In this post I will go through how you can integrate and send policy alert notifications from Red Hat Advanced Cluster Security for Kubernetes (RHACS) to ServiceNow.
Red Hat Advanced Cluster Security supports a number of specific notifier integrations today, including Slack, Jira, Splunk, syslog and email. Although ServiceNow is not currently in that list, it is possible to use generic webhooks to create this integration. Using this option together with the ServiceNow feature Scripted REST API will allow you to send security alert notifications also to ServiceNow.
This guide will demonstrate the following:
-
In ServiceNow: How to configure and prepare a Scripted REST API service as a webhook receiver
-
In Red Hat Advanced Cluster Security: How to configure a notifier integration to use the ServiceNow Scripted REST API
Let’s have a look at how to create this integration!
Prerequisites
There are a few things that need to be in place before you start:
-
Access to a Red Hat OpenShift cluster (version 4.8+)
-
Red Hat Advanced Cluster Security for Kubernetes installed
-
Access to a ServiceNow instance with permissions to create a Scripted REST API service
This guide will not cover the installation of Red Hat OpenShift or Red Hat Advanced Cluster Security. You can get your OpenShift cluster at try.openshift.com and explore the documentation for more information.
ServiceNow REST API configuration
With Red Hat OpenShift and Red Hat Advanced Cluster Security installed, let’s start with configuring a REST API Service to use in ServiceNow.
Logged into ServiceNow, navigate to Scripted REST APIs under System Web Services -> Scripted Web Services and click New.
Add a Name, an API ID and click Submit to create the service.

Figure 1: New Scripted REST Service in ServiceNow
With the REST service created, it’s time to configure the REST resource for alerts by adding a script to handle the REST API request and response.
To demonstrate the integration, this example uses a simplified script that takes the request, does some simple parsing and logs the alert information in ServiceNow.
This script can later be extended to handle actions on the different ServiceNow records you need using the standard ServiceNow API.
Locate the newly created service (rhacs from the example above) from the list of services presented, then under Resources click New.
Configure the resource with the following information as an example:
Name: alert
HTTP method: POST
Script:
(function process(/*RESTAPIRequest*/ request, /*RESTAPIResponse*/ response) { var data = JSON.parse(request.body.dataString); var deployment = data.alert.deployment; var policy_name = data.alert.policy.name; // Create example incident record var incident = new GlideRecord('incident'); incident.initialize(); incident.short_description = 'Automated incident created from Advanced Cluster Security'; incident.description = "Deployment '" + deployment.name + "' in namespace '" + deployment.namespace + "' violated policy ''" + policy_name + "'"; incident.insert(); // Log data from policy violation gs.info("Deployment '" + deployment.name + "' in namespace '" + deployment.namespace + "' violated policy ''" + policy_name + "'"); // Log complete object for debug gs.info(JSON.stringify(data)); })(request, response);
Note: To create an authenticated endpoint, make sure Requires Authentication and Requires ACL authorization are selected.

Figure 2: New Scripted REST Resource in ServiceNow
With the alert resource created, take a note of the Resource path (i.e. /api/xx/rhacs) and the ServiceNow instance name for the next step.

Figure 3: Resource API definition in ServiceNow
With this step done you now have a REST API endpoint available in ServiceNow to use in Red Hat Advanced Cluster Security. This endpoint will be used in the next step, when configuring a Notifier integration in Red Hat Advanced Cluster Security.
Create notifier integration in Red Hat Advanced Cluster Security
With a REST API endpoint configured in ServiceNow, it’s time to create a Generic Webhook notifier integration in Red Hat Advanced Cluster Security.
Navigate to the Integrations page: Platform Configuration -> Integrations
In the Notifier integrations section, select the Generic Webhook option and configure the endpoint using the ServiceNow instance and the REST API resource path from the previous step.
Integration name: ServiceNow
Endpoint: https://<servicenow-instance>/api/<rest-api-resource-path>

Figure 4: Generic Webhook integration in Red Hat Advanced Cluster Security
See Red Hat Advanced Cluster Security documentation for more information on generic Webhook integrations.
When configuring the Generic Webhook you can also add authentication details for ServiceNow. Add username and password if using basic auth or add additional headers with an access token if using an OAuth Client in ServiceNow. It's also possible to add extra fields to be included in the JSON payload sent from Red Hat Advanced Cluster Security.
Example:

Figure 5: Authentication configuration for Webhook
See ServiceNow product documentation for further information on how to set up OAuth.
Attach notifier to policies
With the notifier integration created in Red Hat Advanced Cluster Security, the next step is to attach the notifier to the policies of your choice.
Navigate to Platform Configuration -> Policy Management in Red Hat Advanced Cluster Security
-
Select the policy to update
-
Select Action -> Edit Policy
-
Check the ServiceNow integration under Attach notifiers
-
If no other changes to the policy are needed, simply Next-Next-Next-Save
-

Figure 6: Attach notifier to policy
With the policy updated it is now configured so that whenever a policy is violated an alert is triggered and sent to the notifier.
Before validating the integration and the alert in ServiceNow, verify that the policy selected actually has been violated and that the policy status is set to FAIL.
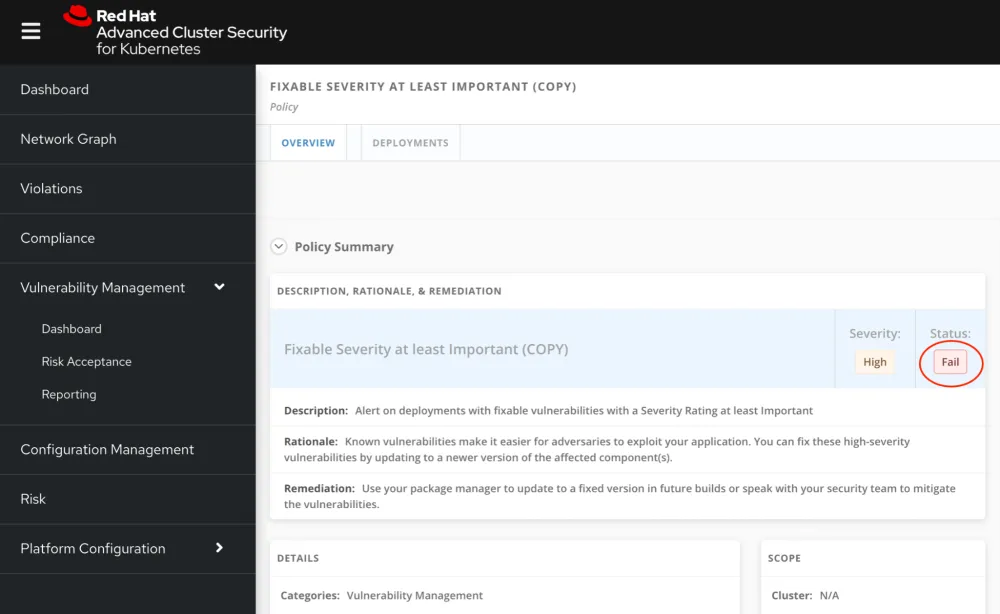
Figure 7: Policy status in Red Hat Advanced Cluster Security
Verify integration in ServiceNow
When a policy in Red Hat Advanced Cluster Security configured with the notifier integration has been violated, an alert should have been triggered and sent to ServiceNow using the configured Scripted REST API endpoint.
Remember the example script from above? It included examples to create incident records, print deployment information and to send the body of the request to the ServiceNow Log.
With the integration working as expected, you would now see automatic incidents being created and the JSON data from the webhook when searching the log. The data will include a v1.Alert object and include any custom fields configured.

Figure 8: ServiceNow incidents created with Red Hat Advanced Cluster Security alert data
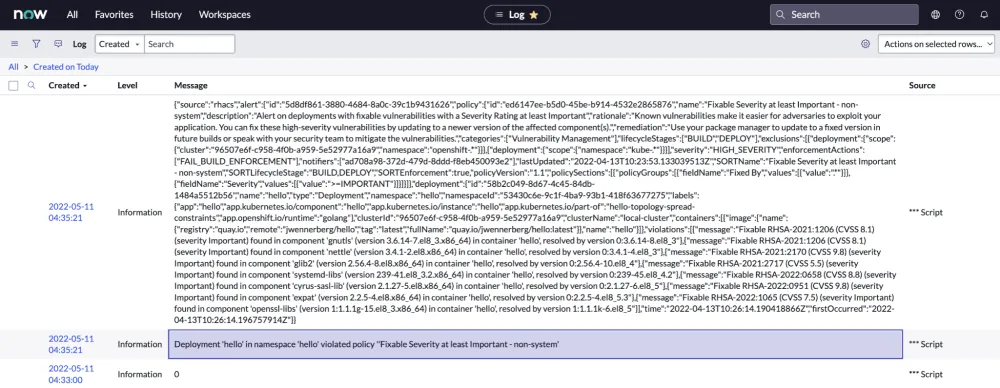
Figure 9: Red Hat Advanced Cluster Security alert data in ServiceNow log
There you go! Red Hat Advanced Cluster Security alert data ready for use with your different ServiceNow records!
Summary
In this post we looked at integrating Red Hat Advanced Cluster Security with ServiceNow. We configured policies in Red Hat Advanced Cluster Security to forward alerts to ServiceNow whenever the policies are violated.
This enables a flexible way to get the security findings surfaced by Red Hat Advanced Cluster Security into your existing processes. With the example policy used in this guide, a CMDB or Problem record could be updated with all vulnerabilities found, but other policies in Red Hat Advanced Cluster Security would also enable additional flows to increase the security posture of the environment.
Red Hat Advanced Cluster Security ability to analyze runtime activity would for example make it possible to automatically create an incident record whenever an anomalous activity is detected. Policies in Red Hat Advanced Cluster Security and the ServiceNow Scripted REST API service can easily be customized to fit your requirements.
To learn more, check out Scripted REST API examples from ServiceNow and the guide on how to manage security policies with Red Hat Advanced Cluster Security.
Sobre el autor
Johan Wennerberg is a Solution Architect working with Enterprise Accounts at Red Hat, with a focus on OpenShift, Kubernetes, Linux and automation. Previously a Senior Consultant at Red Hat.
Más como éste
Deploy Confidential Computing on AWS Nitro Enclaves with Red Hat Enterprise Linux
Red Hat OpenShift sandboxed containers 1.11 and Red Hat build of Trustee 1.0 accelerate confidential computing across the hybrid cloud
What Is Product Security? | Compiler
Technically Speaking | Security for the AI supply chain
Navegar por canal
Automatización
Las últimas novedades en la automatización de la TI para los equipos, la tecnología y los entornos
Inteligencia artificial
Descubra las actualizaciones en las plataformas que permiten a los clientes ejecutar cargas de trabajo de inteligecia artificial en cualquier lugar
Nube híbrida abierta
Vea como construimos un futuro flexible con la nube híbrida
Seguridad
Vea las últimas novedades sobre cómo reducimos los riesgos en entornos y tecnologías
Edge computing
Conozca las actualizaciones en las plataformas que simplifican las operaciones en el edge
Infraestructura
Vea las últimas novedades sobre la plataforma Linux empresarial líder en el mundo
Aplicaciones
Conozca nuestras soluciones para abordar los desafíos más complejos de las aplicaciones
Virtualización
El futuro de la virtualización empresarial para tus cargas de trabajo locales o en la nube
