At Red Hat OpenShift Commons Gathering in Atlanta on November 10, 2025, Satish Puranam, Director of Cloud and Developer Experience at Ford, and Sitaram Iyer, VP of Emerging Technologies at CyberArk, outlined how Ford manages over 200 Red Hat OpenShift clusters amid a complex digital transition. Their strategy relies on a single, non-negotiable mandate: everything must be keyless.

Image 1: From left, Satish Puranam, Director of Cloud and Developer Experience
at Ford, and Sitaram Iyer, VP of Emerging Technologies at CyberArk.
To achieve this scale, Ford has abandoned static secrets entirely, implementing 100% identity-driven automation and Policy as Code (PoC) enforcement directly on the Kubernetes platform.
Managing 200+ clusters
Ford’s Red Hat OpenShift footprint spans diverse workloads, from consumer-facing applications to highly regulated manufacturing and warranty systems. This highly dynamic environment requires clusters to be regularly spun up and torn down, often pushing core Kubernetes limits (such as etcd capacity) and necessitating constant defragmentation or provisioning of new clusters.
To manage this scale, Ford imposes strict guardrails and standardizes on Red Hat OpenShift across its multicloud and multi-datacenter infrastructure.
As Satish noted, "Our decades-long journey is all about hiding complexity and barriers for the developer. You learn it once, use it over and over again, and it scales very well. It allows us to actually update and upgrade our systems at a rapid clip."
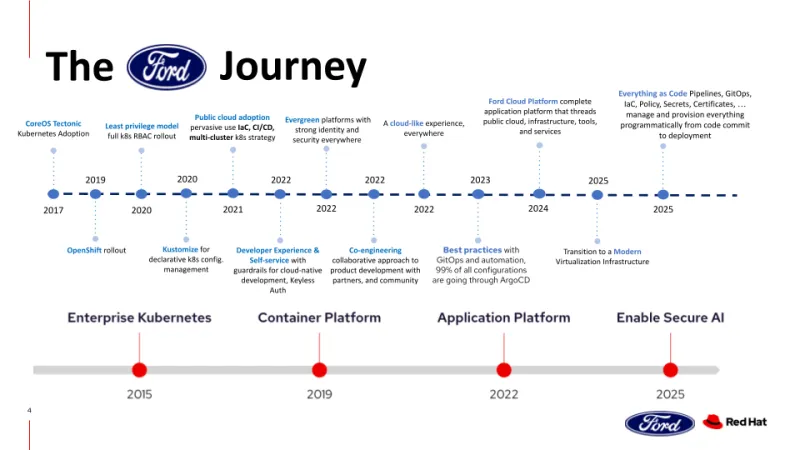
Image 2: Ford’s journey with Red Hat OpenShift
By standardizing the platform, Ford can upgrade systems rapidly without burdening teams with infrastructure friction.
Automation and identity: The keyless mandate
Ford’s scaling strategy eliminates long-lived, static credentials, or "secrets," in favor of 100% automated machine identity.
Born from a need to eliminate outages caused by expired certificates, and working closely with
partners like Red Hat and CyberArk, Ford implemented a fully automated X.509 lifecycle using cert-manager across the entire Red Hat OpenShift estate. Trust starts with a federated source of identity, typically Entra ID via OpenID Connect (OIDC). Every application, product, or project is assigned a specific identity that federates across ecosystems, including cloud services. The automation is resilient enough to support certificates with just one-hour validity periods. Because signing certificate private keys never leave the component, the risk of credential theft is drastically reduced.
Governance: PoC and admission control
Ford enforces a strict “security-first” architecture through automated governance. The guiding principle is clear: "If it’s not in code, it’s not in our platform." To achieve this, Ford takes advantage of a PoC approach using Kyverno and enforced by Kubernetes admission controllers. This setup preemptively blocks non-compliant configurations before they ever reach the cluster. Simple rules, like "do not run as root" or "do not run singletons," are automatically enforced before a workload ever makes it into the cluster. By stopping misconfigurations upstream ("If you do not allow bad things to happen, you don't have to worry about the consequences"), the infrastructure is designed to degrade gracefully rather than fail catastrophically.
Building the foundational infrastructure for AI
While the presentation avoided a lot of AI hype, Ford’s work serves as the necessary prerequisite for safe AI adoption. Successful AI agents require a foundational infrastructure that is automated, self-healing, and consistently up-to-date (such as running Red Hat OpenShift 4.20). AI workloads are treated exactly like other containerized workloads: they must adhere to the same keyless policies and possess well-governed, short-lived identities.
Ford’s deployment of Red Hat OpenShift proves that combining automation with zero trust principles is the only viable path to operating true cloud scale.
Ready to build your own keyless, automated Red Hat OpenShift platform?
Understanding how to manage machine identities at this scale is crucial for any cloud-native organization. Discover the specific tools and methods behind Ford’s security strategy by reviewing these resources:
- Learn more about the security capabilities in “A layered approach to container and Kubernetes security.” Explore cert-manager, the open source tool used by Ford to automate X.509 certificate management within Kubernetes and OpenShift.
- Watch the session from OpenShift Commons in Atlanta.
Read how Ford is prepping its cloud and infrastructure for AI in this TechTarget article.
Produkttest
Red Hat Learning Subscription | Testversion
Über den Autor
Debbie Margulies is a principal product marketing manager for Red Hat OpenShift and has been at Red Hat since 2019 through the acquisition of StackRox.
Ähnliche Einträge
F5 BIG-IP Virtual Edition is now validated for Red Hat OpenShift Virtualization
More than meets the eye: Behind the scenes of Red Hat Enterprise Linux 10 (Part 4)
Can Kubernetes Help People Find Love? | Compiler
Scaling For Complexity With Container Adoption | Code Comments
Nach Thema durchsuchen
Automatisierung
Das Neueste zum Thema IT-Automatisierung für Technologien, Teams und Umgebungen
Künstliche Intelligenz
Erfahren Sie das Neueste von den Plattformen, die es Kunden ermöglichen, KI-Workloads beliebig auszuführen
Open Hybrid Cloud
Erfahren Sie, wie wir eine flexiblere Zukunft mit Hybrid Clouds schaffen.
Sicherheit
Erfahren Sie, wie wir Risiken in verschiedenen Umgebungen und Technologien reduzieren
Edge Computing
Erfahren Sie das Neueste von den Plattformen, die die Operations am Edge vereinfachen
Infrastruktur
Erfahren Sie das Neueste von der weltweit führenden Linux-Plattform für Unternehmen
Anwendungen
Entdecken Sie unsere Lösungen für komplexe Herausforderungen bei Anwendungen
Virtualisierung
Erfahren Sie das Neueste über die Virtualisierung von Workloads in Cloud- oder On-Premise-Umgebungen
