Security is a top priority for OpenShift. OpenShift 4.3 laid the groundwork for even more robust image security with Quay Container Security Integration, which allows registry images to be scanned for vulnerabilities right from the OpenShift Web Console and surfaced on the cluster dashboard’s Status card.
For OpenShift 4.4, we’ve taken this security a step further. To enhance the Container Security Operator's functionality, we've added a dedicated Image Manifest Vulnerabilities list to the Administrator section, where you can quickly view and diagnose these vulnerabilities. You can also access this view from an individual pod, allowing the list of image vulnerabilities to be filtered to those that relate to that specific pod. Let's get into it.
Viewing image vulnerabilities
When cluster security is at risk, you want to take quick and efficient action. That's where the Image Manifest Vulnerabilities list comes in. Once the Container Security Operator has been installed, container image vulnerabilities in pods running on the cluster will begin to populate the list in the Administration section.

This list view conveys a quick overview of images’ vulnerabilities, such as the highest severity for the image, the number of pods affected, and the number of fixable vulnerabilities within the image. If you are interested in viewing a detailed breakdown of all vulnerabilities, along with other security scan information such as packages installed that don't have vulnerabilities, the image manifest’s hash is also a link to these details on the Quay instance the image is hosted on.

To get into the specifics, you can view the details of the Image Manifest Vulnerabilities resource. This offers a more expanded view of the image’s status, powered by Quay Security Scanner, where you can see a summary of the count of vulnerabilities and severity. You can also see the list of vulnerabilities affecting the image, along with their severity, package and current package version, and the version in which the vulnerability is fixed. The vulnerability name links to external security data with further information about the description and solution to the issue.

Let's say an admin is curious about which pods are affected by the vulnerable image. The **Affected Pods** tab shows a complete list of pods. Each name links to the pod resource, which assists in updating the image and getting those vulnerabilities fixed!
Assessing pod security
Alternatively, perhaps you are interested in confirming that a particular pod is secure. Admins can also access the Image Manifest Vulnerabilities list from the pod that might be running a vulnerable image.
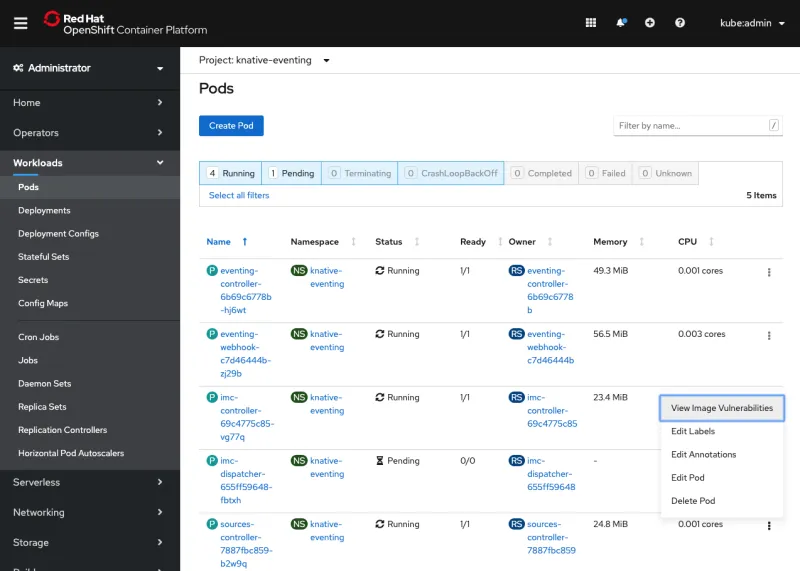
Accessing the list of Image Manifest Vulnerabilities from a pod is as easy as a new **View Image Vulnerabilities** action, available from the pods list or a pod’s **Actions** menu, which quickly gives a sense of that pod’s image security status.

This new action leads to the Image Manifest Vulnerabilities list—but that list is now filtered to show only that pod's vulnerable image, if any vulnerabilities exist.
Staying secure
Quay Container Security integration gives administrators greater confidence to know their cluster images are secure, right from within the OpenShift Web Console. Viewing image vulnerabilities from right within the console allows quicker discovery and rectification, ultimately leading to an overall more secure cluster.
But we aren’t done yet.
Quay integration will continue to expand in the future. So stay tuned for more security features like notifications when a new vulnerability is found and repository-related features like image management.
If you are just getting started with OpenShift or want to try these features now, visit the newly revamped Try OpenShift site to get instant access to a cluster. If you’d like to learn more about what the OpenShift design team is up to, check out our github design repo, or if you are interested in providing any feedback on any of the new 4.4 features or have suggestions for the future, please take this brief 3-minute survey.
À propos de l'auteur
Plus de résultats similaires
Red Hat to acquire Chatterbox Labs: Frequently Asked Questions
Attestation vs. integrity in a zero-trust world
What Is Product Security? | Compiler
Technically Speaking | Security for the AI supply chain
Parcourir par canal
Automatisation
Les dernières nouveautés en matière d'automatisation informatique pour les technologies, les équipes et les environnements
Intelligence artificielle
Actualité sur les plateformes qui permettent aux clients d'exécuter des charges de travail d'IA sur tout type d'environnement
Cloud hybride ouvert
Découvrez comment créer un avenir flexible grâce au cloud hybride
Sécurité
Les dernières actualités sur la façon dont nous réduisons les risques dans tous les environnements et technologies
Edge computing
Actualité sur les plateformes qui simplifient les opérations en périphérie
Infrastructure
Les dernières nouveautés sur la plateforme Linux d'entreprise leader au monde
Applications
À l’intérieur de nos solutions aux défis d’application les plus difficiles
Virtualisation
L'avenir de la virtualisation d'entreprise pour vos charges de travail sur site ou sur le cloud
