Most of the Red Hat Enterprise Linux (RHEL) system administrators I talk to are looking for ways to further automate tasks in order to save time and make their systems more consistent—this can lead to better reliability and improve security in the environment.
RHEL System Roles Powered by Ansible is a feature introduced in RHEL 7.4 as a technology preview, and became a supported feature in RHEL 7.6. These system roles allow you to configure several aspects of RHEL: SELinux, kdump, network configuration, and time synchronization. As of RHEL 7.7, a Postfix system role is also available as a technology preview.
Using RHEL System Roles Powered by Ansible allows you to automate these configurations across your environment. In addition, system roles provide a consistent configuration interface across major RHEL versions. You can use the same system roles to automate the configuration on RHEL 6.10 or later, RHEL 7 and RHEL 8 systems, even when the underlying technologies change between versions.
For example, for time synchronization, rather than having to learn how to configure ntp on RHEL 6 and how to configure chrony on RHEL 7 and RHEL 8, you just need to know how to use the time synchronization system role. The system role will automatically translate that configuration to ntp on RHEL 6 and chrony on RHEL 7 and 8. This makes management easier and saves time, especially in environments with a mixture of RHEL 6, RHEL 7, and RHEL 8.
You can use RHEL System Roles from the command line by following the steps listed in this knowledgebase article. For Satellite customers, you can also manage systems with RHEL System Roles from within Satellite. This post will focus on the second option, and go through an example of configuring SELinux on Satellite clients with RHEL System Roles. We will utilize Advanced Ansible variables introduced in Satellite 6.6, so following these steps will require a Satellite Server running version 6.6 or later.
Getting Started with RHEL System Roles in Satellite
The first step to using RHEL System Roles in Satellite is to get the rhel-system-roles package installed onto the Satellite Server. To do this, first enable the RHEL 7 extras repository with the following command:
# subscription-manager repos --enable=rhel-7-server-extras-rpms
We’ll then install the rhel-system-roles package using the satellite-maintain command shown below on each Satellite and Capsule Server in the environment. Note that the satellite-maintain command runs satellite-installer after the package is installed, which will cause a brief outage on the Satellite and Capsule Servers as the services are restarted.
# satellite-maintain packages install rhel-system-roles
Next, log into the Satellite web interface, go to the Configure menu, and select Roles under the Ansible header. Then click the button Import from <Satellite hostname>.
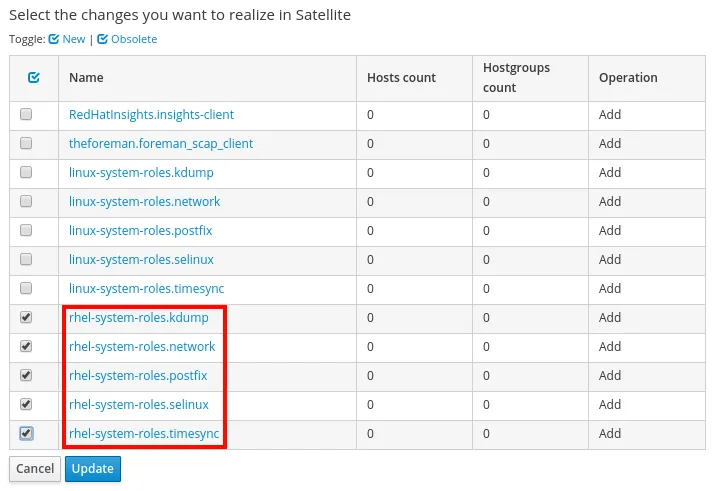
Satellite will show a list of the roles available to be imported. Note that there are both linux-system-roles and rhel-system-roles listed for each of the five system roles. On the filesystem, under /usr/share/ansible/roles/, the linux-system-roles are simply symbolic links to the rhel-system-roles. In order to avoid duplication on the Satellite server, I would recommend only importing the rhel-system-roles by checking their boxes and clicking Update. You can select all five system roles, or leave some of them off if you won’t be using them in your environment.
Next we need to import the Ansible variables for the roles we will be using. To do so, go to the Configure menu, and select Variables under the Ansible header. Click on the blue button that says Import from <Satellite hostname>.
A list of available Ansible variables available to be imported will be displayed. If you are planning on using all of the RHEL System Roles, you can import all of their associated variables, or only import the variables for the roles you will be using. In either case, click the blue Update button once you have selected the variables.

Initial Ansible Setup in Satellite
In order for the Ansible RHEL System Roles to be able to run, remote execution has to be setup and working in Satellite. For the steps to validate remote execution is working, see the Setting Up Remote Execution section of my previous blog on Getting started with Ansible in Satellite, and also review the documentation.
Next, we’ll create a host group by going to the Configure menu and selecting Host Groups, then clicking the Create Host Group button. I’ll name the Host Group standard-config, as shown:

Then we’ll click on the Ansible Roles tab. In this example, I’ll be configuring systems using the SELinux system role, so I’ll click the plus sign on rhel-system-roles.selinux to move it to Assigned Ansible Roles, and then click the blue Submit button.

Now that the Host Group has been created, the next step is to assign hosts I want to manage with the SELinux system role to be members of this Host Group. To do so, go to the Hosts menu and select All Hosts. Place checkboxes in each of the hosts that should be added to the Host Group, then click Select Action, and select Change Group.

On the next screen, for the Host Group, we will select the previously created standard-config Host Group and click Submit:

Customizing the SELinux System Role Variables
Now that the Host Group is all configured, we are almost ready to run the SELinux System Role on our client hosts. However, we first need to configure the SELinux system role with the details on how we’d like SELinux to be setup on the hosts. This configuration is done via Ansible variables within Satellite.
To understand what configuration options are available for the RHEL System Roles, refer to the included documentation under /usr/share/doc/rhel-system-roles-1.0/.
For the SELinux System Role, there is a readme file at: /usr/share/doc/rhel-system-roles-1.0/selinux/README.md and an example playbook at: /usr/share/doc/rhel-system-roles-1.0/selinux/example-selinux-playbook.yml.
The README file explains what variables are available and examples of how to use them.
In our case, we’d like to have the following SELinux configuration on all our servers in the standard-config Host Group
SELinux State: Enforcing
SELInux Boolean: use_nfs_home_dirs to be on
SELInux Boolean: ssh_sysadm_login to be on
SELinux Ports: ssh_port_t with port 50000
To implement this configuration, we’ll go to the Configure menu and Select Variables under the Ansible header. In order to only see variables related to the SELinux system role, we’ll filter for ansible_role = rhel-system-roles.selinux.
We’ll start by overriding the selinux_state variable by clicking on it in the list. We’ll then click the Override check box, uncheck the Hidden Value check box, and set the Default Value to enforcing, as shown:

We’ll then click Submit. You’ll notice a small blue flag next to the selinux_state variable now, which indicates the variable has been overridden.
We’ll repeat the same process to override the selinux_booleans variable, however, this time the Parameter Type is an array, so the value needs to be formatted as an array. We’ll set it to the value shown below to persistently set the two SELinux booleans previously mentioned.
[ { name: 'use_nfs_home_dirs', 'state': 'on', persistent: 'yes' }, { name: 'ssh_sysadm_login', 'state': 'on', persistent: 'yes' } ]

The final variable we’ll override is selinux_ports, which is another array variable. We'll set it to the value shown below.
[ { ports: '50000', proto: 'tcp', setype: 'ssh_port_t', state: 'present' } ]

In these examples, we’ve done basic overrides of the variables. However, it is possible to do more advanced configurations with Matchers. For more information on these advanced use cases, see my earlier blog post on Advanced Ansible variables in Satellite.
Running the SELinux role
At this point, we have everything configured and are ready to run the SELinux system role on the clients that have been added to the standard-config Host Group. In my example, I have two RHEL 7 clients, and one RHEL 6 client in this Host Group.
Before running the role, I checked the status of SELinux on one of the clients:
# getenforce Permissive # semanage boolean -l | egrep "use_nfs_home_dirs|ssh_sysadm_login" use_nfs_home_dirs (off , off) Allow use to nfs home dirs ssh_sysadm_login (off , off) Allow ssh to sysadm login # semanage port -l | grep ssh ssh_port_t tcp 22
To run the role, we’ll go to the Configure menu, and select Host Groups. Press the dropdown menu to the right of the standard-config Host Group, and click Play Roles.

At this point, Satellite runs the SELinux system role on the clients, and the status is shown. If there are any failures, click on the host names that failed at the bottom of the screen to see the Ansible output. The SELinux system role will report a failure if the changes to the system require a reboot (for example, changing the SELinux state from disabled to enforcing). In my case, all were successful:

I’ll re-check one of the clients to make sure the SELinux changes were implemented as expected:
# getenforce Enforcing # semanage boolean -l | egrep "use_nfs_home_dirs|ssh_sysadm_login" use_nfs_home_dirs (on , on) Allow use to nfs home dirs ssh_sysadm_login (on , on) Allow ssh to sysadm login # semanage port -l | grep ssh ssh_port_t tcp 50000, 22
Next Steps
At this point, we have implemented the desired SELinux settings on the Satellite clients using the SELinux system role. It is recommended that Satellite be configured to re-run the Ansible role at regular intervals to validate that the settings are still correct, and if not, to set them to the desired state.
For more information on how to do this, refer to the Scheduling Automatic Runs of Ansible Roles section in my previous post on Getting started with Ansible in Satellite.
Summary and Closing
In conclusion, RHEL System Roles Powered by Ansible are a great way to manage and automate many common configuration settings in your RHEL environment. By utilizing the power of Satellite’s Ansible integration, we can easily implement and customize RHEL System Roles right from the Satellite web interface, as I have shown in this post.
Sull'autore
Brian Smith is a product manager at Red Hat focused on RHEL automation and management. He has been at Red Hat since 2018, previously working with public sector customers as a technical account manager (TAM).
Altri risultati simili a questo
Behind the scenes of RHEL 10, part 3
Alliander modernises its electricity grid with Red Hat for long-term reliability in balance with rapid innovation
The Overlooked Operating System | Compiler: Stack/Unstuck
Linux, Shadowman, And Open Source Spirit | Compiler
Ricerca per canale
Automazione
Novità sull'automazione IT di tecnologie, team e ambienti
Intelligenza artificiale
Aggiornamenti sulle piattaforme che consentono alle aziende di eseguire carichi di lavoro IA ovunque
Hybrid cloud open source
Scopri come affrontare il futuro in modo più agile grazie al cloud ibrido
Sicurezza
Le ultime novità sulle nostre soluzioni per ridurre i rischi nelle tecnologie e negli ambienti
Edge computing
Aggiornamenti sulle piattaforme che semplificano l'operatività edge
Infrastruttura
Le ultime novità sulla piattaforma Linux aziendale leader a livello mondiale
Applicazioni
Approfondimenti sulle nostre soluzioni alle sfide applicative più difficili
Virtualizzazione
Il futuro della virtualizzazione negli ambienti aziendali per i carichi di lavoro on premise o nel cloud
