In this post:
-
See how the CIA triad, a DevSecOps approach, and a unified automation strategy can help you implement a security-focused hybrid cloud plan.
-
Learn about how products like Red Hat Enterprise Linux and Red Hat Advanced Cluster Security for Kubernetes can help you minimize operational risk.
It goes without saying that no matter where you are in your hybrid cloud journey, security is a primary concern. In this post, we'll look at improving your hybrid cloud security to try to avoid data breaches.
What are some security challenges in hybrid cloud environments?
Some security challenges in hybrid cloud environments include:
-
Securing your data: Since the same data will either be in transit or at rest at different moments in time (and across different locations), data exposure is a real possibility in hybrid cloud environments.
-
Disconnected teams: When development, operations and security teams take a siloed approach to security in hybrid cloud environments, it can result in security gaps, duplicated efforts and more.
-
Streamlining compliance and governance: Manually implementing regulatory security baselines, preparing for security audits and checking your distributed environments for compliance can cost you time and money.
Lagging behind in any of these three areas can open the door to unauthorized users hoping to gain access to sensitive data and internal resources.
So what can be done?
3 tips for deploying a security-focused hybrid cloud strategy
1. Make sure your data addresses the CIA triad
In hybrid cloud environments, your data is not only at rest, in motion, or in action in your on-premise datacenter, but also across one or more public clouds. This makes securing your data all the more critical—and complicated.
We can work towards data security by following what’s known as the CIA triad, or three key aspects of data security:
-
Confidentiality: Restricting data access to those who are authorized to use it.
-
Integrity: Ensuring that data has not been altered or deleted by an unauthorized party.
-
Availability: Ensuring that data will be available when it’s needed.
But what does addressing the CIA triad look like in hybrid cloud environments?
It will look different depending on where your data is in its life cycle, but take data at rest for example. Ensuring confidentiality in data at rest could look like encrypting your data, and integrity could look like verifying that encrypted data. Availability could mean making sure that data is backed up.
Red Hat can help you address the CIA triad. Our products built from Red Hat Enterprise Linux (RHEL) inherit core security features such as standardized crypto policies and Security-Enhanced Linux (SELinux).
For example, Red Hat Openshift Data Foundation, our hybrid cloud storage platform for Red Hat OpenShift, leverages the certified, independently validated cryptography provided by RHEL to allow you to encrypt data at rest or in motion for your hybrid cloud.
2. Unify security across your organization using a DevSecOps approach
In DevSecOps, security, development and operations teams share the responsibility of integrating security throughout the entire IT life cycle. Implementing DevSecOps means thinking about application and infrastructure security from the start.
DevSecOps is very much your friend when it comes to deploying a security-focused hybrid cloud—but what does it actually look like in hybrid cloud environments?
First, understand that culture should be at the front of mind when it comes to DevSecOps. Some aspects of a healthy DevSecOps culture in hybrid cloud environments include:
-
Training: Training developers on secure coding practices.
-
Transparency: Eliminating silos and providing visibility into Ops tools.
-
Shared goals: Defining and measuring KPIs throughout the pipeline.
-
Security automation: Automating security at every point in the life cycle.
While culture is important, you’ll also want to make sure that your hybrid cloud technology simplifies DevSecOps as much as possible.
This means that, since containers and Kubernetes are what enable many hybrid clouds today, you need a security platform that both protects your entire Kubernetes environment and makes DevSecOps easier.
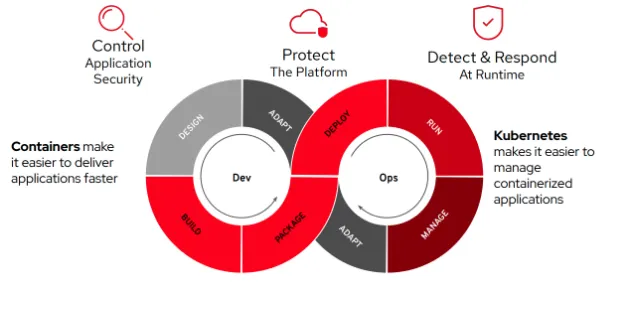
Red Hat Advanced Cluster Security for Kubernetes, our enterprise-ready, Kubernetes-native container security solution, integrates with DevOps and security tools to help you mitigate threats and enforce security policies that minimize operational risk to your applications.
Another Red Hat product that can help simplify a DevSecOps approach is Red Hat OpenShift Platform Plus, which brings together tools you need to manage multiple clusters in a hybrid cloud environment.
3. Implement a unified automation strategy to streamline compliance and governance
Automation helps you reduce risk associated with human errors, helps to bake security in from the start, and allows for everything-as-code. With automation, you can streamline your compliance and governance with:
-
Traceability and repeatability for compliance.
-
Consistent configuration and management across a multivendor environment.
-
Automated rollout of policy, system updates and firewalls across the entire network
In an ideal world, you would have a common automation language across the hybrid cloud stack, one that is simple for your existing DevSecOps teams and your new hires to learn. Having a common automation language provides a layer of interoperability and collaboration for all IT teams.
With Red Hat Ansible Automation Platform, you can take advantage of a leading automation platform that includes a curated collection of modules, roles and playbooks to help investigate and respond to security threats.
Learn more about how easy provisioning cloud infrastructures with Ansible can be.
Conclusion
Security is a big concern no matter where you are in your hybrid cloud journey, so practicing hybrid-cloud security hygiene is important to responding to vulnerabilities in software.
Whether it be securing data, connecting teams or streamlining compliance and governance, it can be challenging to implement healthy hybrid cloud security measures—but Red Hat’s portfolio can help you address these concerns.
We gave a few examples of how Red Hat Openshift Data Foundation, Red Hat Advanced Cluster Security for Kubernetes, and Red Hat Ansible Automation Platform can help you deploy a security-focused hybrid cloud.
Sobre el autor
Bill Cozens is a recent UNC-Chapel Hill grad interning as an Associate Blog Editor for the Red Hat Blog.
Más como éste
IT automation with agentic AI: Introducing the MCP server for Red Hat Ansible Automation Platform
Introducing OpenShift Service Mesh 3.2 with Istio’s ambient mode
Data Security 101 | Compiler
AI Is Changing The Threat Landscape | Compiler
Navegar por canal
Automatización
Las últimas novedades en la automatización de la TI para los equipos, la tecnología y los entornos
Inteligencia artificial
Descubra las actualizaciones en las plataformas que permiten a los clientes ejecutar cargas de trabajo de inteligecia artificial en cualquier lugar
Nube híbrida abierta
Vea como construimos un futuro flexible con la nube híbrida
Seguridad
Vea las últimas novedades sobre cómo reducimos los riesgos en entornos y tecnologías
Edge computing
Conozca las actualizaciones en las plataformas que simplifican las operaciones en el edge
Infraestructura
Vea las últimas novedades sobre la plataforma Linux empresarial líder en el mundo
Aplicaciones
Conozca nuestras soluciones para abordar los desafíos más complejos de las aplicaciones
Virtualización
El futuro de la virtualización empresarial para tus cargas de trabajo locales o en la nube
