OpenShift is an enterprise application platform based on the Kubernetes orchestration tool. It can deploy applications from a number of sources, including prebuilt images as well as from source. In this article, I will talk about Source-to-Image (S2I) and how to automate the entire process using Git webhooks. You can follow along and try it out yourself for free at the OpenShift Interactive Learning Portal.
Source-to-Image
S2I is a process that takes source code for an application stored in a source control management tool like Git or SCM and puts it on a base image using BuildConfig, then deploys the application using DeploymentConfig. Below is a simple diagram that helps us to understand the entire process. In this process, if the code is updated on Git by a developer, we have to trigger a build manually by using this command:
oc start-build <build name>
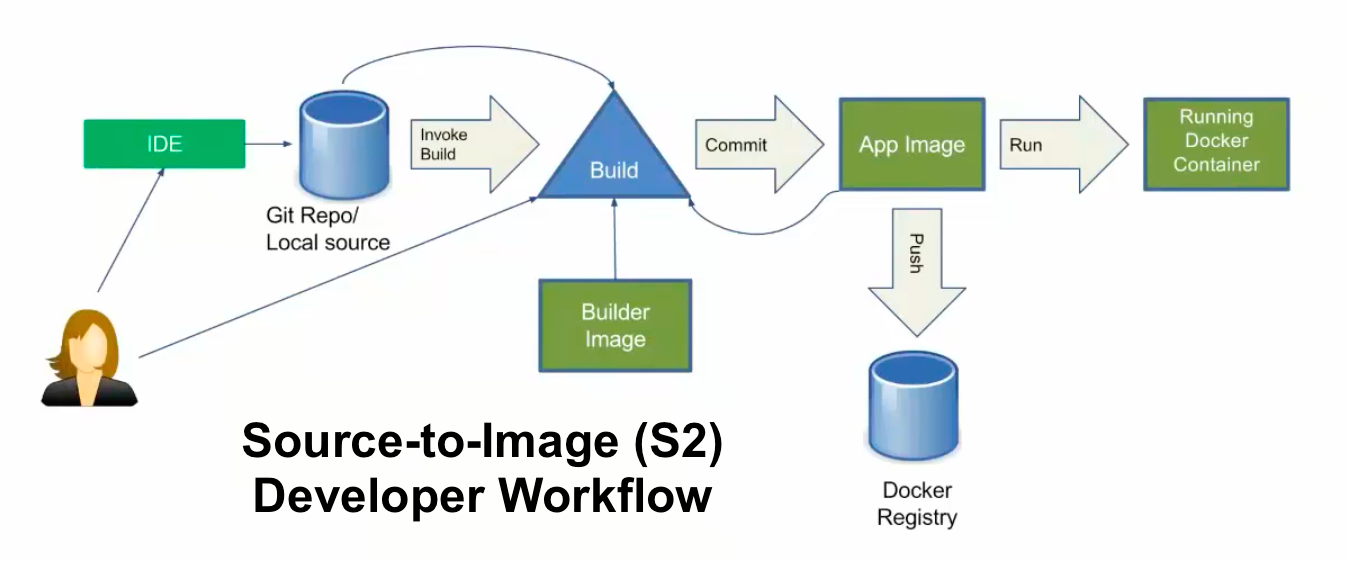
However, OpenShift provides a great way to deal with the automatic triggering of the BuildConfig by using webhooks. Let's see a quick demo of it. To do so, I am using learn.openshift.com running on OpenShift 4.2 CRC.
[ You might also enjoy reading: Troubleshooting handshake errors in OpenShift ]
To launch the application using the S2I process, which creates ImageStream, BuildConfig, DeploymentConfig, and the service in one go, you can do something like this:
$ oc new-app --name=demo https://github.com/ashutoshbhakare/php
$ oc expose svc demo # to create the route
Now let's try to integrate OpenShift and GitHub by using webhooks. To achieve this, we need a webhooks URL and a secret, which authenticates our GitHub trigger to OpenShift. So whenever a developer updates the GitHub source code, it immediately triggers the build to OpenShift. Webhooks is an API call that is running on port 6443. To get the webhooks URL and secret, we can use:
$ oc describe bc demo
Which returns the output below:

In the above example, https://openshift:6443 must be replaced with our OpenShift's master URL, per my learn.openshift.com online labs.
To get the secret:
$ oc get bc demo -o yaml | grep secret
secret: N58sBgReryjBwYIBp4FV
secret: u1BaRZVDxAfvsT5lC3tX
We are going to use the second value, which is for generic webhooks: payload URL for GitHub.
Add the webhook
This was the most tricky part of the online labs.
Now let's go to GitHub and add the webhook payload URL to it. By clicking settings and the Selecting Webhooks option → Add Webhook, we will copy the entire payload URL like above and paste the secret in the text box.

This is how the GitHub and OpenShift webhooks integration successfully completed. We can test that by changing the Git code, which should result in the info below, which shows the recent deliveries.

[ Learn the basics of using Kubernetes in this free cheat sheet. ]
Wrap up
Source-to-Image (S2I) can help to automate the process of launching an application by using Git webhooks. The process can be straightforward, and you can demonstrate it yourself at the OpenShift Interactive Learning Portal.
About the author
Ashutosh is an open source software advocate, docker community leader, Fedora active contributor, Red Hat / SUSE Certified Instructor with 19 years of experience as a trainer and consultant.
More like this
Simplify Red Hat Enterprise Linux provisioning in image builder with new Red Hat Lightspeed security and management integrations
F5 BIG-IP Virtual Edition is now validated for Red Hat OpenShift Virtualization
Scaling For Complexity With Container Adoption | Code Comments
Kubernetes and the quest for a control plane | Technically Speaking
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Virtualization
The future of enterprise virtualization for your workloads on-premise or across clouds
