table { border: #ddd solid 1px; } td, th { padding: 8px; border: #ddd solid 1px; } td p { font-size: 15px !important; }
SAP officially announced the support for SAP HANA 2.0 on Red Hat Enterprise Linux 8.1 for SAP Solutions on Intel and IBM POWER9 architectures in March 2020. With this offering, SAP HANA is fully certified and supported on Red Hat Enterprise Linux 8.1 for SAP Solutions as documented in SAP notes 2777782 and 2235581.
Today, we will walk you through how to use Red Hat Enterprise Linux for SAP Solutions and Ansible Roles to automate your SAP HANA System Replication deployment on RHEL 8.1. In the following demo, we will run SAP HANA System Replication on Microsoft Azure Cloud.
Note: The Azure Cloud setups (e.g. VM and network, etc.) in this demo can be used for setting up test and development HANA instances on Azure. For officially supported production HANA Setups on Azure, please follow the guidelines provided by Microsoft.
What is RHEL for SAP Solutions?
RHEL for SAP Solutions offers the following components for your SAP applications:
-
SAP-specific technical components to support S/4HANA, SAP HANA, and SAP Business Applications, e.g. compat-sap-c++, compat-locales-sap, etc.
-
High availability solutions for S/4HANA, SAP HANA, and SAP Business Applications, which provide Pacemaker resource agents and other components needed for setting up high available SAP environments
-
RHEL System Roles for SAP, which can be used to automate the configuration of a RHEL system to run SAP workloads, examples will be covered later in this document.
-
Smart Management and Red Hat Insights for lifecycle management and proactive optimization.
-
Update services for SAP Solutions, providing support for specific minor RHEL releases for four years from general availability.
Note: Cloud Providers (e.g. Azure) may offer you a Pay-As-You-Go (PAYG) model for SAP software. The subscription for RHEL is then included in the offer and is called “RHEL for SAP with High Availability and Update Services” and offers the same functionality as RHEL for SAP Solutions but without Smart Management.
Red Hat also offers Red Hat Cloud Access, which allows you to run eligible Red Hat product subscriptions on certified public cloud providers (e.g. Azure). This model is called “Bring-Your-Own-Subscription” (BYOS). It makes your subscriptions portable, so you may choose the best architecture and infrastructure for your needs on public clouds.
What are System Roles?
Based on the usage and supportability, there are 3 “types” of Ansible Roles available specifically for SAP workloads to automate and accelerate your SAP deployments as shown in the following picture:
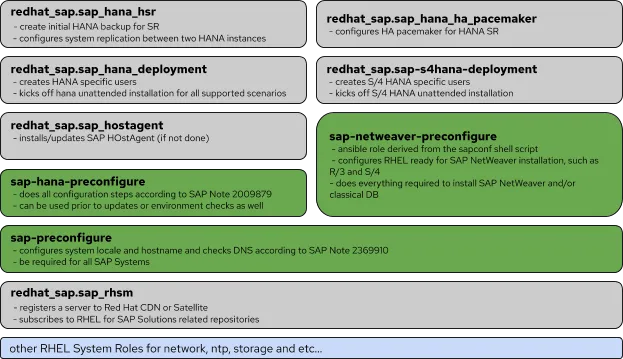
First, the grey boxes are community-driven Ansible roles for SAP from Ansible Galaxy. These roles are maintained by Red Hat Community of Practice (CoP) for SAP. You can tell their functions from their names, which can be used to deploy SAP HANA System Replication, S/4 HANA stack, etc... Second, RHEL for SAP Solutions offers RHEL System Roles for SAP in green boxes, which help you configure your RHEL environment for SAP applications. Red Hat provides technical support for these roles. Lastly, the light blue ones at the bottom are the RHEL system roles in technical preview, which will cover the settings of network, NTP, storage, etc.
Automate your SAP HANA deployment
In the following demo, all the servers are running on the Azure Cloud, including bootstrap and SAP HANA servers. So, you will need an Azure account to create VMs. To automate the deployment, you need to have a “bootstrap” server. The bootstrap will run an Ansible playbook (i.e. deploy_azure_vms.yaml) to deploy Azure VMs. And then, it will run another playbook (i.e. deploy-sap-hana-hsr.yaml) to set up RHEL, install SAP HANA, and set up SAP HANA System Replication (SR) eventually. Additionally, the bootstrap also shares the SAP media to the VMs via NFS.
Since you need to SSH to the bootstrap in this demo, the bootstrap will need to have a public IP. For the SAP HANA VMs, only internal IP is needed. Besides, both bootstrap and SAP HANA VMs are located in the default subnet, you can also create a separate subnet for your SAP applications as long as the servers can talk to each other.


It’s time to set up an SAP HANA environment! Doing so involves a few steps. But, follow along with the steps below and you’ll be well on your way to deploy your SAP HANA System Replication environment!
As shown in the below picture, you’ll first need to set up a “bootstrap” for your SAP applications. Once the bootstrap is set up, you can run Ansible roles and modules on the bootstrap to deploy 2 Azure VMs and install SAP HANA SR on the VMs.

Installing the Bootstrap server
In this demo, the bootstrap server is running on RHEL 8.1. To set up the bootstrap server, you will need to install Ansible cloud modules for Azure, system roles for SAP, and NFS server to store SAP HANA media.
The installation was pretty easy but setting up isn’t quite as so. If you’re not scared off yet, let’s jump right into it.
Setting up Ansible Cloud Modules for Azure
You’ll first need to set up your RHEL subscription and Ansible Engine.
# subscription-manager clean # mv /etc/yum.repos.d/rh-cloud.repo /etc/yum.repos.d/rh-cloud.repo.bk # subscription-manager register --auto-attach # subscription-manager repos --enable=ansible-2.8-for-rhel-8-$(uname -m)-rpms # yum install -y ansible
Once the Ansible Engine is installed, set up and install Azure CLI.
# rpm --import https://packages.microsoft.com/keys/microsoft.asc # sh -c 'echo -e "[azure-cli]\nname=Azure CLI\nbaseurl=https://packages.microsoft.com/yumrepos/azure-cli\nenabled=1\ngpgcheck=1\ngpgkey=https://packages.microsoft.com/keys/microsoft.asc" > /etc/yum.repos.d/azure-cli.repo' # yum install -y azure-cli
Now, let’s install the required packages for the Azure Python SDK modules.
# yum install -y gcc libffi-devel platform-python-devel openssl-devel # yum install -y python3-pip python3-wheel # curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py # python3 get-pip.py # pip3 install 'ansible[azure]' --use-feature=2020-resolver
It is worth mentioning that these Ansible Cloud modules for Azure will be installed in path /usr/lib/python3.6/site-packages/ansible/modules/cloud/azure.
Ansible includes a suite of modules for interacting with Azure Resource Manager, giving you the tools to easily create and orchestrate infrastructure on the Microsoft Azure Cloud. Using the Azure Resource Manager modules requires authenticating with the Azure API. Let’s configure Azure authentication with Azure service principal.
You’ll first need to enter “az login” to authenticate your Azure administration server and log in.
# az cloud set --name AzureCloud # az login
And then, create an Azure service principal with Azure CLI.
# az ad sp create-for-rbac --name hanaSP
 Once the service principal is created, record the Azure SubscriptionID.
Once the service principal is created, record the Azure SubscriptionID.
# az account show
Lastly, Insert the following lines into the credentials file.
# mkdir $HOME/.azure # vi $HOME/.azure/credentials [default] subscription_id=<id from command "az account show"> client_id=<"appId"> secret=<"password"> tenant=<"tenant">
Now, Azure authentication is configured, you need to create an ssh key pair on the bootstrap server, and record the public key. You will use it while creating Azure VMs.
# ssh-keygen -t rsa
Setting up NFS server for SAP media
To store the installation media, you will need to install and set up NFS server, and unzip the SAP HANA installation binary to the NFS share (e.g. /ssd_vms/SAP_HANA_BINARY/HANA2SPS04/)
Setting up System Roles for SAP HANA
Now, let’s install the following system roles for SAP.
- redhat_sap.sap_rhsm - redhat_sap.sap_hana_mediacheck - linux-system-roles.timesync - linux-system-roles.storage - redhat_sap.sap_hana_deployment - redhat_sap.sap_hostagent - redhat_sap.sap_hana_hsr
Make sure to install the RHEL System Roles for SAP.
# yum -y install rhel-system-roles-sap
Once the roles are installed, you will need to set the RHEL release and enable required repositories for the bootstrap server by running the following playbook:
setup_subscription.yaml
--- - name: test variables of rhsm hosts: localhost connection: local become_user: root vars: # sap_rhsm role variables sap_rhsm_username: '<your Red Hat login>' sap_rhsm_password: '<your Red Hat login password>' sap_rhsm_pool_ids: - "<pool id>" roles: - { role: redhat_sap.sap_rhsm }
If you have questions about which repositories have been enabled currently, you can check the handy tool - RHEL for SAP Configurator.
And then, it is an important step to set up variables for SAP HANA servers, you can refer to the following configurations:
|
./group_vars/hana.yml |
--- # sap_rhsm role variables sap_rhsm_username: '<your Red Hat login>' sap_rhsm_password: '<your Red Hat login password>' sap_rhsm_pool_ids: - "<your pool id>" # Deploy SAP HANA vars sap_hana_deployment_root_password: "MyPassw0rd!" sap_hana_deployment_sapadm_password: "MyPassw0rd!" sap_hana_deployment_hana_sid: RHT sap_hana_deployment_hana_instance_number: "01" sap_hana_deployment_hana_env_type: development sap_hana_deployment_hana_mem_restrict: 'n' sap_hana_deployment_hana_db_system_password: "MyPassw0rd!" sap_hana_deployment_ase_user_password: "MyPassw0rd!" sap_hana_deployment_hana_groupid: 30200 sap_hana_deployment_hana_userid: 30200 sap_hana_deployment_apply_license: false # Seems sapadm password won't be taken, so use a common master password instead # Update it if sapadm password is working again sap_hana_deployment_common_master_password: "MyPassw0rd!" sap_hana_deployment_use_master_password: y # Variables required for 'sap_hana_hsr' role sap_hana_hsr_hana_sid: RHT sap_hana_hsr_hana_instance_number: "01" sap_hana_hsr_hana_db_system_password: "MyPassw0rd!" sap_hana_hsr_hana_primary_hostname: saphana01 # linux-system-roles.storage role variables storage_pools: - name: vgsaphana disks: - sdc volumes: - name: hana_shared size: "24 GiB" mount_point: "/hana/shared" fs_type: xfs state: present - name: hana_data size: "24 GiB" mount_point: "/hana/data" fs_type: xfs state: present - name: hana_logs size: "12 GiB" mount_point: "/hana/logs" fs_type: xfs state: present - name: usr_sap size: "49 GiB" mount_point: "/usr/sap" fs_type: xfs state: present # rhel-system-roles.timesync variables ntp_servers: - hostname: 0.rhel.pool.ntp.org iburst: yes - hostname: 1.rhel.pool.ntp.org iburst: yes - hostname: 2.rhel.pool.ntp.org iburst: yes - hostname: 3.rhel.pool.ntp.org iburst: yes # SAP Preconfigured role # SAP-Media Check (get unpacked HANA from Mountpoint) sap_hana_mediacheck_serverpath: "10.0.0.4:/ssd_vms/SAP_HANA_BINARY/HANA2SPS04" sap_hana_mediacheck_mountpoint: /SAP_HANA_BINARY sap_hana_installdir: "{{ sap_hana_mediacheck_mountpoint + '/DATA_UNITS/HDB_SERVER_LINUX_' + ansible_architecture|upper }}" # SAP Host Agent sap_hostagent_installation_type: "bundle" sap_hostagent_bundle_path: "{{ sap_hana_installdir + '/server'}}" sap_hostagent_clean_tmp_directory: true ... |
|
./host_vars/saphana01.yml |
sap_hana_hsr_role: "primary" sap_hana_hsr_alias: "DC1" |
|
./host_vars/saphana02.yml |
sap_hana_hsr_role: "secondary" sap_hana_hsr_alias: "DC2" |
You survived! Congratulations! There are only a few steps left, I promise.
Deploying 2 Azure VMs for SAP HANA
Once you’ve got all of the proper prerequisites, it’s time to deploy the Azure VMs. To get the VMs deployed, you would need to do some preparatory steps on Azure. You’ll first need to create Resource Group (i.e. ResourceGroupHana) and Virtual Network (i.e. VirtualNetworkHana). And then, check your Azure subscription’s quotas to make sure that you have a sufficient number of vCPU in your quotas. Otherwise, your playbook will fail.
 So you’ve installed Ansible modules for Azure and survived the setup portion. Now comes the easy part; deployment Azure VMs by running the following playbook:
So you’ve installed Ansible modules for Azure and survived the setup portion. Now comes the easy part; deployment Azure VMs by running the following playbook:
./deploy_azure_vms.yaml
--- - hosts: localhost connection: local vars: resource_group: ResourceGroupHana virtual_network: ResourceGroupHana-vnet virtual_subnet: default virtual_machine1: saphana01 virtual_machine2: saphana02 nic1: NicHana01 nic2: NicHana02 security_group: SecurityGroupHana tasks: - name: Ensure a security group that allows SSH azure_rm_securitygroup: resource_group: "{{ resource_group }}" name: "{{ security_group }}" rules: - name: 'AllowSSH' protocol: Tcp destination_port_range: 22 access: Allow priority: 101 direction: Inbound - name: Ensure a network interface for VM saphana01 azure_rm_networkinterface: resource_group: "{{ resource_group }}" name: "{{ nic1 }}" virtual_network: "{{ virtual_network }}" subnet_name: "{{ virtual_subnet }}" security_group: "{{ security_group }}" ip_configurations: - name: ipconfig1 primary: True - name: Ensure a VM saphana01 to run SAP HANA azure_rm_virtualmachine: resource_group: "{{ resource_group }}" name: "{{ virtual_machine1 }}" vm_size: Standard_E8s_v3 admin_username: adminUser admin_password: "adminUser#1" ssh_public_keys: - path: /home/adminUser/.ssh/authorized_keys key_data: <Insert the public key of the bootstrap server here> network_interfaces: "{{ nic1 }}" image: offer: "RHEL" publisher: "RedHat" sku: '8.1' version: latest managed_disk_type: Standard_LRS data_disks: - lun: 0 disk_size_gb: 128 managed_disk_type: Premium_LRS - name: Ensure a network interface for VM saphana02 azure_rm_networkinterface: resource_group: "{{ resource_group }}" name: "{{ nic2 }}" virtual_network: "{{ virtual_network }}" subnet_name: "{{ virtual_subnet }}" security_group: "{{ security_group }}" ip_configurations: - name: ipconfig2 primary: True - name: Ensure a VM saphana02 to run SAP HANA azure_rm_virtualmachine: resource_group: "{{ resource_group }}" name: "{{ virtual_machine2 }}" vm_size: Standard_E8s_v3 admin_username: adminUser admin_password: "adminUser#1" ssh_public_keys: - path: /home/adminUser/.ssh/authorized_keys key_data: <Insert the public key of the bootstrap server here> network_interfaces: "{{ nic2 }}" image: offer: "RHEL" publisher: "RedHat" sku: '8.1' version: latest managed_disk_type: Standard_LRS data_disks: - lun: 0 disk_size_gb: 128 managed_disk_type: Premium_LRS ...
The following picture is the screen dump while running the above playbook:

Once the VMs are deployed successfully, remember to add the entries of the VMs to /etc/hosts on the bootstrap. The following playbook helps you get the IP address for your HANA servers:
--- - hosts: localhost connection: local tasks: - name: Get facts for saphana01's network interface azure_rm_networkinterface_facts: resource_group: ResourceGroupHana name: NicHana01 register: result - name: Print Private IP address for saphana01 debug: msg: - "saphana01 Private IP address: {{ result.networkinterfaces[0].ip_configurations[0].private_ip_address }}" - name: Get facts for saphana02's network interface azure_rm_networkinterface_facts: resource_group: ResourceGroupHana name: NicHana02 register: result - name: Print Private IP address for saphana02 debug: msg: - "saphana02 Private IP address: {{ result.networkinterfaces[0].ip_configurations[0].private_ip_address }}" ...
Once you’ve got the IP addresses, edit the /etc/hosts.
10.0.0.5 saphana01 saphana01.<domain_name> 10.0.0.6 saphana02 saphana02.<domain_name>
Installing SAP HANA with System Replication
Now that you’ve deployed the Azure VMs, it’s time to install SAP HANA with System Replication. Before getting to the last step, let’s run the below playbook to fix a few existing issues:
./fix_vms_issues.yaml
--- - hosts: hana tasks: - name: Copy a new "/etc/hosts" file into place, backing up the original if it differs from the copied version copy: src: /etc/hosts dest: /etc/hosts owner: root group: root mode: '0644' backup: yes - name: Disable RHUI repos by renaming repo file /etc/yum.repos.d/rh-cloud.repo command: mv /etc/yum.repos.d/rh-cloud.repo /etc/yum.repos.d/rh-cloud.repo.bk - name: Extend root filesystem “/” of VMs to 10GB, the default to 2GB lvol: vg: rootvg lv: rootlv size: 10240 - name: Extend the filesystem filesystem: fstype: xfs dev: "/dev/mapper/rootvg-rootlv" resizefs: yes ...
Now, you are free to go and run the following playbook to deploy SAP HANA SR:
./deploy-sap-hana-hsr.yaml
--- - hosts: hana roles: - { role: redhat_sap.sap_rhsm } - { role: redhat_sap.sap_hana_mediacheck } - { role: redhat_sap.sap_hostagent } - { role: linux-system-roles.timesync } - { role: linux-system-roles.storage } - { role: sap-preconfigure } - { role: sap-hana-preconfigure } - { role: redhat_sap.sap_hana_deployment } - { role: redhat_sap.sap_hana_hsr } ...
Here is the screen dump while running the playbook. It takes approximately 20 minutes to install the SAP HANA instances and configure System Replication.


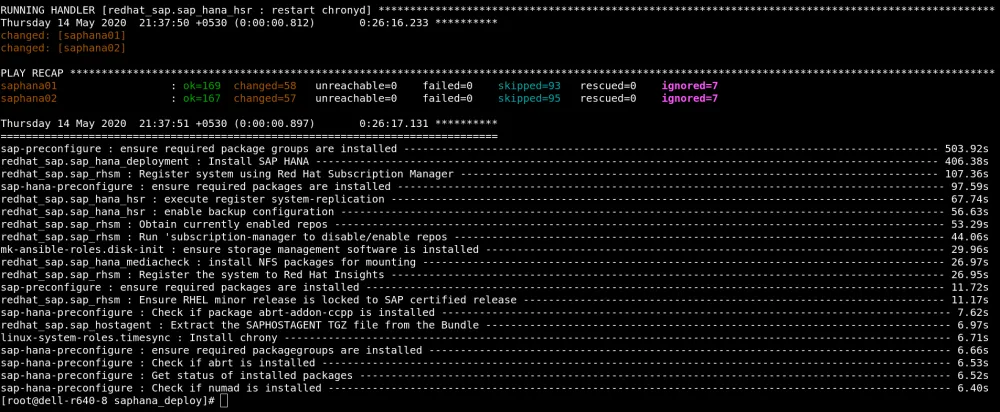
Once the installation is complete, you can check the status of SAP HANA System Replication.

Summary
As SAP HANA takes on a central function as the primary database platform for SAP landscapes, requirements for stability, and reliability increase dramatically. With RHEL for SAP Solutions and system roles, you can deploy your SAP HANA in about 20 minutes!
To further simplify the settings, you can convert the bootstrap server to an Azure VM image, so you can quickly start up a bootstrap to deploy your SAP applications when you need it. Besides, Red Hat Enterprise Linux (RHEL) for SAP Solutions meets those requirements by enhancing native SAP HANA replication and failover technology to automate the takeover process, in order to reduce system administrators’ efforts and increase the stability and availability of your SAP applications.
À propos de l'auteur
Edward Jin has been working in IT for more than 12 years. He has a strong service mindset and design thinking and insights to IT systems and processes within the pharmaceutical , manufacturing and finance industry. Currently, he is helping customers on their digital journey using open source technology.
Plus de résultats similaires
Data-driven automation with Red Hat Ansible Automation Platform
Ford's keyless strategy for managing 200+ Red Hat OpenShift clusters
Technically Speaking | Platform engineering for AI agents
Technically Speaking | Driving healthcare discoveries with AI
Parcourir par canal
Automatisation
Les dernières nouveautés en matière d'automatisation informatique pour les technologies, les équipes et les environnements
Intelligence artificielle
Actualité sur les plateformes qui permettent aux clients d'exécuter des charges de travail d'IA sur tout type d'environnement
Cloud hybride ouvert
Découvrez comment créer un avenir flexible grâce au cloud hybride
Sécurité
Les dernières actualités sur la façon dont nous réduisons les risques dans tous les environnements et technologies
Edge computing
Actualité sur les plateformes qui simplifient les opérations en périphérie
Infrastructure
Les dernières nouveautés sur la plateforme Linux d'entreprise leader au monde
Applications
À l’intérieur de nos solutions aux défis d’application les plus difficiles
Virtualisation
L'avenir de la virtualisation d'entreprise pour vos charges de travail sur site ou sur le cloud
