Vulnerability and patch management can be time-consuming and painful. Standard practices for vulnerability management rely on scanning for vulnerabilities and rescanning to confirm that patches have been applied. Unfortunately, this can lead to false positives and can be time consuming. In this post we will discuss how Red Hat Insights complements vulnerability management processes by providing deeper visibility to the risks associated with vulnerabilities based on your environment.
Not only does Red Hat Insights identify vulnerabilities but it prioritises them based on any mitigations already in place and gives immediate validation when a patch is applied. This additional validation can serve as defense in depth security strategy, as Insights helps you monitor policy, identify vulnerabilities and validate that appropriate mediations are in place remediation.
What is defense-in-depth?
NIST defines defense-in-depth as “the application of multiple countermeasures in a layered or stepwise manner to achieve security objectives. The methodology involves layering heterogeneous security technologies in the common attack vectors to ensure that attacks missed by one technology are caught by another.”
Unfortunately in many cases, defense-in-depth can lead to complexity for the IT and security teams responsible for protecting the environment. As organizations grow in complexity they rely on a multitude of tools to improve security and provide vulnerability management.
For many, the key features of a risk management tool are the ability to analyze systems to identify risk and accelerate processes for remediation. Expertise is critical to evaluate risk and determine the right course of action from a set of alternatives.
Another challenge is having certainty that the tools are reliable and up-to-date before incurring any down-time for updates, which is not always the case in third party tools. As we've discussed on the blog before, assessing real risk is harder than just looking at a CVE. Third party tools may simply look at version numbers to flag vulnerabilities, which may be inaccurate when vendors like Red Hat backport fixes.
How can you be sure that you and your teams have the most current recommendations for handling vulnerabilities, patching procedures and risk management? As we discuss in the Risk Management eBook, add “vendor-specific expertise” to your requirements. Having the latest information and guidance from operating system and application vendors can save time and money and reduce your risk exposure.
Prioritization: Patching? Protecting? Profits?
The goal is not only to identify vulnerabilities but assess the risk to particular environments. While patching may seem the most straightforward solution, IT knows there is never enough time to patch everything.
Therefore, incorporating local expertise, expertise from the vendor, and weighing the mitigation options available to avoid downtime and business interruption is necessary. In some cases, patching can be postponed if the appropriate security rules can be put into effect.
Many organizations rely on external tools to help them convert vulnerability information into actionable recommendations for remediation. The ideal vulnerability management tool streamlines the decision-making processes.
Organizations are turning from scanning tools that look for vulnerabilities to more sophisticated observability platforms for their risk management. These types of tools are essential to scan and manage vulnerabilities across platforms. It is important to incorporate a scanner into your “Defense in Depth” strategy and most do so as a matter of best practice.
Another way to look at risk is as the intersection of Vulnerability severity with a particular asset’s criticality combined with potential network exposure leads to a more exact risk determination. Risk is situation and environment dependent. Critical vulnerabilities can require differing remediation depending on the particular risk scenario. The scanning tools typically can provide only vulnerability severity. In contrast, Insights can look across your environment and incorporate your security rules and policies to determine a more granular level of risk.
Avoiding false negatives
But have you ever applied a patch, only to be told by your scanning tool that the vulnerability is still there? Third-party tools often do not have the latest information or the updated capabilities to recognize that a patch has been successfully applied. This can lead to second-guessing, rework and to additional documentation for compliance and change management processes, all of which take time.
This is one of the many scenarios where Red Hat Insights reflects the extensive Red Hat vendor knowledge and experience with the Red Hat Enterprise Linux (RHEL) platform for which it was built. Red Hat Insights is an operational and business efficiency and security risk management solution that provides continuous, in-depth analysis of registered Red Hat Enterprise Linux systems. It is included in your Red Hat Enterprise Linux subscription. Some users have referred to Insights as "like having an extra pair of eyes." Red Hat Insights serves as another layer for your defense in depth strategy. Red Hat Insights enables users to obtain actionable intelligence regarding their RHEL environments, helping to identify and address operational, business and vulnerability risks before an issue results in downtime.
Planning is better than just scanning
Juggling the priorities of security and performance is always more difficult for mission-critical applications like SAP and SQL. Red Hat Insights provides advice on improving performance and addressing vulnerabilities with a holistic view of your entire operations.
The predictive analytics across many Red Hat Linux users helps you detect configuration problems that may otherwise go unnoticed until performance or availability is affected. In addition, there are security rules and other recommendations that Red Hat Insights can recommend. A critical vulnerability may be categorized as low risk in some systems based on the security rules that are configured but may be high for other systems. This granularity is accomplished by looking beyond the package and analyzing the configuration of the individual hosts.
Red Hat Insights can help provide you the granularity you need to decide what takes priority, what to patch and when. With Red Hat Insights you are able to go beyond just scanning and to start planning how to make continuous improvements to your systems to optimize your investment and achieve the performance you need without sacrificing security.
Behind the scenes
Scanners are not typically designed to perform the deep threat analytics that allows technology like Red Hat Insights to provide an additional layer of defense. Red Hat Insights can look deeper, “under the covers'' beyond just a version number. It checks the host’s configuration parameters. Additional capabilities within Red Hat Insights enables you to check and monitor against your own internal policies or industry-standard best practices for compliance.
With Red Hat Insights delivered as a service, there is no additional infrastructure needed and you can easily enroll and know that it is always on. A limited and controlled set of system metadata is required but you can control what is sent to the Red Hat Insights for analysis. Learn more about how Red Hat Insights security posture and how we safeguard your system data.
Diagnose and remediate what, when, and how you want
Insights serves as a diagnostic tool that is always on. Unlike a scanner, it has access only to those systems for which it is specifically configured. Red Hat has put security measures in place to protect the heartbeat of your systems and to help reduce security risks when transmitting, processing, and analyzing the metadata that your systems share with Red Hat.
Insights gets to work not only identifying vulnerabilities but also providing your team with various options that you can take to remediate your systems and reduce risk as soon and as easily as possible. Red Hat Insights provides intelligent choices to maximize security, operational efficiency and keep your business critical systems up and running.
The value of Insights can be seen with the Sudo vulnerability, which can lead to a privilege escalation. With Insights, you can detect and prioritize which systems are vulnerable. In addition it can help you to discern those systems that are running vulnerable software but aren’t at a high risk from the sudo vulnerability and therefore don’t need to be patched immediately if ever depending on your configuration.
You can see how Insights works and Diagnose sudo with Insights (only for those that are already registered). More information about sudo via "Privilege escalation via command line argument parsing - sudo - (CVE-2021-3156)".
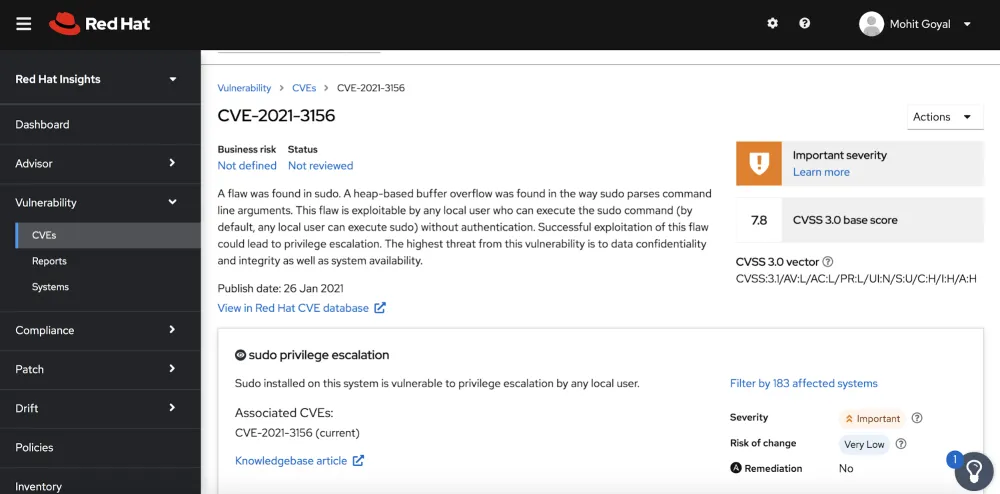
A new security rule that has been written by Red Hat Product Security for the "Sudo vulnerability" which helps us to determine whether or not this specific vulnerability impacts a Red Hat Enterprise Linux system beyond just looking at the OS version. This is an example where Insights has differentiated and higher value than the typical scanning tool.
A vulnerability does not always equate to risk. Details on Red Hat severity ratings is useful for guiding decisions. Insights provides the granular details for each system. This immediately helps system administrators make the right decisions for what to patch. For enterprises with hundreds of systems, making decisions with knowledge-based patching strategies can lead to significant operational savings in staff time and downtime.
Crawl, walk, automate, soar
Red Hat automation solutions streamline IT administration. Automation can not only save time but it can make your environment more secure, optimized, and reliable. Another key benefit of automation is reducing human error.
Once you register Red Hat Insights, you will receive recommendations based on your risk profile and policies. Many of these recommendations will have associated Ansible playbooks that you can immediately use and feed to automation tools.
If you need to manage thousands of distributed systems across multiple datacenters and in the cloud — you can fix issues with a click of a button by integrating Insights with Red Hat Smart Management. If you need to coordinate across multiple global teams and multiple infrastructure vendors, Red Hat Ansible Automation Platform provides an efficient, streamlined solution to automate security practices and bring together the different tools used in security activities across a variety of platforms. Both of these solutions provide you with the appropriate levels of security oversight, notifications and approvals. Both will streamline your processes to not only address vulnerabilities faster but make patching at scale easier while assuring that you remain in compliance and follow change management procedures.
Go deep with Red Hat Insights
Many customers including financial institutions and governments across all geographies have adopted Insights as part of their defense in depth strategy. Red Hat Insights is already part of your Red Hat Enterprise Linux subscription so you can get started immediately. It provides not only recommendations but confidence that patching procedures were successful.
The goal of Insights is to provide immediate access to vulnerability information and provide options for customers based on their risk tolerance and IT maturity. The range of services keeps growing to include Vulnerabilities and Compliance services. Whatever tools you have in place today, Red Hat Insights can complement your tools, integrate into your existing workflow, and provide additional flexibility. So dive deeper and learn more about how to use Red Hat Insights as part of your defense in depth strategy.
저자 소개
Mary Roark is a Principal Product Manager for Red Hat Insights as well as a Certified Information Systems Security Professional (CISSP). Roark has held leadership positions in international technology marketing at companies like Microsoft, RSA Security, Sophos and security startups. Roark has a bachelor's degree in Electrical Engineering from the University of Arizona (Go Wildcats!) and an MBA from the Stern School of Business, New York University.
채널별 검색
오토메이션
기술, 팀, 인프라를 위한 IT 자동화 최신 동향
인공지능
고객이 어디서나 AI 워크로드를 실행할 수 있도록 지원하는 플랫폼 업데이트
오픈 하이브리드 클라우드
하이브리드 클라우드로 더욱 유연한 미래를 구축하는 방법을 알아보세요
보안
환경과 기술 전반에 걸쳐 리스크를 감소하는 방법에 대한 최신 정보
엣지 컴퓨팅
엣지에서의 운영을 단순화하는 플랫폼 업데이트
인프라
세계적으로 인정받은 기업용 Linux 플랫폼에 대한 최신 정보
애플리케이션
복잡한 애플리케이션에 대한 솔루션 더 보기
가상화
온프레미스와 클라우드 환경에서 워크로드를 유연하게 운영하기 위한 엔터프라이즈 가상화의 미래