bloomberg, Make Magazine, SD Times, The Austin American Statesman, The Atlanta Journal Constitution and many other outlets.
I have been written about by the Wall Street Journal, The Washington Post, Wired and The Atlantic. I have been called "The Gertrude Stein of Video Games," an honor I accept, as I live less than a mile from her childhood home in Oakland, CA. I was project lead on the first successful institutional preservation and rebooting of the first massively multiplayer game, Habitat, for the C64, from 1986: https://neohabitat.org . I've consulted and collaborated with the NY MOMA, the Oakland Museum of California, Cisco, Semtech, Twilio, Game Developers Conference, NGNX, the Anti-Defamation League, the Library of Congress and the Oakland Public Library System on projects, contracts, and exhibitions.
유사한 검색 결과
What’s new in post-quantum cryptography in RHEL 10.1
Introducing OpenShift Service Mesh 3.2 with Istio’s ambient mode
Data Security And AI | Compiler
Data Security 101 | Compiler
채널별 검색
오토메이션
기술, 팀, 인프라를 위한 IT 자동화 최신 동향
인공지능
고객이 어디서나 AI 워크로드를 실행할 수 있도록 지원하는 플랫폼 업데이트
오픈 하이브리드 클라우드
하이브리드 클라우드로 더욱 유연한 미래를 구축하는 방법을 알아보세요
보안
환경과 기술 전반에 걸쳐 리스크를 감소하는 방법에 대한 최신 정보
엣지 컴퓨팅
엣지에서의 운영을 단순화하는 플랫폼 업데이트
인프라
세계적으로 인정받은 기업용 Linux 플랫폼에 대한 최신 정보
애플리케이션
복잡한 애플리케이션에 대한 솔루션 더 보기
가상화
온프레미스와 클라우드 환경에서 워크로드를 유연하게 운영하기 위한 엔터프라이즈 가상화의 미래
