In this post:
-
Explains the concept of data controls.
-
Shows how data controls integrate into the framework at the container orchestration and cluster level.
-
Pointers to Red Hat partners that can help with data controls.
Data controls help protect data integrity and prevent unauthorized data disclosure for stored data and data in motion. In this post we'll dive deeper into the concepts of data controls and how they fit into the DevSecOps framework.
July is “Data Controls” month in Red Hat’s monthly Security series! Since March 2021, the Red Hat Security Ecosystem team has published monthly articles and videos on DevOps Security topics to help you learn how Red Hat can help you master the practice called DevSecOps.
By explaining how to assemble Red Hat products and introducing our security ecosystem partners, we aim to aid in your journey to deploying a comprehensive DevSecOps solution.
Data controls defined
Data controls are typically implemented in a running Kubernetes cluster, and the goal is to provide a defense in depth approach to protect sensitive data either at rest or in motion. The following security methods make up the Data Controls category:
-
Data encryption: Provides data cryptography, tokenization, data masking, and key management capabilities to help prevent unauthorized disclosure of data in databases, files, and containers.
-
Data protection: Discovers and classifies data and monitors and audits activity to help protect sensitive data and improve compliance.
Data controls integrated in DevSecOps
As pictured in the DevSecOps framework below, data controls integrations are typically found on the right side of the DevSecOps life cycle in a running cluster. The table that follows details some, but not all, of the common integrations to consider for Data Controls.
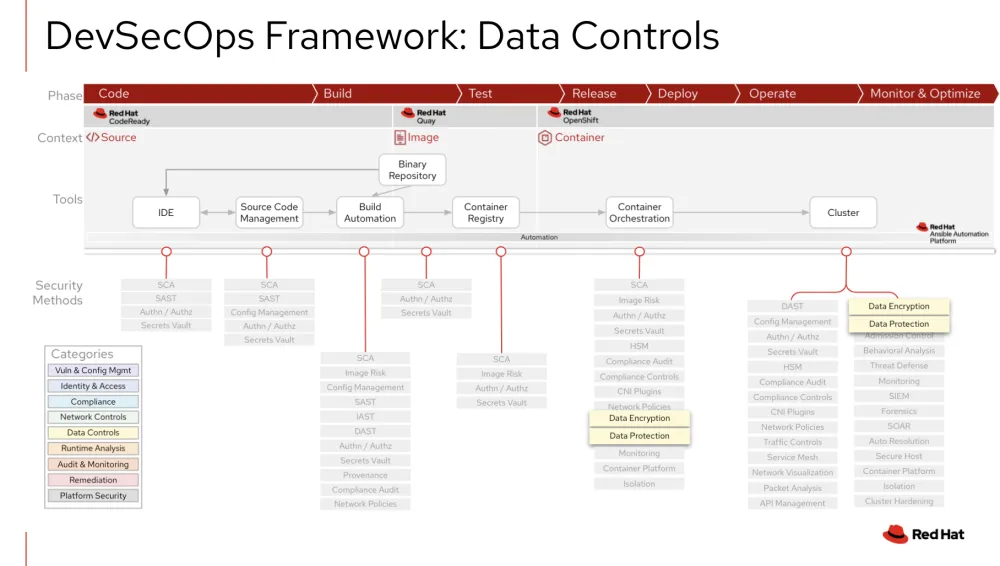
|
Integration Point |
Description |
|
Container Orchestration and Cluster |
Data Control integrations in both container orchestration and the running cluster provide the same functionality as described below. Whether you are testing, releasing, deploying, operating or monitoring the cluster, these controls need to be considered. With Red Hat OpenShift Container Platform, you can enable etcd encryption, which provides an additional layer of data security for Secrets, Config maps, Routes, and OAuth tokens. This can help protect data if it's exposed to the wrong parties. Data in-transit encryption is all about certificates and securing the ingress and egress traffic within a cluster. One of the many certificate types to address in the default API server certificate provided by the OpenShift Container Platform. For example, if you need clients outside of the cluster to access any running web applications, you’ll need to replace the certificate with a Certificate Authority that the client's trust. In order to centrally manage, store and further protect OpenShift keys and certificates for data controls, you’ll want to extend and enhance OpenShift Container Platform’s data security capabilities with certified partner software that centralizes data encryption across environments and adds layers of data protection. Red Hat’s partner ecosystem can help add:
Data protection in a running cluster can also include discovering where sensitive data exists in your cluster, as well as analyzing data risks and uncovering suspicious activity against the data in rest. |
Enhance and extend Data Controls with Red Hat partners
Combining Red Hat OpenShift Container Platform Data Control features with Red Hat’s certified ecosystem security partners can help your organization's DevSecOps practice.
If you are looking to enhance and extend Red Hat’s security capabilities in Data Controls, take a look at the following Red Hat Partners:
-
Zettaset’s certified software, product brief and webinar.
-
Thales’ Red Hat solution brief and webinar.
Sull'autore
Dave Meurer currently serves as a Principal Solution Architect on the Red Hat Global Partner Security ISV team, where he owns technical relationships and evangelism with security independent software vendor partners of Red Hat. Before joining Red Hat, he spent nine years in the Application Security industry with Synopsys and Black Duck, where he served in similar roles as the director of technical alliances and sales engineering.
Meurer also worked for Skyway Software, HSN.com, and Accenture in various management and application development roles. When he’s not thinking about Kubernetes, security, and partners, he enjoys being the VP Sales of North Central Tampa for his wife (the CEO) and 5 kids (Inside Sales).
Altri risultati simili a questo
Red Hat to acquire Chatterbox Labs: Frequently Asked Questions
Attestation vs. integrity in a zero-trust world
What Is Product Security? | Compiler
Technically Speaking | Security for the AI supply chain
Ricerca per canale
Automazione
Novità sull'automazione IT di tecnologie, team e ambienti
Intelligenza artificiale
Aggiornamenti sulle piattaforme che consentono alle aziende di eseguire carichi di lavoro IA ovunque
Hybrid cloud open source
Scopri come affrontare il futuro in modo più agile grazie al cloud ibrido
Sicurezza
Le ultime novità sulle nostre soluzioni per ridurre i rischi nelle tecnologie e negli ambienti
Edge computing
Aggiornamenti sulle piattaforme che semplificano l'operatività edge
Infrastruttura
Le ultime novità sulla piattaforma Linux aziendale leader a livello mondiale
Applicazioni
Approfondimenti sulle nostre soluzioni alle sfide applicative più difficili
Virtualizzazione
Il futuro della virtualizzazione negli ambienti aziendali per i carichi di lavoro on premise o nel cloud
