Did you know that Red Hat Insights for Red Hat Enterprise Linux (RHEL) can be used to help detect the presence of malware? This makes it more likely that you'll know when a RHEL system has sustained a malware attack. The effectiveness of Insights for this purpose is enhanced by threat intelligence subscriptions from IBM X-Force, in collaboration with Red Hat.
The Insights malware detection service is a monitoring and assessment tool that scans RHEL systems for the presence of known malware. The system incorporates YARA pattern-matching software and detection signatures.
Insights is a cloud-based service that can be accessed from the Red Hat customer portal. This means there is no maintenance to be done on the user's end. Simply integrate it with Insights clients, which are available for almost all subscriptions to RHEL, Red Hat OpenShift and Red Hat Ansible Automation Platform.
Insights proactively and continuously analyzes platforms and applications to help predict risks, recommend actions, track licenses and manage costs. This helps enterprises better manage their on-premise and hybrid cloud environments.
Sound good? Then I'll show you how easy it is to integrate your Red Hat environment, issue the first report on malware detection, and other useful information for smooth-running Red Hat systems.
Prerequisites
Since this is a modern solution, we will need a supported operating system.
- The operating system version must be RHEL8 or RHEL9
- The administrator must have administrative or sudo access to the system
- The Insights client package must be installed
- The environment must be registered in Insights for Red Hat Enterprise Linux
- The system must be able to access the Red Hat Cloud Console via direct internet access or HTTP proxy
- User permission on malware-detection groups, roles and members in User Access
Laboratory
We will work with an RHEL 8 system to better exemplify the reports generated. We will intentionally adjust some items to provide a better analysis by Insights.
The fully qualified domain name (FQDN) will be:
- Host: rhel8-yara-testing.rhbrlabs.com
Host
For the host, we’ll use RHEL 8.5, with no updates and Security-Enhanced Linux (SELinux) disabled. This insecure setup is necessary to generate more inputs to Insights.
- A regular update routine in a real production environment is important. Likewise SELinux should operate in Enforcing mode to increase the reliability of a production environment.
Before proceeding with the YARA installation, we need to perform three important basic tasks:
- Take care that the environment clock is always synchronized
- Set the timezone correctly
- Perform the system subscription
Basic tasks
Disable SELinux (again, in real production environments, we recommend using SELinux in Enforcing mode), and perform the basic tasks:
# sed -i s/'\=enforcing'/'\=disabled'/g /etc/selinux/config # timedatectl set-timezone America/Sao_Paulo # hostnamectl set-hostname rhel8-yara-testing.rhbrlabs.com
You may want to logout/login before performing the next steps:
# subscription-manager register --auto-attach # subscription-manager status # subscription-manager repos # dnf -y install chrony # systemctl enable --now chronyd.service # chronyc sources # reboot
Don't update the system yet!
Software installation
Now the YARA and Insights packages:
# dnf -y install yara insights-client
Only these packages are needed for the magic to happen. Very handy.
Using Insights
Let's move on to performing the basic tasks below:
- Connection test
- Registering the system in Insights
- Scanning the system for malware
Connection test
Test the connection to Insights for RHEL.
# insights-client --test-connection
Running Connection Tests...
=== Begin Upload URL Connection Test ===
Testing: https://cert-api.access.redhat.com/r/insights/uploads/
POST https://cert-api.access.redhat.com/r/insights/uploads/
HTTP Status: 200 OK
HTTP Response Text: {"request_id":"e7d200e80a","upload":{"account_number":"000000X","org_id":"1111111Y"}}
Successfully connected to: https://cert-api.access.redhat.com/r/insights/uploads/
=== End Upload URL Connection Test: SUCCESS ===
=== Begin API URL Connection Test ===
Testing: https://cert-api.access.redhat.com/r/insights/
GET https://cert-api.access.redhat.com/r/insights/
HTTP Status: 200 OK
HTTP Response Text: lub-dub
Successfully connected to: https://cert-api.access.redhat.com/r/insights/
=== End API URL Connection Test: SUCCESS ===
Connectivity tests completed successfully
See /var/log/insights-client/insights-client.log for more details.
In the example above, we can see that the system was able to connect to the Insights cloud services.
Registering the system in Insights
Register the system with Insights.
# insights-client --register Successfully registered host rhel8-yara-testing.rhbrlabs.com Automatic scheduling for Insights has been enabled. Starting to collect Insights data for rhel8-yara-testing.rhbrlabs.com Uploading Insights data. Successfully uploaded report from rhel8-yara-testing.rhbrlabs.com to account 000000X. View the Red Hat Insights console at https://console.redhat.com/insights/
System successfully registered in Insights. Now move on to the next step.
Malware scanning
Run the Insights client malware-detection collector. This operation will take a while to finish.
# insights-client --collector malware-detection Starting to collect Insights data for rhel8-yara-testing.rhbrlabs.com Writing the malware-detection app default configuration to /etc/insights-client/malware-detection-config.yml Performing a test scan of /etc/insights-client/malware-detection-config.yml and the current process (PID 5638) to verify the malware-detection app is installed and scanning correctly ... Starting filesystem scan ... Scanning specified files in /etc ... Matched rule TEST_RedHatInsightsMalwareDetection in file /etc/insights-client/malware-detection-config.yml Scan time for /etc: 0 seconds Filesystem scan time: 00:00:00 Starting processes scan ... Scanning process 5638 ... Matched rule TEST_RedHatInsightsMalwareDetection in process 5638 Scan time for process 5638: 0 seconds Processes scan time: 00:00:00 Found 2 rule matches. Red Hat Insights malware-detection app test scan complete. Test scan results are not recorded in the Insights UI (https://console.redhat.com/insights/malware) To perform proper scans, please set test_scan: false in /etc/insights-client/malware-detection-config.yml Uploading Insights data. Successfully uploaded report for rhel8-yara-testing.rhbrlabs.com.
A rule related to "TEST_RedHatInsightsMalwareDetection" will be matched, but this is intentional and nothing to worry about, as the operation was performed in "test" mode. Later on we will see how to deactivate the test mode.
The results of the initial scan may not yet appear in the detection service's Web UI, but Insights will be fully operational and update the Web UI with some information.
Go to the Insights console and check the Insights findings for your system.

Insights advisory

Vulnerabilities found
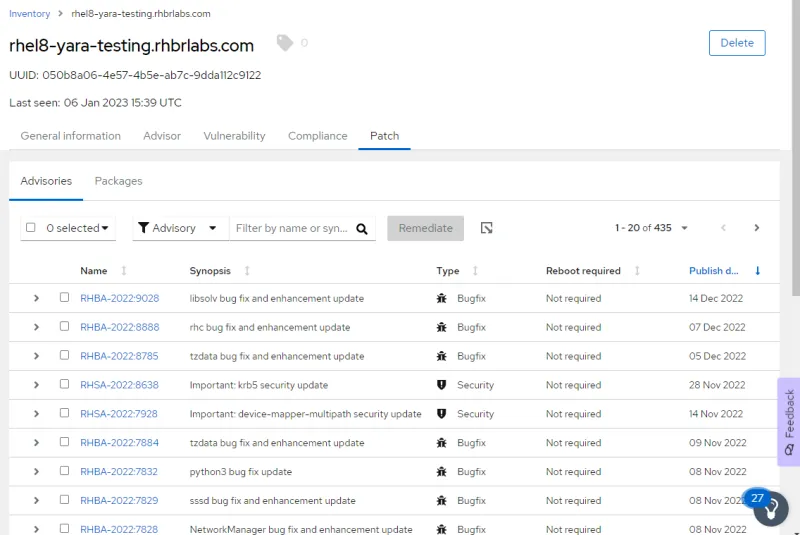
Pending patches
The collector takes the following actions during this first run:
- Creates a malware detection configuration testing file at /etc/insights-client/malware-detection-config.yml.
- Performs a test scan and uploads the results
Next, we will see how to customize the generated YAML configuration to enable other functions, as this initial scan only does simpler checks.
Edit /etc/insights-client/malware-detection-config.yml and set the test_scan option to false.
# sed -i s/'test_scan:\ true'/'test_scan:\ false'/g /etc/insights-client/malware-detection-config.yml
There are other YAML configuration options you can explore, but for now, we'll just stick with what we have.
Now perform a full filesystem scan, by re-running the Insights client collector:
# insights-client --collector malware-detection Starting to collect Insights data for rhel8-yara-testing.rhbrlabs.com Skipping missing filesystem_scan_exclude item: '/cgroup' Skipping missing filesystem_scan_exclude item: '/selinux' Skipping missing filesystem_scan_exclude item: '/net' Excluding specified filesystem items: ['/proc', '/sys', '/mnt', '/media', '/dev'] Starting filesystem scan ... Scanning files in /.autorelabel ... Scan time for /.autorelabel: 0 seconds Scanning files in /.bash_history ... Scan time for /.bash_history: 0 seconds Scanning files in /boot ... Scan time for /boot: 0 seconds Scanning files in /etc ... Scan time for /etc: 0 seconds Scanning files in /home ... Scan time for /home: 0 seconds Scanning files in /opt ... Scan time for /opt: 0 seconds Scanning files in /root ... Scan time for /root: 0 seconds Scanning files in /run ... Scan time for /run: 0 seconds Scanning files in /srv ... Scan time for /srv: 0 seconds Scanning specified files in /tmp ... Scan time for /tmp: 0 seconds Scanning files in /usr ... Scan time for /usr: 65 seconds Scanning specified files in /var ... Scan time for /var: 4 seconds Filesystem scan time: 00:01:11 No rule matches found. Uploading Insights data. Successfully uploaded report for rhel8-yara-testing.rhbrlabs.com.
Logs
Check the Insights and malware detection logs at: /var/log/insights-client/insights-client.log

Insights and malware detection logs
View results of malware-detection system scans on the Hybrid Cloud Console
Prerequisites:
- You must be logged into the Hybrid Cloud Console (https://console.redhat.com)
- You are a member of a Hybrid Cloud Console User Access group with the Malware detection administrator or Malware detection viewer role.
NOTE: An Organization Administrator must create malware-detection groups in Red Hat Hybrid Cloud Console > User Access > Groups and add the necessary malware-detection roles and members (registered users on the account).
Navigate to Red Hat Enterprise Linux > Malware > Systems.
In the Insights dashboard in the customer portal, we can see the malware scan results as well as other health and safety recommendations for the environment:

Malware scan results
IMPORTANT: There is no "default-group" role for malware-detection service users. For users to view data or control settings in the malware-detection service, they must be members of one or more User Access groups with one of the following roles:
- Malware detection viewer
- Malware detection administrator
In the malware-detection service UI, User Access-authorized administrators and viewers can:
- See the list of signatures against which their RHEL systems are scanned
- See aggregate results for all RHEL systems with malware-detection enabled in the Insights client
- See results for individual systems
- Know when a system shows evidence of the presence of malware
These features give security threat assessors and IT incident-response teams valuable information to help prepare a response.
Useful links
저자 소개
Andre Rocha is a Consultant at Red Hat focused on OpenStack, OpenShift, RHEL and other Red Hat products. He has been at Red Hat since 2019, previously working as DevOps and SysAdmin for private companies.
채널별 검색
오토메이션
기술, 팀, 인프라를 위한 IT 자동화 최신 동향
인공지능
고객이 어디서나 AI 워크로드를 실행할 수 있도록 지원하는 플랫폼 업데이트
오픈 하이브리드 클라우드
하이브리드 클라우드로 더욱 유연한 미래를 구축하는 방법을 알아보세요
보안
환경과 기술 전반에 걸쳐 리스크를 감소하는 방법에 대한 최신 정보
엣지 컴퓨팅
엣지에서의 운영을 단순화하는 플랫폼 업데이트
인프라
세계적으로 인정받은 기업용 Linux 플랫폼에 대한 최신 정보
애플리케이션
복잡한 애플리케이션에 대한 솔루션 더 보기
가상화
온프레미스와 클라우드 환경에서 워크로드를 유연하게 운영하기 위한 엔터프라이즈 가상화의 미래
