Davie Street Enterprises (DSE) continues its digital transformation journey. After transforming the culture, standardizing and automating the IT infrastructure, deploying a middleware strategy, and deploying its cloud strategy, DSE is beginning to shift towards DevOps. This is where DSE can leverage the cultural changes implemented within its development and operations teams to release features faster than the competition, using container technology.
To launch DevOps into production, DSE is holding itself accountable for ensuring security is integrated into the culture and process. Security has been the top priority for DSE ever since its 2020 website outage, which involved a security breach among other factors. Security has now almost grinded DSE’s traditional development cycles to a halt, so this transformation over to DevOps couldn’t have come at a better time.
Susan Chin, Senior Director of Development, and Ranbir Ahuja, Senior Director IT Operations, are leading the effort to shift development towards DevOps, but don’t have the expertise to ensure security is tightly integrated and comprehensive in the process. Therefore, Monique Wallace, the CIO, has promoted Zachary L. Tureaud from the Security Operations team to lead this critical effort. Tureaud has been at DSE for five years and spent all of his time on the Security Operations team responsible for threat detection and remediation. Instituting a security culture
The first order of business for Tureaud was to get in front of the DevOps shift and ensure the correct security culture was established and built in to the hard work the teams were doing. Chin and Ahuja were more than happy to welcome Tureaud’s ideas to meet DSE’s security requirement. To kickstart a security-minded culture, Tureaud laid out the following guiding principles for the DevOps teams:
-
Adopt a “you code it, you own it” philosophy to security.
-
Designate a security champion for each DevOps team.
-
Train developers on secure coding practices.
-
Focus on Critical & High vulnerabilities.
-
Automate security without sacrificing speed and agility.
-
Define and Measure security goals throughout the lifecycle.
With security now embedded into the DevOps culture, Tureaud can turn his attention to the technology and ensure all the appropriate security controls and tooling are in place. From his experience, Tureaud knew Red Hat OpenShift is a certified Kubernetes distribution that could provide DSE with an out-of-the-box, secure-by-design platform. He also understands that Red Hat has a rich partner ecosystem with hundreds of certified integrations, which allows him to build a comprehensive DevSecOps solution with some of DSE’s current security tools already deployed. This will greatly increase the adoption of security controls within the DSE DevOps teams.
Red Hat OpenShift: Secure-by-design Kubernetes platform
Luckily, Tureaud didn’t have to worry about adding key foundational security controls to DSE’s Kubernetes implementation because Red Hat OpenShift already contained the controls he needed. Some of the foundational security features included:
-
SELinux: One of Tureaud ’s favorite Red Hat Enterprise Linux (RHEL) features is SELinux. Keeping SELinux enabled is key in achieving defense in depth, especially for zero day vulnerabilities. It’s basically done by enforcing a labeling system that provides mandatory access controls on every process and operating system objects. For example, if a container process hacked into the host system and tried to write a file in root somewhere, SELinux would prevent the write because the container process has a different label than the file object in the root directory. Tureaud didn’t need to configure anything to get this type of protection because SELinux is on by default in Red Hat OpenShift’s operating systems.
-
Runtime security policies: One of the ways SELinux can be seen by default is through Red Hat OpenShift’s runtime security policy feature called Security Context Constraints (SCCs). SCCs control permissions for pods by defining a set of conditions that a pod must run under in order for it to be accepted into the cluster. SCCs ultimately limit the ability of the container to negatively impact the infrastructure or other containers.
-
Container optimized operating system: One of Red Hat OpenShift’s key security features is an operating system optimized for containers, called RHEL CoreOS. RHEL CoreOS is an immutable, self-updating operating system, booted from container images, and contains only the packages needed to run Red Hat OpenShift.
-
Hardening and compliance guides: Due to regulatory compliance, Tureaud will need to further harden DSE’s clusters and meet certain compliance requirements, like PCI. Coincidentally, Red Hat has a handful of guides that were easy for Tureaud to find online that help for things like PCI-DSS and CIS Benchmarks.
-
IAM & RBAC: Authentication, or identity and access management, is yet another one of the added services Red Hat OpenShift provides on top of Kubernetes. It comes with a built-in OAuth server, which (by using a configured identity provider) handles the user authentication to Red Hat OpenShift through an access token. Authorization, which is handled by Role Based Access Controls (RBAC), determines whether a user is allowed to perform a given action, like creating a pod within a project. It’s made up of rules, which are the actions or verbs permitted on an object. The collection of those rules make up roles, which are mapped to users or groups with bindings. RBAC is enabled by default in Red Hat OpenShift.
-
Service mesh: Due to DSE’s transition to DevOps and more of a microservices architecture, Tureaud will be leveraging Red Hat OpenShift’s service mesh feature, which is based on the open source project, Istio. Service mesh provides even more security benefits, including policy driven security, encryption of east/west traffic, as well as distributed tracing, visualization and monitoring.
Red Hat ecosystem: Partners extend and enhance Red Hat functionality
Tureaud has been to several Red Hat Security webinars recently, including a series in late 2020 about DevSecOps, where he learned about the rich ecosystem of partners that complement Red Hat technologies and provide a comprehensive DevSecOps solution for DSE. These partners not only extend and enhance Red Hat functionality, but are certified in technologies such as containers, operators, and vulnerability scanning.
However, understanding where each partner fits into DSE’s DevSecOps solution isn’t a straightforward task. The good news is that Red Hat has worked with Tureaud to lay out a DevSecOps solution starting from a framework consisting of nine security categories and 32 security methods that are all mapped to integration points in a DevOps lifecycle. This allows DSE and Red Hat to have the appropriate conversations regarding where DSE may look to Red Hat’s ecosystem to extend and enhance Red Hat functionality. For example, Red Hat has DSE covered with platform security and certain pieces of network controls, and Red Hat’s partners can enhance the solution in the areas of application analysis, identity and access, and runtime analysis.
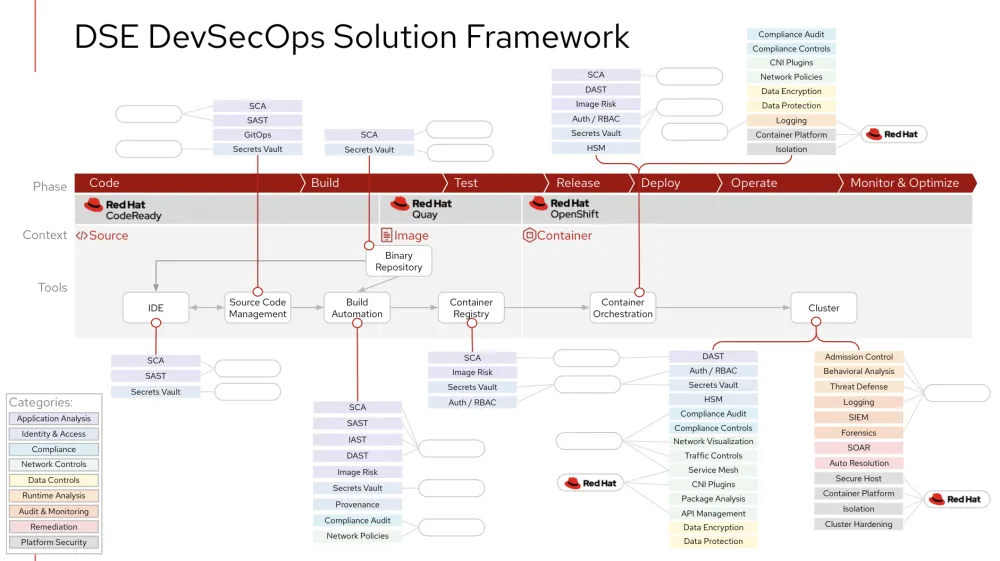
When Tureaud was promoted to this new position, Wallace tasked him with looking at DSE’s current security vendors to leverage their existing investments in this new DevSecOps solution. With that in mind, Red Hat helped Tureaud put together the following table to identify the capabilities of their current vendors and new vendors which fill in the gaps:
| Vendor | Status | Security Methods |
|---|---|---|
|
Red Hat |
existing |
Application Analysis: GitOps Network Controls: Service Mesh, CNI Plugins, API Management Data Controls: Data Encryption Platform Security: Secure host, container platform, isolation, cluster hardening. |
|
Synopsys |
existing |
Application Analysis: SCA, SAST, IAST, DAST |
|
CyberArk |
new |
Identity & Access: Secrets vault |
|
Sysdig |
new |
Compliance Audit and Controls Network Controls: Network policies, network visualization, traffic controls, service mesh (hardening) Runtime Analysis: Runtime protection, behavioral analysis, threat defense, logging Audit & Monitoring: Logging, forensics |
Once each vendor’s security methods were known, the next step was to map each vendor to the Red Hat DevSecOps framework to create a solution. This simple, yet insightful, diagram will serve as the foundation to implement the technology required for a comprehensive DevSecOps solution at DSE.
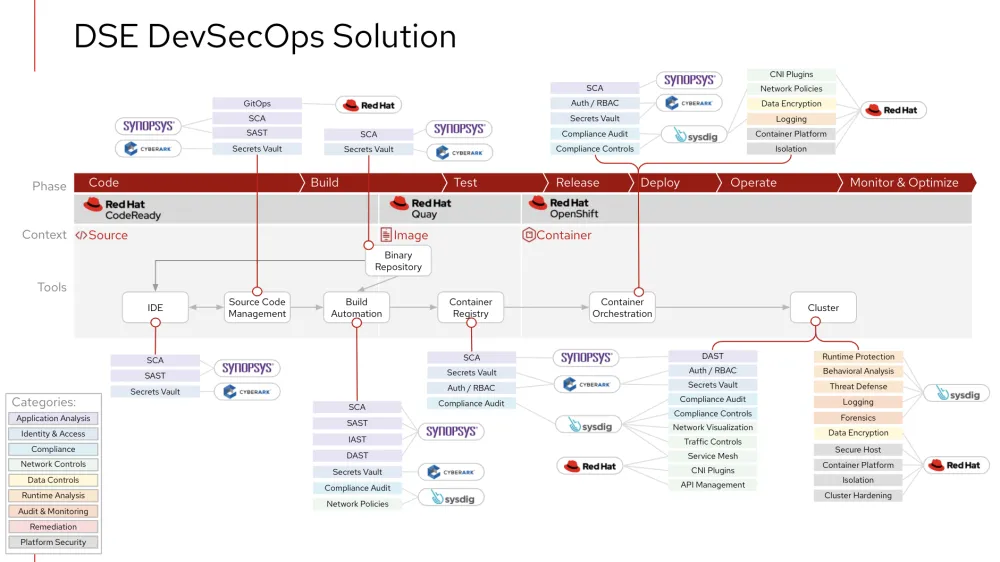
Conclusion
DevOps practices can help organizations deploy containerized applications faster. DSE needed that advantage to keep ahead of its competition in the manufacturing plant industry, but was halted by security concerns. Red Hat helped weave security into the entire DevOps lifecycle, starting with culture, then tackling technology through Red Hat OpenShift and extending and enhancing the features with Red Hat’s Security Ecosystem. To learn more about Red Hat’s work in the previous phases and to see the latest developments of DSE’s digital transformation, visit this page.
저자 소개
Dave Meurer currently serves as a Principal Solution Architect on the Red Hat Global Partner Security ISV team, where he owns technical relationships and evangelism with security independent software vendor partners of Red Hat. Before joining Red Hat, he spent nine years in the Application Security industry with Synopsys and Black Duck, where he served in similar roles as the director of technical alliances and sales engineering.
Meurer also worked for Skyway Software, HSN.com, and Accenture in various management and application development roles. When he’s not thinking about Kubernetes, security, and partners, he enjoys being the VP Sales of North Central Tampa for his wife (the CEO) and 5 kids (Inside Sales).
유사한 검색 결과
Red Hat to acquire Chatterbox Labs: Frequently Asked Questions
From incident responder to security steward: My journey to understanding Red Hat's open approach to vulnerability management
What Is Product Security? | Compiler
Technically Speaking | Security for the AI supply chain
채널별 검색
오토메이션
기술, 팀, 인프라를 위한 IT 자동화 최신 동향
인공지능
고객이 어디서나 AI 워크로드를 실행할 수 있도록 지원하는 플랫폼 업데이트
오픈 하이브리드 클라우드
하이브리드 클라우드로 더욱 유연한 미래를 구축하는 방법을 알아보세요
보안
환경과 기술 전반에 걸쳐 리스크를 감소하는 방법에 대한 최신 정보
엣지 컴퓨팅
엣지에서의 운영을 단순화하는 플랫폼 업데이트
인프라
세계적으로 인정받은 기업용 Linux 플랫폼에 대한 최신 정보
애플리케이션
복잡한 애플리케이션에 대한 솔루션 더 보기
가상화
온프레미스와 클라우드 환경에서 워크로드를 유연하게 운영하기 위한 엔터프라이즈 가상화의 미래
