Many customers I talk to have gotten a lot of value out of Red Hat Insights, which allows Red Hat Enterprise Linux (RHEL) customers to proactively identify and remediate risks in their RHEL environments. These risks can include items related to security and compliance, performance, availability, and stability.
However, one common request I’ve heard is that customers would like a way to add their own internal checks that are specific to their environment into Insights.
This type of functionality is now available with the Policies capability in Red Hat Insights, which allows customers to define their own policies which are evaluated when Insights data is uploaded from RHEL hosts. If any of the policies are evaluated to match, an email or webhook action can be triggered.
Some examples of what Policies can check for, and notify you about, include:
-
Running processes (for example, notify if firewalld isn’t running, or notify if a third party antivirus process isn’t running)
-
The number of CPUs or sockets (for example, notify if there are less than two CPUs on a host)
-
Amount of memory on the host (for example, notify if hosts don’t have a specific amount of memory)
-
The packages installed on a host (for example, notify if a specific package is or isn’t installed, or notify if a package is not at a specific version)
-
The RHEL OS release (for example, notify if servers are on a version less than RHEL 8.2)
For a list of available facts that Policies can use, see this documentation.
There are also a wide variety of operators that can be used, including logical AND and OR operators that allow powerful Policy checks to be developed. For example, you could write a policy that will check that firewalld is both currently running and also enabled to start at boot.
Example Environment and Policy Goals
In my test environment, I have four systems configured in the following manner:
|
Server Name |
CPU’s |
OS |
firewalld running |
|
prod-db |
2 |
RHEL 8.2 |
Yes |
|
prod-web |
2 |
RHEL 8.2 |
Yes |
|
test-db |
1 |
RHEL 8.2 |
Yes |
|
test-web |
2 |
RHEL 8.1 |
No |
I would like to use Insights Policies to validate the following conditions are true, and get an email notification if they are not:
-
Hosts should have two CPUs
-
Hosts should be running RHEL 8.2 or later
-
firewalld should be running and enabled to start at boot on hosts.
Throughout this post, we will walk through setting up these policies and see examples of the resulting alerts when systems are out of alignment with these policies.
Registering Insights clients
The first step to using any of the Insights services, including Policies, is to register your RHEL servers with Insights. There are two ways to do this. See the Red Hat Insights Get Started documentation for information on how to register RHEL servers. And there is now an intuitive and interactive capability to register systems right on the Insights dashboard, under the left menu item called Register Systems.
If you have a large number of hosts to register, there are options to automate the Insights client registration process, and the previous two links contain more information on this.
Accessing Red Hat Policies
Now that the hosts are registered with Insights, we’ll next go to the Insights Inventory page, which will show a list of the systems that have been registered with Insights, as shown in figure 1.

Figure 1. Insights Inventory page
We also need to enable Insights Polices email alerts by accessing the Email preferences page (see figure 2). This is done by clicking on the name in the upper right section of the screen, and clicking on User Preferences. From this page, you can either enable Instant notifications to receive an immediate email after Polices are triggered, or you can select the Daily digest option to receive a daily summary of triggered policies, or you can select both options. In our case, the inventory contains 4 systems, so we can opt-in for instant notification, which will send one email for each system matching a policy. For large inventories, daily digest is a preferred option to avoid receiving too many emails.

Figure 2. Email preferences page
We can then browse to the Policies page. A list of any policies that have been created on your account will be shown.
To create a policy, click the Create Policy button. If you already have policies defined in your account, you’ll be prompted to pick if you would like to define the new policy from scratch, or define the new policy as a copy of an existing policy. Next, you’ll be prompted for the name of the policy and an optional description (see figure 3). We’ll start by creating a policy that will alert if hosts don’t have two CPUs.

Figure 3. Policy details section of creating a Policy
The next screen will prompt for the conditions for the policy. If these conditions evaluate to “true” then a trigger action (email notification or webhook) will be triggered. For a list of available facts that Policies can use, see this documentation, and see this documentation on the operators that can be used.
We would like to trigger the policy if hosts don’t have two CPUs so the condition text will be:
NOT facts.number_of_cpus = 2
Next, we will click on the Validate condition button and ensure its syntax represents a valid condition, as shown in figure 4.
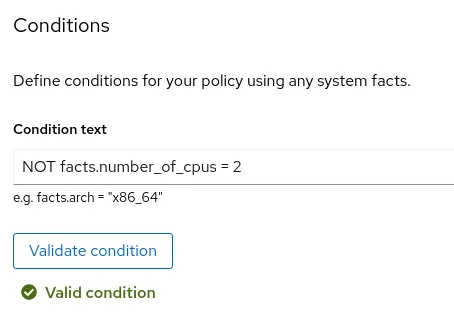
Figure 4. Validating the syntax
On the next screen, we can click on Add trigger actions, and select Email, as shown in figure 5.
Figure 5. Adding an email trigger action
On the final screen, we can either select if the policy should be disabled or enabled, confirm the policy settings, then click Finish, as shown in figure 6.

Figure 6. Reviewing the policy and specifying if it should be enabled
We’ll also create the other two policies to notify if servers are at less than RHEL 8.2, or if they don’t have firewalld running and enabled to start at boot.
For the policy to notify if servers are at less than RHEL 8.2, the condition text would be:
facts.os_release < 8.2
For the final policy to notify if firewalld is not running and enabled at boot, the condition text would be:
NOT ( facts.running_processes contains ['firewalld'] AND facts.enabled_services contains ['firewalld'] )
You might be wondering why the “NOT” statement is used and its parentheses surround the rest of the condition. If the condition were missing the “NOT” statement, as shown below, the condition would only be triggered when the firewalld process is running and the firewalld service was enabled.
facts.running_processes contains ['firewalld'] AND facts.enabled_services contains ['firewalld']
We want to be notified if it is not running/enabled, so we wrap the entire statement in a “NOT”.
Testing the Policies
The policy will be checked the next time the hosts upload Insights data via the Insights client, so we can wait until the next scheduled run, or we can manually run the insights-client command on the hosts to force an upload of the Insights data.
Once the Insights data is uploaded, if you’ve enabled instant email notifications for Insights Policies, you’ll receive an email for each host that matches one or more of the policies. If you’ve opted for the daily digest email notification, you’ll receive a daily summary of which policies matched.
The instant email notifications I received in this example for test-db.example.com indicate this host matched the policy rule regarding the number of CPUs (see figure 7), which was configured to notify on any hosts that didn’t have two CPUs.

Figure 7. Policy email regarding the test-db.example.com host
I received another email for the test-web.example.com host indicating that the policy matched for systems not running RHEL 8.2 or later, as well as that the policy matched for servers that don’t have firewalld running and enabled to start at boot, as shown in figure 8.

Figure 8. Policy email regarding the test-web.example.com host
Summary and Closing
Red Hat Insights Policies is a useful tool that enables you to essentially create custom Insights rules specific to your environment. If any of these custom Policy rules match, you can be notified via an email or webhook. We covered a few examples of policies that can be created, but we really just scratched the surface of what's possible. The policies you implement in your environment can be driven by what’s most important to you and your organization.
You can see a short presentation and live demo of the Policies capability from a recently recorded “Ask Me Anything” webinar. This webinar is part of a full series of technical webinars on the new Red Hat Insights capabilities to help you get started.
About the author
Brian Smith is a product manager at Red Hat focused on RHEL automation and management. He has been at Red Hat since 2018, previously working with public sector customers as a technical account manager (TAM).
More like this
Refactoring isn’t just technical—it’s an economic hedge
Migrate your VMs faster with the migration toolkit for virtualization 2.11
Understanding AI Security Frameworks | Compiler
Data Security And AI | Compiler
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Virtualization
The future of enterprise virtualization for your workloads on-premise or across clouds
