Este es el primero de una serie de dos artículos. Aquí, damos un paso atrás y analizamos el panorama cambiante de los riesgos de seguridad de la TI y la manera en la que incide en las empresas. Luego, analizaremos una arquitectura sugerida de cumplimiento normativo automatizado. En la segunda parte, demostraremos el funcionamiento de la arquitectura mencionada cuando se utilizan Red Hat Insights y Red Hat Ansible Automation Platform.
Cualquier persona que haya tenido un vehículo o haya estado en uno probablemente haya visto aparecer al menos uno o más símbolos en el tablero. Allí aparecen indicaciones de que surgió un problema que requiere atención. Muchas veces, se ha visto que cuando no se aborda un problema, el propietario del vehículo debe invertir más tiempo y energía en solucionarlo, lo cual aumenta su nivel de estrés. ¿Vale la pena correr el riesgo de enfrentar estas consecuencias por no encargarse rápidamente de las advertencias y los avisos cuando aparecen, antes de que se conviertan en un problema?
A la hora de cumplir con los requisitos normativos y de seguridad, Red Hat funciona como su tablero de conducción y como su mecánico con Insights y Ansible Automation Platform, lo que le permite mantenerse a la vanguardia y regirse por las normas.
El panorama cambiante de los riesgos
Según un informe de Gartner de 2020, el 75 % de los directores de información realizan inversiones para mejorar la reducción de los riesgos cibernéticos, y es probable que esta cifra haya aumentado en los últimos años. Mientras las empresas buscan mejorar la disminución de riesgos, también deberán cumplir con los requisitos de cumplimiento normativo, lo cual aumenta la complejidad.
El cumplimiento de la seguridad determina si un sistema sigue las reglas de la política correspondiente. Existen varios estándares normativos que deben aplicarse de forma permanente. Algunos ejemplos son el Instituto Nacional de Estándares y Tecnología (NIST), que proporciona lineamientos sobre asuntos relacionados con la tecnología, y el Estándar de Seguridad de los Datos para la Industria de Tarjetas de Pago (PCI-DSS) para cuidar a los clientes y protegerse a usted mismo al aceptar pagos, entre muchos otros. En este artículo, nos centramos en el estándar del Centro de Seguridad de Internet (CIS). CIS es una organización sin fines de lucro que se esfuerza por proteger a las empresas públicas y privadas de las amenazas cibernéticas.
Es importante tener en cuenta que no existe una política de seguridad estándar, sino varias que aplican para diferentes empresas e incluso para los distintos sistemas dentro de una sola. Los sistemas tienen diferentes propósitos y muchos niveles de relevancia. No existe un enfoque universal para el cumplimiento normativo de la seguridad.
¿Por qué es importante esto? Cuando se trata del cumplimiento normativo, las soluciones que se adoptan inciden en los ejecutivos y los empleados de toda la empresa, y varían los aspectos que se deben tener en cuenta para cada función. Analicemos dos perfiles clave: el director general de seguridad de la información (CISO) y el administrador de sistemas.
Los aspectos que debe tener en cuenta un CISO incluyen:
Impulsar la flexibilidad y la agilidad de las tecnologías y la infraestructura mientras mantiene una estrategia de seguridad adecuada.
Cumplir con los requisitos normativos y de control.
Evitar noticias desfavorables que surgen de las interrupciones de la TI o las fallas de seguridad.
Los aspectos que debe tener en cuenta un administrador de sistemas (o un administrador de seguridad en establecimientos más grandes) incluyen:
Desarrollar y respaldar los estándares de seguridad, las prácticas recomendadas, las medidas preventivas y los planes de recuperación ante desastres de la empresa.
Supervisar las redes en busca de fallos de seguridad e investigar las infracciones a medida que surgen.
Implementar y actualizar el software para proteger los datos.
En 2021, Gartner informó que los clientes pierden USD 300 000 en promedio por hora durante el tiempo de inactividad de la TI. Según el informe, el costo depende de muchos factores, como los ingresos, el sector, la duración de la interrupción y el momento del día en el que ocurre, además de la cantidad de personas a las que afecta.
También se detallan algunos ejemplos en los que se observan pérdidas monetarias significativas: las empresas que dependen de las transacciones con muchos datos, como los bancos y las tiendas minoristas en línea, verán un aumento en estas cifras, al igual que los servicios que experimentan una interrupción durante los momentos de mayor uso. Es por esto que las empresas buscan soluciones para gestionar la expansión, reducir los riesgos y trabajar mejor con los recursos limitados. Red Hat cuenta con soluciones que ayudan a abordar estos desafíos, como Red Hat Satellite, Ansible Automation Platform e Insights.
Arquitectura de cumplimiento
En esta sección, veremos la forma en la que algunas de estas tecnologías funcionan en conjunto para producir una arquitectura de cumplimiento más adecuada.
Se dice que la automatización ocurre cuando se enfrenta un problema que no se desea volver a resolver. Pero ¿por dónde se empieza? Red Hat trabaja en un proyecto en GitHub denominado Compliance as Code (CaC). El proyecto CaC tiene un marco para desarrollar contenido de cumplimiento normativo de manera automatizada. No se trata solo de gestionar la configuración, sino también de proteger los contenedores, sus plataformas, sus servicios y los sistemas operativos, además de demostrar el funcionamiento correcto de estas medidas. Todo esto se incorpora en el proyecto OpenSCAP.
OpenSCAP está validado y certificado por el NIST y es la herramienta para el análisis de seguridad preferido de Red Hat que se usa con frecuencia en las suscripciones de Red Hat Enterprise Linux (RHEL) y Satellite. También analiza los puntos vulnerables conocidos y el cumplimiento de las normas de seguridad y cuenta con soporte para la automatización; de hecho, Red Hat ofrece muchos playbooks de corrección de Ansible y los respalda.
Con este proyecto, puede ir un paso más allá y producir contenido personalizable a través de la interfaz gráfica de SCAP Workbench. Entendemos que las diferentes empresas tienen su propio conjunto de procesos diseñados según su conveniencia para cumplir con los estándares establecidos, y lo más importante de la plataforma OpenSCAP es que resulta muy sencillo ajustar las políticas de manera que refleje sus procesos. En la segunda parte de esta serie, daremos un ejemplo sobre la forma de abordar todo esto, pero hay diferentes maneras de hacerlo.
Como se mencionó anteriormente en este artículo, el CIS se esfuerza por ayudar a proteger a las empresas públicas y privadas de las amenazas cibernéticas. Una forma de hacerlo es mediante la implementación de los indicadores de CIS, es decir, los documentos de las prácticas recomendadas del sector para la configuración de la seguridad de los sistemas de TI, el software y las redes. En un perfil de indicadores (Figura 1), disponible para su visualización desde los PDF CIS Benchmarks, que se pueden descargar fácilmente:
Se incluye el título de la descripción general del perfil del indicador.
Se indica el lugar en el que se aplica el perfil (un servidor o una estación de trabajo) y si es de nivel 1 o nivel 2; este último tiene requisitos más seguros.
Se incluye una descripción del perfil.
Se justifica el perfil del indicador.

Figura 1: perfil del indicador 5.2.11 (CIS Red Hat Enterprise Linux 8 Benchmark v2.0.0)
Afortunadamente, en la documentación también se proporciona la corrección que se requiere para cumplir con los requisitos del perfil del indicador:

Figura 2: Corrección para el perfil del indicador 5.2.11
A continuación, se muestra un fragmento como ejemplo de la forma en la que el perfil anterior podría implementarse fácilmente con un playbook de Ansible:
- name: ssh disable PermitEmptyPasswords
lineinfile:
state: present
dest: /etc/ssh/sshd_config
regexp: ^#?PermitEmptyPasswords
line: PermitEmptyPassword no
notify: restart sshdFuncionamiento conjunto de OpenSCAP y Ansible Automation Platform
Ya analizamos la forma en la que Red Hat Ansible Automation Platform ayuda a cumplir las normas, pero ¿de qué manera la plataforma y OpenSCAP funcionan en conjunto de manera automatizada?
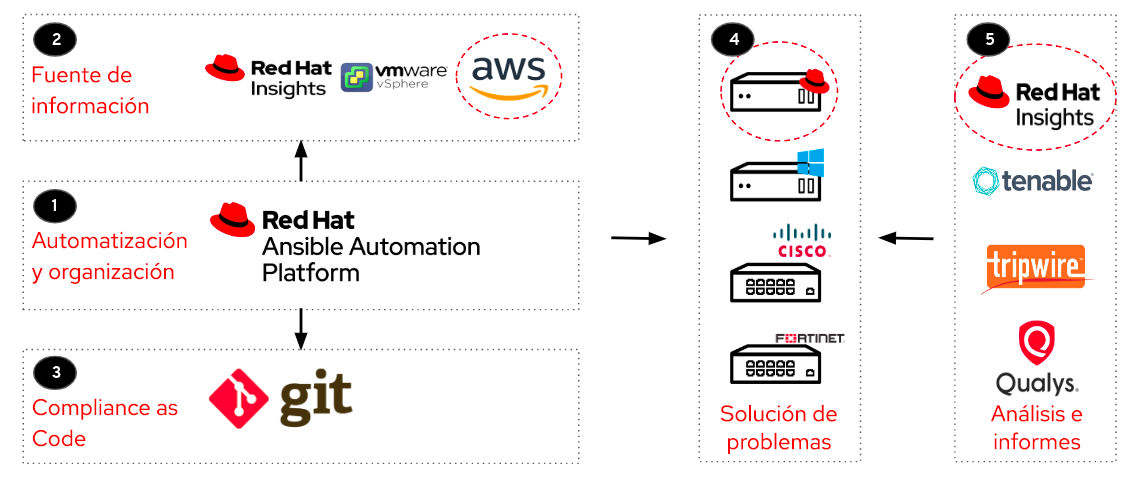
Figura 3: Flujo de trabajo de cumplimiento automatizado
Según lo que se muestra en la Figura 3, el flujo de trabajo previsto es el siguiente:
El plugin dinámico de Ansible irá a la fuente de información para descubrir los nodos registrados que deben gestionarse.
Esta fuente de información es una plataforma necesaria para los nodos registrados; entre los ejemplos se incluyen Red Hat Insights, VMware y AWS.
Se requiere un código para corregir los cambios, el cual se consigue de Git, donde puede extraer las reglas y los playbooks adecuados para incorporarlos a Ansible Automation Platform.
Ahora está todo listo para que implemente correcciones en cualquier dispositivo que desee, ya sea un servidor Linux, Windows, Cisco o cualquier otro que elija.
Por último, es aconsejable conocer el estado en el que se encuentra el host, en especial el estado de corrección, realizando análisis anteriores y posteriores. Para obtener esta información, puede utilizar herramientas como OpenSCAP dentro de Red Hat Insights, Tenable y Tripwire.
Los íconos que están rodeados por una línea punteada roja en la Figura 3 son los que usaremos para nuestro tutorial de corrección en la segunda parte, pero este flujo de trabajo sirve para demostrar que los casos de uso son infinitos. También verá que Insights aparece en más de un área del flujo de trabajo. Dado que usaremos esta solución principalmente para implementar la corrección, es útil conocer la manera en la que permite gestionar con anticipación el nivel de cumplimiento.
Red Hat Insights es una oferta de software como servicio (SaaS) que está disponible en la consola Hybrid Cloud Console. Permite analizar y prever de manera anticipada lo que sucede en su entorno de TI y clasificar los riesgos que le impedirán operar de manera óptima desde una perspectiva tecnológica. Además, brinda recomendaciones a través de su servicio de asesoramiento y automatiza las correcciones que se proporcionan.
Por más que usted no sea la persona que use Insights o que administre un entorno de Red Hat, la solución aporta un valor adicional a la empresa.
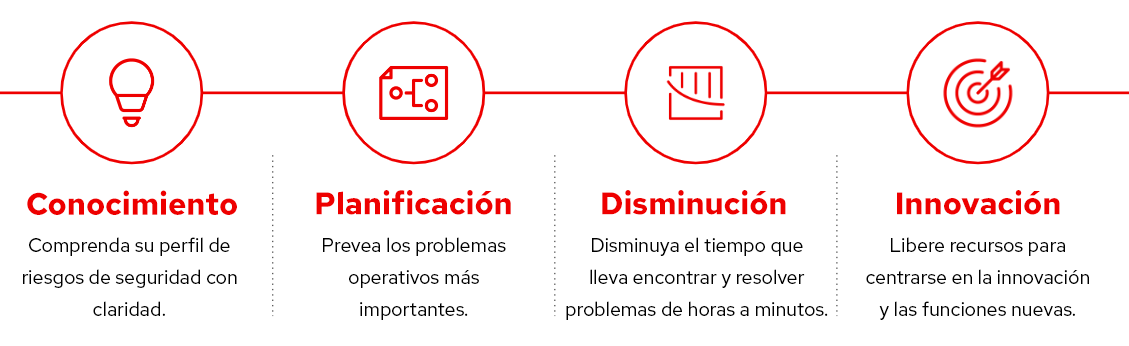
Figura 4: Ventajas importantes que ofrece Red Hat Insights para una empresa
Si necesita saber si el punto vulnerable más reciente afecta a su empresa, Insights genera en segundos una lista de todos los sistemas registrados.
Si esta falla afectó a los sistemas, la solución generará un playbook que se puede ejecutar manualmente para corregirla. Si prefiere automatizar este proceso, puede conectar Satellite a Insights con Cloud Connector y para hacerlo con solo un clic.
Todo esto ayuda a los equipos a pasar de un modelo reactivo a uno preventivo: en lugar de reaccionar al incidente una vez que está en marcha, los equipos pueden reducir los riesgos antes de que ocurra, lo que les da la libertad para concentrarse en iniciativas más estratégicas y de mayor valor que son importantes para la empresa.
Servicio de cumplimiento que se incluye con Red Hat Insights
El servicio de cumplimiento que se ofrece con Insights se basa en los informes de OpenSCAP. Esto permite que los clientes evalúen, supervisen, informen y corrijan los requisitos de cumplimiento normativo internos y externos en su entorno de Red Hat.

Figura 5: Visualización del panel del servicio de cumplimiento desde la consola de Red Hat Insights
Dentro del servicio de cumplimiento, puede evaluar un sistema con las políticas que se incluyen en la guía de seguridad para Red Hat Enterprise Linux o puede crear su propia política desde cero.
Este servicio señalará si la versión de OpenSCAP que se usa no es compatible con la versión de Red Hat Enterprise Linux que se implementa (Figura 5). Además, puede observar desde la consola si tiene sistemas que están asignados al host pero que no envían informes a Insights.
Para cada política, podrá ver la cantidad de sistemas que se evalúan, así como el nivel de cumplimiento. Todas ellas tienen un límite que se puede configurar para que se establezca el riesgo máximo que se admite en los niveles de la aplicación.
También tiene la opción de personalizar las reglas que forman parte de las políticas mediante el servicio de cumplimiento y comenzar a controlarlas rápidamente. Otra opción es usar SCAP Workbench para personalizar las políticas. Sin embargo, si elige este proceso, Insights no podrá verificar los cambios personalizados, por lo que deberá implementarlos directamente dentro de la solución.
Tenga en cuenta que la implementación de OpenSCAP en Red Hat Enterprise Linux es un enfoque uniforme para cada sistema. De todas formas, existen maneras de ampliar la capacidad, como usar Red Hat Satellite conectado a Insights utilizando Cloud Connector, lo que le permite implementar muchos sistemas, hasta cientos o miles, con bastante facilidad.
En resumen, a la hora de gestionar el cumplimiento normativo de su empresa, Insights funciona simultáneamente como el panel de control y el verificador, lo que le permite anticipar y cortar esos avisos de raíz con la ayuda de su mecánico de confianza, Ansible.
Obtenga más información
Sobre el autor
Ally Kouao is a Portfolio Solution Architect based in the UK, who joined Red Hat in 2019. Her areas of interest and expertise encompass all things to do with security and automation.
Más como éste
Redefining automation governance: From execution to observability at Bradesco
Chasing the holy grail: Why Red Hat’s Hummingbird project aims for "near zero" CVEs
Understanding AI Security Frameworks | Compiler
Data Security And AI | Compiler
Navegar por canal
Automatización
Las últimas novedades en la automatización de la TI para los equipos, la tecnología y los entornos
Inteligencia artificial
Descubra las actualizaciones en las plataformas que permiten a los clientes ejecutar cargas de trabajo de inteligecia artificial en cualquier lugar
Nube híbrida abierta
Vea como construimos un futuro flexible con la nube híbrida
Seguridad
Vea las últimas novedades sobre cómo reducimos los riesgos en entornos y tecnologías
Edge computing
Conozca las actualizaciones en las plataformas que simplifican las operaciones en el edge
Infraestructura
Vea las últimas novedades sobre la plataforma Linux empresarial líder en el mundo
Aplicaciones
Conozca nuestras soluciones para abordar los desafíos más complejos de las aplicaciones
Virtualización
El futuro de la virtualización empresarial para tus cargas de trabajo locales o en la nube
