Containers may be like "sandboxes," but libraries and applications still run inside of them, and like everything else, those components need to be monitored for vulnerabilities. The Red Hat Advanced Cluster Security (RHACS) module monitors runtime data on containers to look for known vulnerabilities and to verify Kubernetes clusters for policy enforcement. RHACS can gather information about the container platform and the images, applications, and configuration assets that control the behavior of applications once deployed.
When I'm doing product testing, I deploy RHACS on OpenShift. It's uncovered some major vulnerabilities before deployment, and preventing them from getting into production is what matters.
Install RHACS
The first step is to install the Advanced Cluster Security (ACS) Operator. To start, log into your OpenShift Container Platform (OCP) web console, search for ACS in OperatorHub, and install it. By default, ACS is installed in the rhacs-operator namespace.

ACS uses two custom resources, which you need to install after installing the ACS Operator:
- Central installs the Central, Scanner, and Scanner DB services. The Central service provides access to a user interface through a web UI or the RHACS portal. It also handles API interactions and provides persistent storage. Scanner analyzes images for known vulnerabilities. It uses Scanner DB as a cache for vulnerability definitions.
- Secured Cluster installs the Collector, Sensor, and Admission Controller services. Collector collects runtime information on container security and network activity. It then sends data to Sensor, which monitors your Kubernetes cluster for policy detection and enforcement. Admission Controller monitors workloads and prevents users from creating them in RHACS when they violate security policies.

[ Shorten your OpenShift learning curve by downloading and reading OpenShift for Developers. ]
Install Central
First, select the rhacs-operator namespace, and then click on Create project. Create a new namespace, such as stackrox.
In the stackrox project, click on Central under Provided APIs.

Enter a name for your Central custom resource, and then click Create.
After installing Central, the RHACS portal or the Web user interface (UI) is ready for you to log in.
Navigate to Networking > Routes to get the new portal's URL.

Get the password of Central (or RHACS portal) by clicking on Workloads > Secrets > central-htpasswd. Copy the password.

Now log into the RHACS portal using the ID admin with the password you copied.
Generate an init bundle
Before you can create a Secured Cluster, you need to generate an init bundle. The Secured Cluster uses this bundle to authenticate with Central. You can do this from the RHACS portal or through Central.
In RHACS portal, navigate to Platform Configuration > Integrations. Under the Authentication Tokens section, click on cluster init bundle.
Click Generate bundle, and then click Download Kubernetes secrets file to download the generated bundle and save the YAML file.

In the OpenShift UI, click on the + (plus sign) in the top-right of the stackrox project and import the YAML file you downloaded.
This creates the required resources for Scanner to authenticate with Central in the RHACS portal.
Install a Secured Cluster
Almost done! All that's left is to install the Secured Cluster. Under the Provided APIs section, select Create instance on the Secured Cluster API.

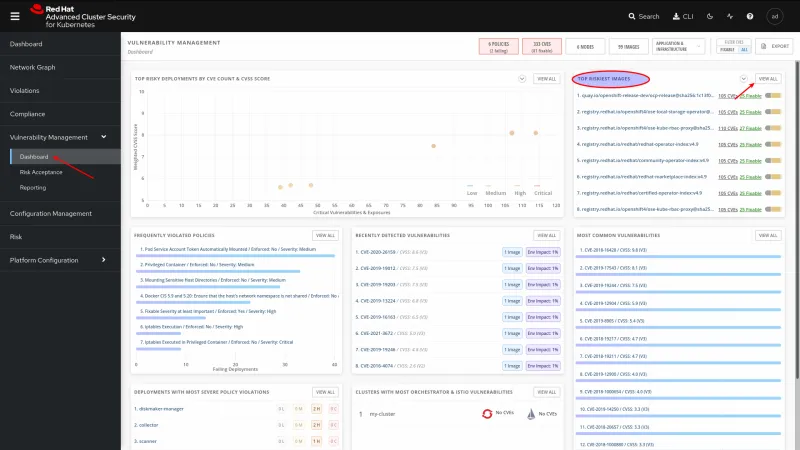
Once the scanner is up, go to the RHACS portal and click on the dashboard. The dashboard now shows data for clusters, nodes, and violations. It also shows the number of critical, high, and medium violations by cluster. You can click on each number to see details.
[ Learn how to bring security into your DevOps practice. Download A guide to implementing DevSecOps. ]
RHACS for Kubernetes automatically scans all deployments in the cluster for security risks and policy violations. For any new deployment, scanning starts as soon as the deployment is submitted to the cluster.

You can view all images scanned for vulnerabilities and their details at Vulnerability Management > Dashboard > View All (Top Riskiest Images).
Stay informed
Monitoring your systems is a vital part of maintenance, so stay informed about what you're about to deploy, and catch any problems before they go live.
About the author
Shveta is a senior software engineer at Red Hat, leading a team. She is a subject-matter expert on the Migration Toolkit for Applications (MTA) and Pathfinder that helps customers migrate their applications to containers (Openshift and Kubernetes) and the latest technologies. She continuously develops her technical and domain expertise in MTA, functional testing, Kubernetes, OpenShift, and DevOps and is involved in reporting and validating dozens of issues ensuring high-quality releases to customers. Shveta has independently built the automation framework from scratch for some Red Hat products and has automated the needed test cases in Python and Cypress. Shveta is also contributing to some DevOps tasks and CI/CD tools like building and maintaining Jenkins pipelines to run automation tests on virtual machines for different operating systems, including Linux, Windows, and macOS.
More like this
AI insights with actionable automation accelerate the journey to autonomous networks
IT automation with agentic AI: Introducing the MCP server for Red Hat Ansible Automation Platform
Data Security And AI | Compiler
Data Security 101 | Compiler
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Virtualization
The future of enterprise virtualization for your workloads on-premise or across clouds
