The Red Hat Advanced Cluster Security for Kubernetes team continues to build on its 4.0 release earlier this year, with a user-driven release in Red Hat Advanced Cluster Security 4.3. This release focuses on supporting even more Kubernetes platforms, and delivers better vulnerability reports, while onboarding users quickly and more. The Red Hat Advanced Cluster Security 4.3 release notes contain the many updates, depreactions and removal of features in the product.
Take a look at the updates in Red Hat Advanced Cluster Security 4.3:
- Vulnerability reporting 2.0 is generally available
- Watch and scan images in Vulnerability Management 2.0
- Increased support for hardware and software
- Scan local image registries by using the roxctl CLI
- Easily invite users to your Red Hat Advanced Cluster Security instance
As always, you can try out the latest version of Red Hat Advanced Cluster Security with the 60 day, no cost trial of Red Hat Advanced Cluster Security Cloud Service.
Vulnerability Reporting 2.0 is generally available
The team is excited to announce that the Vulnerability Reporting option under the Vulnerability Management menu is now generally available. This vulnerability reporting capability upgrade builds on the release of Red Hat Advanced Cluster Security 4.0 and the Vulnerability Management 2.0 dashboard.
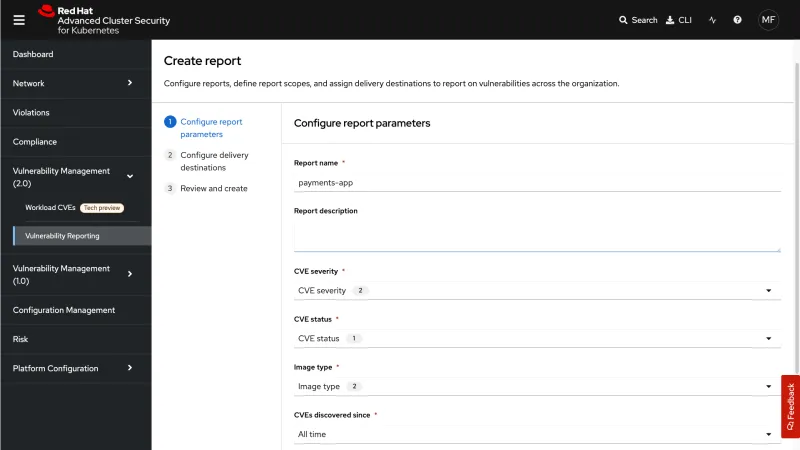
The reporting options enable security teams to send weekly or monthly updates to groups with collections based on the apps and services they develop and maintain. There are several enhancements, including the ability to customize email templates and on-demand send of vulnerability reports. For more information, see “Vulnerability Reporting.”

One thing to note! All reports created in the Vulnerability Management 1.0 reporting page are automatically migrated to the Vulnerability Management 2.0 menu. For more information, see “Migration of vulnerability reports when upgrading to RHACS version 4.3 and later.”
Watch and scan images in Vulnerability Management 2.0
Red Hat Advanced Cluster Security prioritizes container images that are being used in your cluster. However, some container images have a short lifespan or are used periodically. Red Hat Advanced Cluster Security has been able to mark an image as “watched” so that vulnerability scans can always be completed regardless of whether the image is used in an active deployment.

This functionality has been migrated from Vulnerability Management 1.0 to Vulnerability Management 2.0. For more information, see “Scanning inactive images.”
Increased support for hardware and software
Red Hat Advanced Cluster Security continues to help our customers secure their hosts, platform and container workloads. This means supporting a wide range of Kubernetes versions for our Central and Secured Cluster services.
With 4.3, we’re announcing support for the following hardware and software:
- Red Hat Advanced Cluster Security secured clusters for Red Hat OpenShift on IBM Cloud
- Red Hat Advanced Cluster Security Central on IBM Power and IBM Z
- Red Hat Advanced Cluster Security support for Red Hat OpenShift Service on AWS with hosted control planes (ROSA with HCP)
- Support for Red Hat OpenShift 4.14
For more information, see “Supported platforms and installation methods.”
Scan local image registries by using the roxctl command line interface (CLI)
Red Hat Advanced Cluster Security first enabled scanning locally and in the pipeline with the roxctl CLI. We are taking it further and enabling users to scan images stored in image registries, including cluster local registries such as the OpenShift integrated image registry.
For more information, see “Image scanning using the roxctl CLI.”
NEW! Red Hat Advanced Cluster Security Event Log Viewer
We’ve added a UI section to easily filter through the Red Hat Advanced Cluster Security events:

Easily invite users to your Red Hat Advanced Cluster Security instance
Security dashboards are only as powerful as your ability to share them with your team. With Red Hat Advanced Cluster Security, you can invite multiple new users with a simple email.

As always, you can define your user's roles to simplify accurate access control and improve the security of your Red Hat Advanced Cluster Security instance.
For more information, see “Inviting users to your RHACS instance.”
Try Red Hat Advanced Cluster Security 4.3 at no cost today!
Red Hat Advanced Cluster Security Cloud Service makes getting started a breeze and comes with a 60-day, no cost trial. Sign up and get hands-on with Red Hat Advanced Cluster Security today!
Sobre o autor
Michael Foster is a CNCF Ambassador, the Community Lead for the open source StackRox project, and Principal Product Marketing Manager for Red Hat based in Toronto. In addition to his open source project responsibilities, he utilizes his applied Kubernetes and container experience with Red Hat Advanced Cluster Security to help organizations secure their Kubernetes environments. With StackRox, Michael hopes organizations can leverage the open source project in their Kubernetes environments and join the open source community through stackrox.io. Outside of work, Michael enjoys staying active, skiing, and tinkering with his various mechanical projects at home. He holds a B.S. in Chemical Engineering from Northeastern University and CKAD, CKA, and CKS certifications.
Mais como este
Friday Five — January 9, 2026 | Red Hat
Accelerating success with the Red Hat Partner Program
Technically Speaking | Build a production-ready AI toolbox
AI Is Changing The Threat Landscape | Compiler
Navegue por canal
Automação
Últimas novidades em automação de TI para empresas de tecnologia, equipes e ambientes
Inteligência artificial
Descubra as atualizações nas plataformas que proporcionam aos clientes executar suas cargas de trabalho de IA em qualquer ambiente
Nuvem híbrida aberta
Veja como construímos um futuro mais flexível com a nuvem híbrida
Segurança
Veja as últimas novidades sobre como reduzimos riscos em ambientes e tecnologias
Edge computing
Saiba quais são as atualizações nas plataformas que simplificam as operações na borda
Infraestrutura
Saiba o que há de mais recente na plataforma Linux empresarial líder mundial
Aplicações
Conheça nossas soluções desenvolvidas para ajudar você a superar os desafios mais complexos de aplicações
Virtualização
O futuro da virtualização empresarial para suas cargas de trabalho on-premise ou na nuvem
