In this post:
- Red Hat Insights is 91% faster than discovering vulnerabilities on a fleet of systems using a scripted or any sort of manual method. See how the dashboard helps you quickly discover vulnerabilities that are affecting your systems.
- Insights doesn’t just help you know if you are vulnerable, it helps you remediate the issue in your environment with as little friction as possible. By expanding the view of your system, Insights will tell you what to do to fix the vulnerability.
- Use the "Remediate” button to start the process of generating an Insights playbook that you can either download and run on your own or execute directly from Insights.
I woke up this morning and heard about the latest vulnerability in my news feed. Today it was polkit/pwnkit, a couple weeks ago it was something else. (And another will be along shortly, no doubt.) When these come out the impact on IT teams are huge and for anyone responsible for managing systems, one of your first thoughts is “am I exposed and to what extent?”
If you are using Red Hat Enterprise Linux (RHEL), you can use Red Hat Insights to find out what systems are exposed, and to what extent.

Right on the Dashboard of Insights for Red Hat Enterprise Linux is the latest vulnerability - Polkit, pwnkit, or CVE-2121-4034.
When I look at the dashboard I have 16 systems exposed. My level of effort? Almost zero. I opened up the Hybrid Cloud Console and just looked at the information Insights was showing me.
Faster discovery
Red Hat Insights is one way you can find your level of exposure quickly - according to a study by Principled Technologies, "Save administrator time and effort by activating Red Hat Insights," Insights is 91% faster than discovering vulnerabilities on a fleet of systems using a scripted or any sort of manual method. This time savings is really important when you need to understand your level of exposure and you need to report this information to various stakeholders.
For Red Hat Enterprise Linux (RHEL) systems, Insights will also be better attuned to the software on your systems than manual methods. Manual methods that rely on naive checks, like simply looking at the version number reported by software, won't tell you whether Red Hat has backported security fixes to the specific versions of software.
Since this vulnerability is new, it was right on the dashboard, so this was easier than normal to find. If I was looking for something a little older I might have a couple more steps - go to the Insights Vulnerability service then search for the CVE ID or common name if it has one.
 From this page, I can select the CVE - I’m going to stick with polkit since it affects several of my systems.
From this page, I can select the CVE - I’m going to stick with polkit since it affects several of my systems.
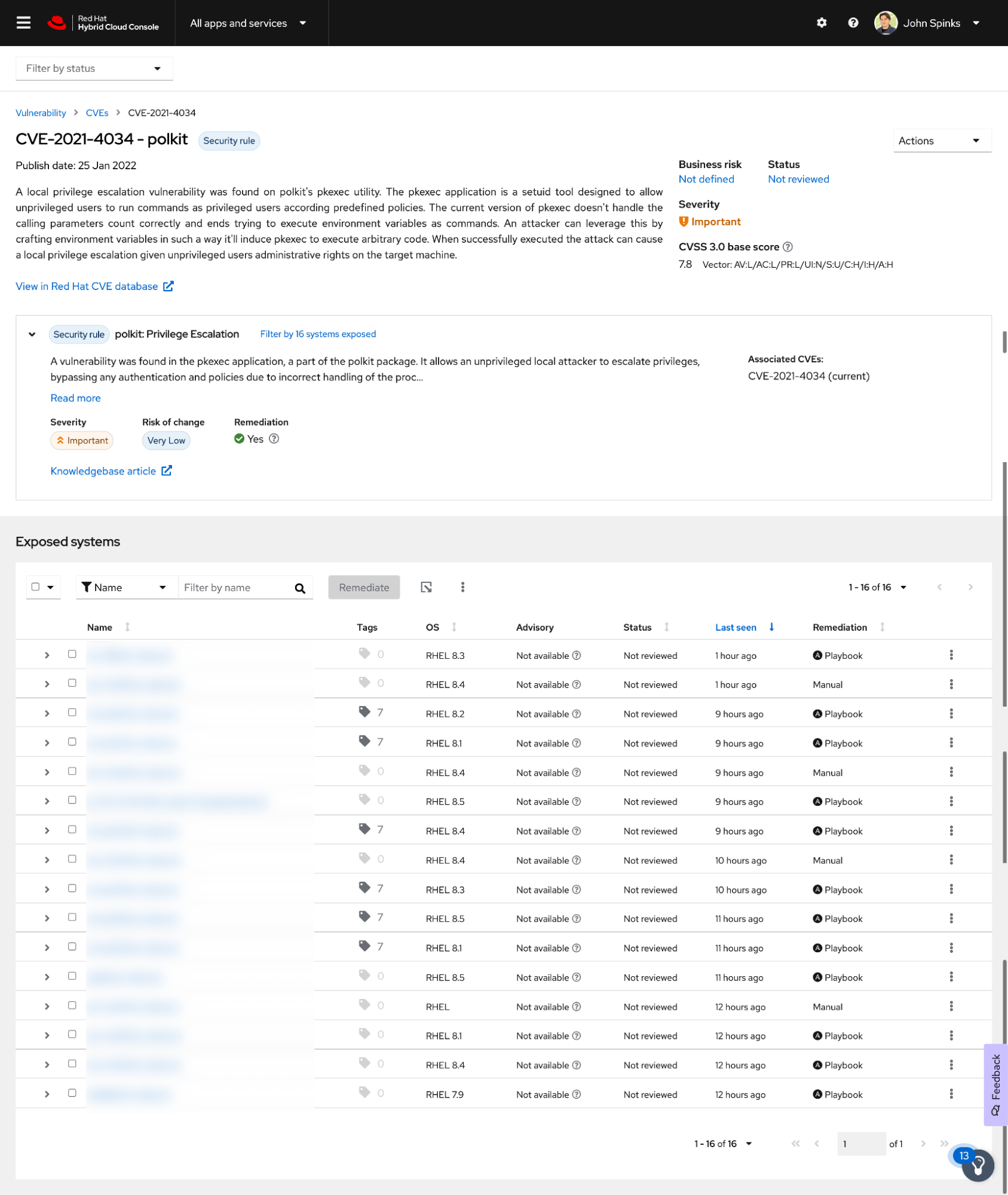
From this page I can see the vulnerability details including common vulnerability scoring system (CVSS) score, severity, and a link to the Red Hat CVE database which will have even more information. In this case we also have a security rule associated which means that Red Hat’s Product Security team has done more in depth analysis about the severity and impact of this vulnerability with additional information such as the risk of making the change needed to protect your organization from this vulnerability.
Further down the page I see the list of systems impacted - In this case I have 16 systems impacted across a variety of RHEL versions. If you need to send a list of impacted systems to anyone, Insights provides an option to export affected hosts.
It is important to know that Insights doesn’t just help you with knowing if you are vulnerable - it helps you remediate the issue in your environment with as little friction as possible. Of systems impacted, one is a test system that doesn’t have any critical workloads on it. I’m going to start by fixing this on a single system just to see how it goes.
The system in question is an AWS system with the default hostname (I was reproducing an issue and this system won’t live long enough to get a proper host name).
If I expand the view of this system, Insights will tell me what I need to do to fix this vulnerability, specific to this version of RHEL. In this case, we are just updating the package using: yum update polkit.

Faster remediation
Insights can actually fix this for me though.
If I check the box next to the system name, as shown in the image above the “Remediate” button becomes available. This will start the process of generating an Insights playbook that you can either download and run on your own (or sync with your Ansible Automation Platform environment) or execute directly from Insights.
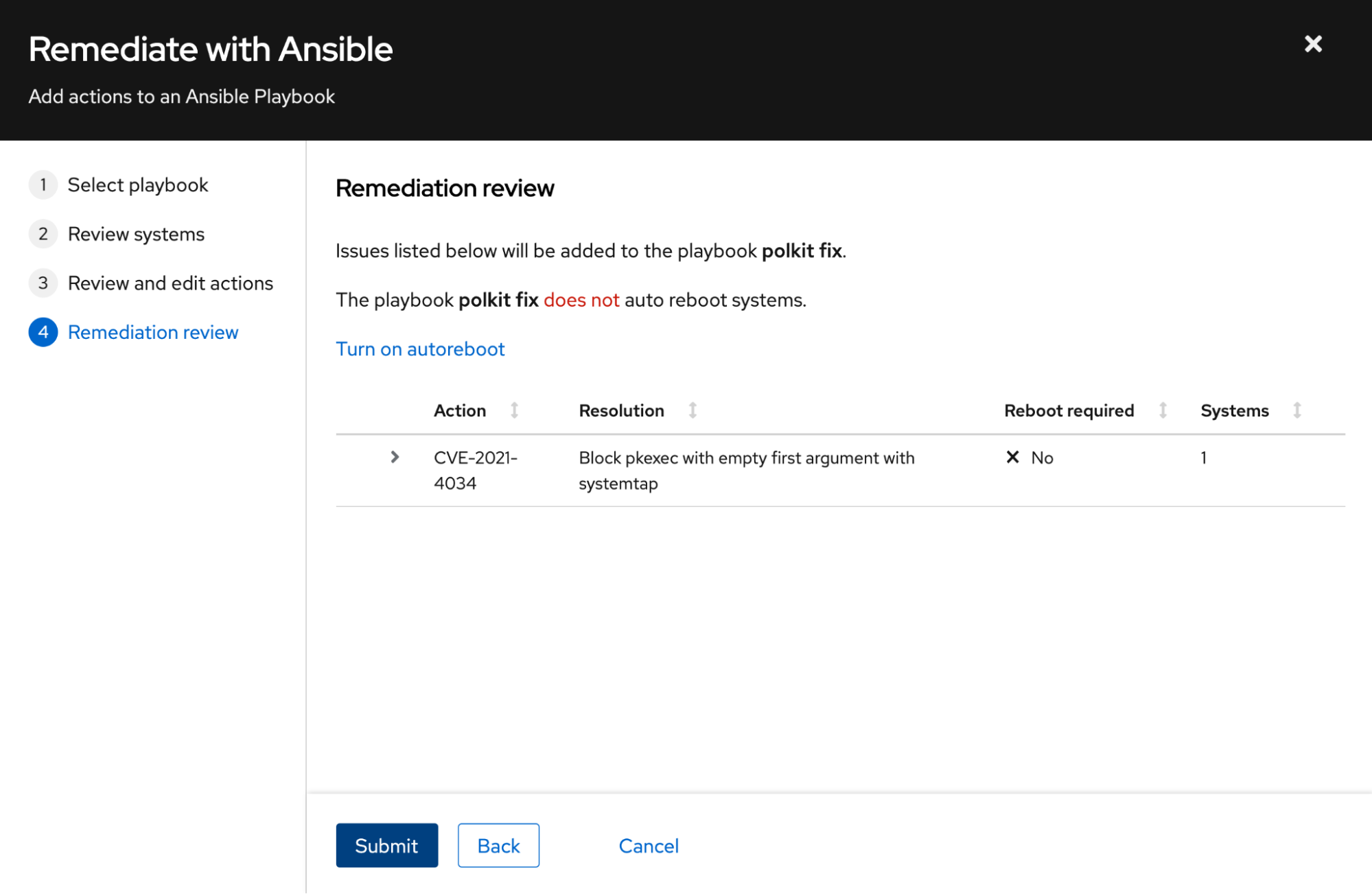
In order to do this, you click the Remediate button (you can select all the machines, but I am testing this with just one system before I deploy the fix everywhere). This starts a wizard that walks you through several steps we'll look at here.
Create a new playbook (or add to an existing one).

Next, review the list of systems you’re fixing the issue on:

Once you have the playbook, you can download it or run it.

First, I downloaded the playbook and inspected it to see what it would do on my system.
Everything is in order and this drastically shortened my time to remediate as I didn’t have to create this playbook by hand - I just downloaded and inspected it. When time is of essence and you need to protect your organization as quickly as possible against a malicious threat, this is important.
Now I am ready to run the playbook. I have an Execute playbook button available to me.
This does require some setup that I previously had done in my environment. You have two options if you want to use this functionality:
-
Execute playbooks using Red Hat Satellite - This requires you to have Red Hat Satellite infrastructure, your hosts are connected to the Satellite, and Cloud Connector is configured.
-
Execute playbooks using Red Hat connector - This requires you to use the Red Hat connector (RHC) command to connect your systems to Insights. RHC is a new feature that is supported starting with RHEL 8.5. I’m using this Red Hat connector functionality on this specific system.
-
In addition to the above, since you are making changes on systems, an organization admin needs to provide you with the Remediations Administrator role in the Hybrid Cloud Console Role Based Access Control (RBAC).
I already have all of this set up. I just wanted to explain in case you try to follow along and the Execute playbook button is not enabled for you. If you want to enable it, refer to the docs above. You could also watch the Connect and secure Red Hat Enterprise Linux on AWS video to see setup, configuration, and use of RHC in an AWS environment.
I’m going to click the Execute playbook button.
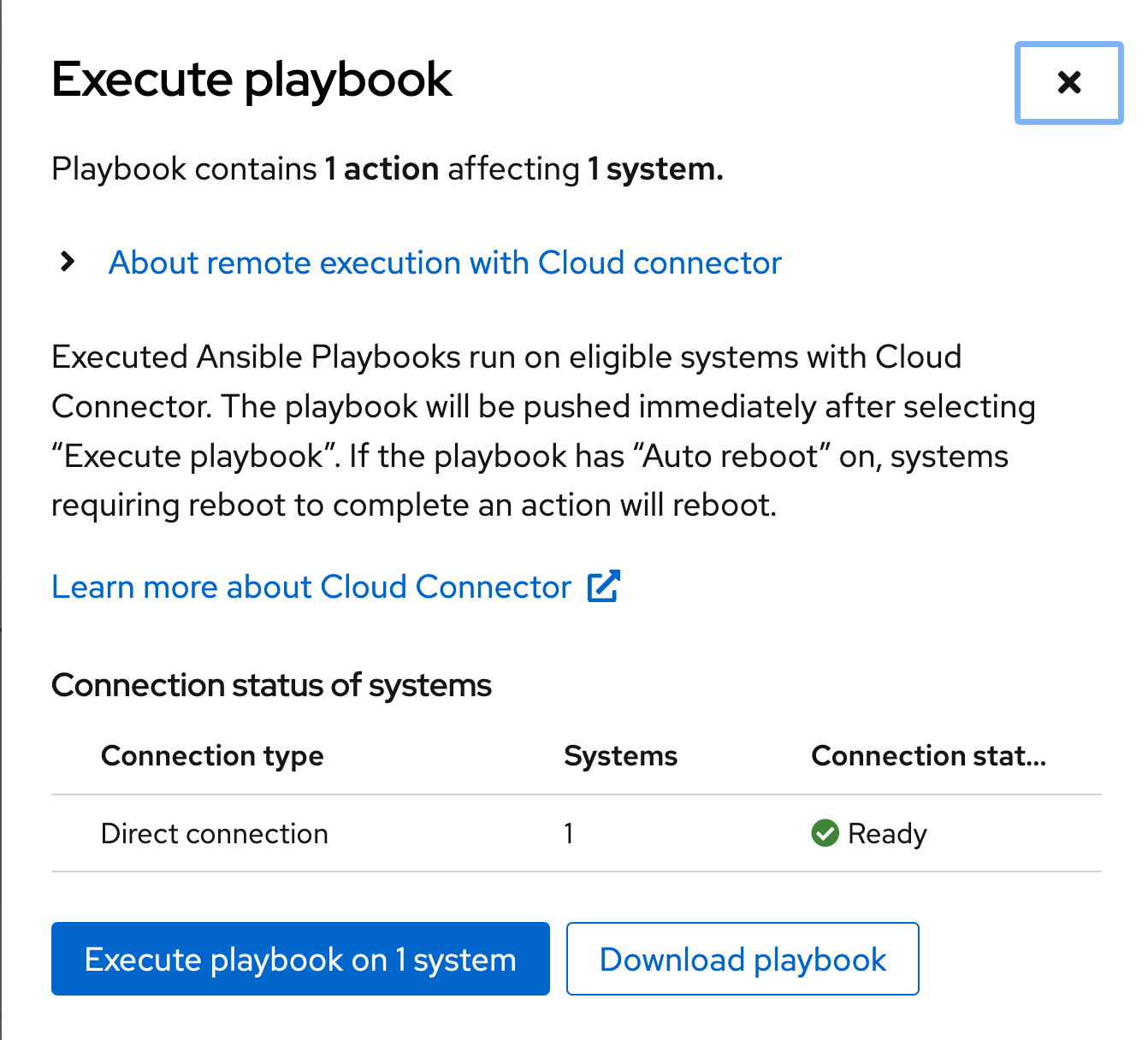
The first thing it will do is confirm my connection status - If I am connected using RHC or through a Satellite I will get a checkmark here. If not, I will be told that the system isn’t connected in a way that allows me to remediate.
You can have a mixture of connection types in a single playbook - If I had a hundred systems I might have 50 through a Satellite, 40 through RHC, and 10 not connected in a way we can remediate. In that case we would fix the 90 systems that we can fix and you would need to manually run the playbook on the remaining 10 using whatever method you deem best.
Since I’m connected and ready to go, I just click Execute playbook on this screen.
The host pulls down the playbook and runs it using Ansible. You can monitor the process right from the remediations page.
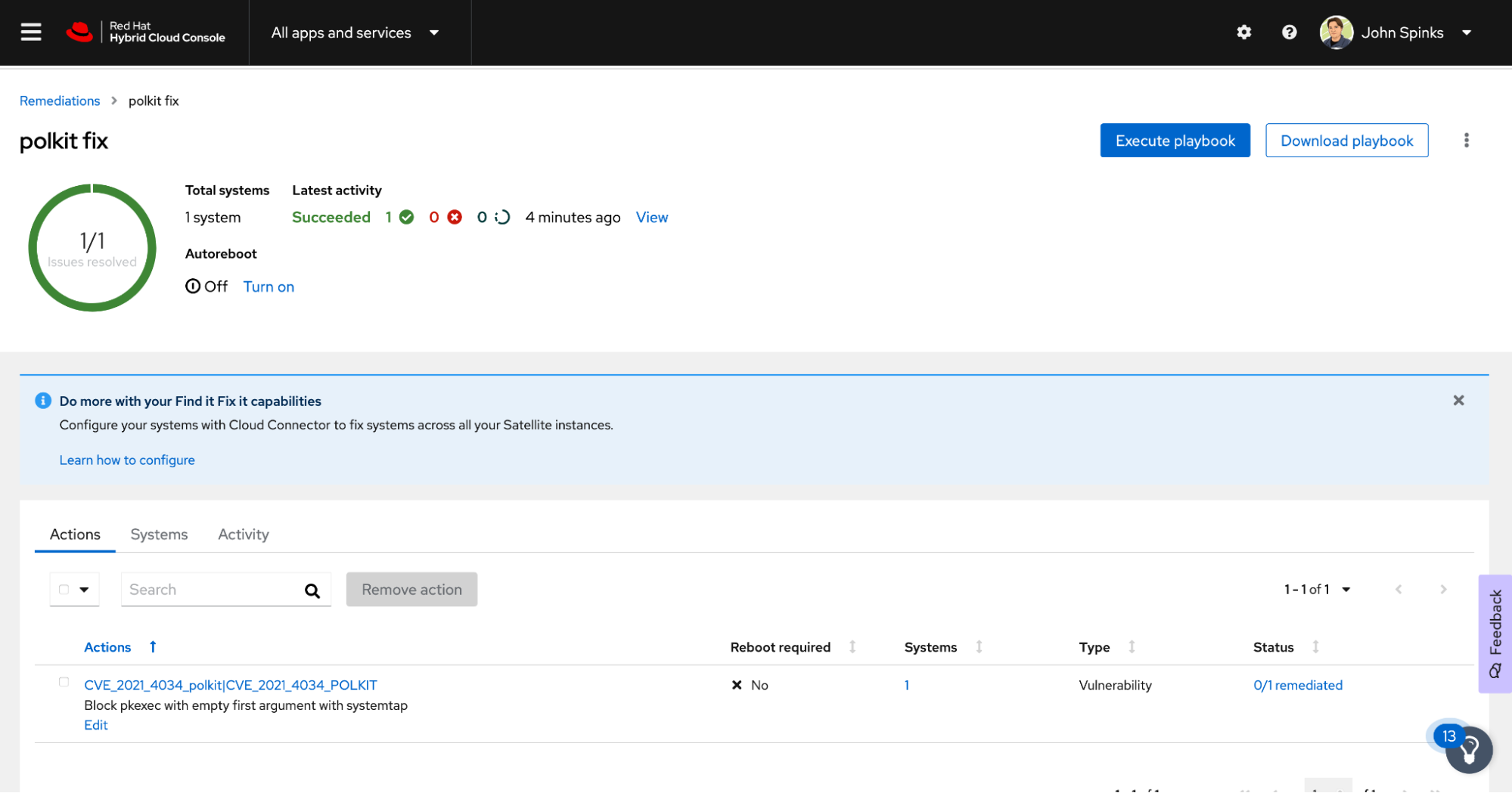
That’s it. I was able to identify my exposure, create a playbook, and run the playbook, all from one place in a matter of minutes.
Now that this is working on this test system, I’m going to go back and remediate the rest of my systems.
Summary
Insights has helped me to:
-
Identify my exposure to a vulnerability
-
Create a playbook to mitigate the exposure across a large number of systems
-
Run the playbook to complete remediation
It took me way longer to type this up than it did to complete the steps above. Insights is a part of your existing Red Hat Enterprise Linux subscriptions (as well as OpenShift and Ansible Automation Platform subscriptions) - all you have to do is turn it on.
Insights helps with more than vulnerabilities. It helps with best practice recommendations, identifying drift between systems, regulatory compliance like PCI or HIPAA, resource optimization, and much more. Check out the Level Up Hour on Red Hat Insights (E50) as one of the many places you can learn more.
Not using Insights? Learn how to get started today. Already using Insights? Review the docs above on integrating with Satellite or with RHC to take it to the next level and enable remediation from Insights.
Want to know more technical details? Check out the Insights Data & Application Security page, which includes a section on frequently asked questions.
I hope this gives you an idea of how your organization can use Red Hat Insights to shorten the time it takes to understand your level of exposure to vulnerabilities, report this information to various stakeholders, and remediate issues.
À propos de l'auteur
John Spinks is a Senior Principal Technical Marketing Manager for Red Hat. He acts as a subject matter expert for Red Hat Management products including Satellite and Insights. Previous experience includes almost 10 years as a Technical Marketing Engineer for NetApp in RTP, NC.
Plus de résultats similaires
From incident responder to security steward: My journey to understanding Red Hat's open approach to vulnerability management
Deploy Confidential Computing on AWS Nitro Enclaves with Red Hat Enterprise Linux
What Is Product Security? | Compiler
Technically Speaking | Security for the AI supply chain
Parcourir par canal
Automatisation
Les dernières nouveautés en matière d'automatisation informatique pour les technologies, les équipes et les environnements
Intelligence artificielle
Actualité sur les plateformes qui permettent aux clients d'exécuter des charges de travail d'IA sur tout type d'environnement
Cloud hybride ouvert
Découvrez comment créer un avenir flexible grâce au cloud hybride
Sécurité
Les dernières actualités sur la façon dont nous réduisons les risques dans tous les environnements et technologies
Edge computing
Actualité sur les plateformes qui simplifient les opérations en périphérie
Infrastructure
Les dernières nouveautés sur la plateforme Linux d'entreprise leader au monde
Applications
À l’intérieur de nos solutions aux défis d’application les plus difficiles
Virtualisation
L'avenir de la virtualisation d'entreprise pour vos charges de travail sur site ou sur le cloud