This is the first in a series of three blog posts focusing on United Kingdom Critical National Infrastructure (CNI) cybersecurity. Part 1 will focus on giving readers an overview of the problem space that CNI organizations face, Part 2 will explore the critical areas of People and Processes, and finally, Part 3 will concentrate on technology and identify where CNI organizations can reduce their risk through Red Hat technology, training, and services.
- Enterprise security challenges for CNI organizations: Overview
- Enterprise security challenges for CNI organizations: People and processes
- Enterprise security challenges for CNI organizations: Technical solutions
All organizations across the globe are feeling the effects of increased cybersecurity attacks. Along with the growing number of attacks, the complexity of the tactics and techniques used by intruders has expanded significantly, which makes detection and prevention markedly harder.
This blog uses the UK National Protective Security Authority's (NPSA) definition of Critical National Infrastructure, which is:
“National Infrastructure are those facilities, systems, sites, information, people, networks and processes, necessary for a country to function and upon which daily life depends. It also includes some functions, sites and organisations which are not critical to the maintenance of essential services, but which need protection due to the potential danger to the public (civil nuclear and chemical sites for example).”
In the UK, there are 13 national infrastructure sectors:
The damage to critical infrastructure—its destruction or disruption by natural disasters, terrorism, criminal activity, or malicious behavior—may have a significant negative impact on a nation's security, safety, and economy.
As a global organization, Red Hat has many customers who fall under the banner of CNI. We proactively work with our customers to help identify risks and provide mitigation advice, putting an emphasis on IT security best practices and postures at a foundational level for all our solutions.
Case Study 1: NCSC warns of emerging threat to critical national infrastructure
In 2022, Check Point Research reported a 77% increase in UK cyberattacks, including very real and recent attacks on CNI organizations. For example, in April 2023, the UK National Cyber Security Centre issued an alert concerning CNI.
- The threat comes particularly from state-aligned groups sympathetic to Russia's invasion of Ukraine and has emerged over the past 18 months.
- These groups are not motivated by financial gain nor subject to control by the state, so their actions can be less predictable and their targeting broader than traditional cybercrime actors.
- Activity from the groups is likely to take the form of Distributed Denial of Service (DDoS) attacks, website defacements, or the spread of misinformation.
Case Study 2: Tech flaw that lets intruders control surveillance cameras
A recent BBC story details foreign-made surveillance cameras in British offices, high streets, and even government buildings. CNI was specifically called out:
Prof Fraser Sampson, the UK's surveillance camera commissioner, warns the country's critical infrastructure - including power supplies, transport networks and access to fresh food and water - is vulnerable. "All those things rely very heavily on remote surveillance - so if you have an ability to interfere with that, you can create mayhem, cheaply and remotely," he says.
Security tooling can help CNI organizations better secure their IT environments, but not all CNI cybersecurity challenges can be resolved or mitigated through purely technical methods. We also need to focus on people and processes issues when addressing cybersecurity concerns.
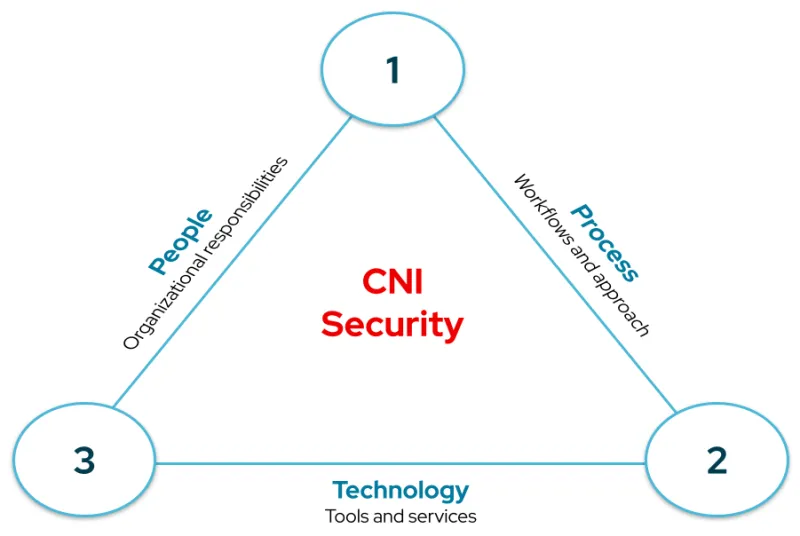
CNI security challenges
This section identifies some security challenges that can affect CNI organizations. Due to cybersecurity's constantly shifting risk profile, this isn't a definitive list but offers some initial focus areas.
Cyber threats
Threat actors are constantly developing new tactics and techniques to breach security defenses; therefore, CNI organizations need to constantly reassess their security processes. Security is an ongoing and cyclic process, with new cyber attack threats being revealed practically every day. Having agile and extensible security policies can help organizations keep one step ahead of cybercriminals. To develop and manage these policies, you need to understand which areas of your organization have the potential for compromise and what data is stored, transferred, or processed.
CNI organizations, especially, must build methodical threat analysis across critical systems and infrastructure that is updated with the ever-changing and continuous threat risk. Effective threat modeling should be a key part of the CNI security operations, guided by NCSC frameworks.
Critical infrastructure security spending to grow 83% by 2027.
Large attack surface
The UK's CNI is a natural target for a major cyber attack due to its importance to daily life, law, order, and the running of the country's economy. It is strongly recommended that organizations proactively conduct attack surface analysis as an essential first step to reducing attack surfaces. This activity will help define a strategy to identify and prioritize specific functions and processes, giving you the ability to start planning either mitigation or risk management acceptance.
A significant number of CNI organizations rely on IT systems that are between 6-20 years old. These critical systems may be running unpatched or “End of Life” operating systems and software with known (and published) vulnerabilities at varying levels of severity. It is recommended to keep software updated, especially where vulnerabilities have been identified with a severity level of Critical or Important.
"It has become clear that certain state-aligned groups have the intent to cause damage to CNI organisations, and it is important that the sector is aware of this.” - Dr Marsha Quallo-Wright, NCSC Deputy Director for Critical National Infrastructure
State-sponsored actors
Due to the large attack surface, CNI cybercriminals are no longer just "Script Kiddies" but can be state-sponsored actors with access to funds, extensive IT skills, and massive computing power. A report from Microsoft observed the cyber-threat landscape between July 2021 and June 2022, and it found that the proportion of cyber-attacks perpetrated by nation-states targeting critical infrastructure jumped from 20% to 40%.
NCSC has also issued warnings about state-sponsored cyber activity targeting CNI networks. These types of threat actors have highly malicious intent and focus on actively damaging CNI systems to create potential safety and/or security issues.
Software supply chain management
Software supply chains are not formally regarded as part of the UK's CNI, but they are integral to their operation. Attackers increasingly exploit supply chain vulnerabilities to access CNI operators' networks and systems. Cyber attacks against software supply chains are often more successful than attacks against large entities due to the many "moving parts" within the supply chain. By implementing a Trusted Software Supply Chain, organizations can attest to the source of the software and build security checks into the development process. Once a specific software component has been created and assessed to meet the security requirements, it is possible to digitally sign the component and create a Software Bill of Materials (SBOM), demonstrating its provenance.
Third-party risks
CNI organizations often rely on third-party vendors for various services and products. However, these third parties may not have adequate IT security measures in place, creating vulnerabilities in the organization's overall security posture. Using the techniques mentioned above regarding software supply chain management, all third-party software should be signed using a certificate issued by a trusted Certificate Authority. Once deployed, the software should also be patched as and when the provider distributes updates in a security-forward manner. You can find an example of a third-party cyber attack in the NCSC Supply chain security guidance.
Complex and legacy systems
Additional complexity can be introduced as IT systems grow, which needs to be identified and managed from a security point of view. Some of this growth can be organic through integration with legacy systems, acquisitions, or utilizing a hybrid cloud architecture. Threat modeling techniques can be employed to holistically identify and manage security weaknesses and vulnerabilities. It is important to stress that threat modeling is a process, not a tool. While tools can help the process be more efficient (e.g., by providing visualization, platform baselining and drift, tracking changes over time, or identifying changes to software that would more likely affect its threat model), tools by themselves cannot currently take the place of humans reasoning about how other humans would attack a system.
A significant number of CNI organisations rely on IT systems that are between 6-20 years old.
Intensive manual processes
Heterogeneous systems can make configuration management difficult because different systems use various tools for provisioning, configuration, maintenance, and support. This problem is conflated when multiple operations teams using different tools and techniques carry out these processes. These repetitive and time-consuming tasks are prone to human error and can have severe implications on critical systems. A comprehensive automation strategy consisting of automation and Infrastructure as Code (IaC) can help alleviate these issues. Replacing manual tasks with automated processes can also improve infrastructure consistency and help eliminate configuration drift.
With human error accounting for 95% of security breaches and costs associated with cybercrime predicted to reach US$8 trillion globally in 2023 according to Cybersecurity Ventures, manual detection and responses aren’t enough.
Lack of observability
The full ecosystem of CNI organizations' IT systems can be vast—not just geographically (as most are national systems) but also due to the use of multiple heterogeneous environments. With such a large estate to manage, you need full observability of all systems to establish and maintain the cybersecurity posture. The phrase "If you cannot see it, you cannot secure it" is very relevant in this scenario. Once you have full observability, you can enable monitoring, event logging, and alerting for a comprehensive view of your environment. With these practices in place, you can automatically assess your cybersecurity hygiene using baselining and regular assessments. Creating clearly defined system and platform baselines, including regular patching regimes, will allow you to identify drift from the baseline, which could indicate malicious activity. Baselining your platforms also helps with regulatory compliance. You should have a trusted, documented, and standardized deployment process to meet individual security requirements.
Multiple security frameworks
Many security frameworks exist, such as the ISO 27000 Series, NIST Special Publications, and the Center for Internet Security (CIS) Critical Security Controls. Each of these frameworks assists with defining policies and procedures around the implementing and managing security controls. The goals of each framework are similar, but identifying areas specific to CNI organizations can be overwhelming.
The NCSC Cyber Assessment Framework (CAF) is a valuable resource for organizations that form part of UK CNI to assess their cyber security strategy and identify areas for improvement.
Wrap up
Hopefully, you have found this post useful and have considered some of the topics to help reduce risk and better secure your CNI systems. There is no magic bullet when it comes to cybersecurity, but by understanding some of the challenges above and shifting security left within your organization, you can start putting the security guardrails, monitoring, and processes in place to secure your overall infrastructure better.
Just remember that good security is based on good engineering practices.
About the author
Chris is a visionary Senior Principal Chief Architect renowned for spearheading innovative cybersecurity strategies and fostering the seamless adoption of cutting-edge security measures. With over 30 years of distinguished experience in the technology industry, Chris is a trailblazer known for crafting robust security frameworks that fortify organisations against evolving cyber threats while ensuring business continuity and growth.
More like this
Chasing the holy grail: Why Red Hat’s Hummingbird project aims for "near zero" CVEs
Elevate your vulnerabiFrom challenge to champion: Elevate your vulnerability management strategy lity management strategy with Red Hat
Data Security And AI | Compiler
Data Security 101 | Compiler
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Virtualization
The future of enterprise virtualization for your workloads on-premise or across clouds
