What can be said about 2020 that hasn’t been said already? It definitely was a year where things happened and there certainly were several of those things that involved security. Looking across the vulnerability landscape, we see that more than 176,447 CVEs were reported.
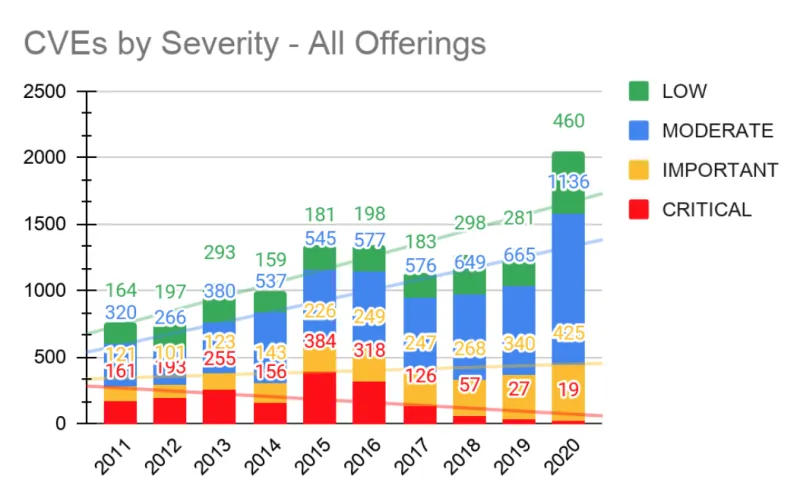
Within the Red Hat portfolio, we identified 2,040 unique CVEs that impacted components we supply and support. This was far-and-away the highest volume of CVEs we’ve fixed in any calendar year on record. This translates to a significant amount of work an operator or administrator needs to do in order to keep their systems running at peak patch levels.
We understand that most enterprises do not run exclusively on Red Hat products and services, and for someone that is responsible for a heterogeneous environment that has a melange of technologies to keep updated, it can seem like a Herculean task.
This is why we issue Red Hat Severity Scores with each vulnerability, along with our CVSS scoring and CWE analysis. Every security issue has some level of importance to deal with, but some issues have higher likelihoods of being exploited or have higher consequences if they were.
It is interesting to note that over the years we’ve actively tracked and reported on issues impacting our software to see the change in distribution of the severity of issues. The volume of Critical and Important issues that we consistently address across the whole portfolio have remained generally flat, with a slight uptick in 2020, but are nowhere near “record levels.” Red Hat Engineering addressed Critical issues across the portfolio with great speed. In 2020, 31% of CVEs that we rated as Critical were addressed and had patches for consumers within one business day. A total of 89% had fixes within one week and a full 100% were addressed within one month of public disclosure.
Overall, the volume of issues we patched was 1.5 times higher than we had in 2019, with the average and median delivery times being down. This translates to faster availability of security updates.
The volume of Moderate security flaws that were fixed in 2020 alone was more than all the vulnerabilities Red Hat fixed back in 2011, 2012, 2013, and 2014 (plus we fixed 460 Low severity issues as icing on that cake). This was a 3x increase in volume across the board since 2011...what do the next nine years hold? Only time will tell.
Reducing security risks requires effective management programs
As systems get more complex, the key to reducing your risks associated with them is to have effective patch and vulnerability management programs in effect and to minimize the attack surface if you present a malicious or curious actor.
It is worth noting that when default security features are disabled (like turning SELinux off for example, which if you did would make Dan Walsh cry), the risk profile of that system is drastically altered, opening up the potential for additional security risks and impacts. Good security hygiene, timely patch management, and appropriate access controls and logging can go a very long way preventing the next terrible media headline from impacting you.
We hope you’ve enjoyed this series of blogs around our 2020 Product Security Risk Report. Each of these articles has expanded upon a concept covered within the report, so if you liked the blogs, please read the full report to learn more.
執筆者紹介
Christopher Robinson, better known as CRob to his colleagues, is a former Product Security Program Architect at Red Hat.
チャンネル別に見る
自動化
テクノロジー、チームおよび環境に関する IT 自動化の最新情報
AI (人工知能)
お客様が AI ワークロードをどこでも自由に実行することを可能にするプラットフォームについてのアップデート
オープン・ハイブリッドクラウド
ハイブリッドクラウドで柔軟に未来を築く方法をご確認ください。
セキュリティ
環境やテクノロジー全体に及ぶリスクを軽減する方法に関する最新情報
エッジコンピューティング
エッジでの運用を単純化するプラットフォームのアップデート
インフラストラクチャ
世界有数のエンタープライズ向け Linux プラットフォームの最新情報
アプリケーション
アプリケーションの最も困難な課題に対する Red Hat ソリューションの詳細
仮想化
オンプレミスまたは複数クラウドでのワークロードに対応するエンタープライズ仮想化の将来についてご覧ください
