While migrating virtual or containerized workloads between environments may seem straightforward, teams responsible for managing system uptime, policy enforcement, and securing east-west traffic, often find it to be a complex process. Subtle differences in hypervisor behavior, inconsistent policy application, and blind spots in traffic flows can introduce risks that aren’t always obvious, until it’s almost too late.
Red Hat OpenShift Virtualization combined with Palo Alto Networks VM-Series software firewalls helps address these complexities where they typically arise.
OpenShift Virtualization streamlines the modernization and lifecycle management of VM-based workloads within a Kubernetes-native platform. VM-Series complements this by bringing consistent, application-aware network security to virtualized environments, helping teams enforce policy and maintain visibility even as infrastructure evolves.
Additionally, Red Hat OpenShift integrated with Prisma AIRS™ enables customers to deploy AI-powered threat prevention for runtime network protection across containerized workloads running on OpenShift clusters.
The operational tension
Many enterprises operate in hybrid environments by necessity, not choice. Existing virtualization investments coexist with containerized applications, and teams are expected to support both with equal reliability. The operational challenge is not only bridging these domains but doing so without fragmenting security policy, tooling, or visibility.
Today, workloads migrate between private clouds, public clouds, or across datacenters and have different form factors of the workload including physical, virtual, and containerized. While this provides significant flexibility to the customers, it compounds the issue of enforcing uniform security posture, and migrations become moments of risk. Policy gaps, inconsistent segmentation, or east-west blind spots can create undetected lateral movement paths for threats.
A strategic optimization
OpenShift Virtualization allows VMs to run fully supported and integrated on a Kubernetes platform, using the open source KubeVirt project. This lets organizations consolidate VM and container workloads within OpenShift clusters, maintaining consistent deployment, scaling, and lifecycle controls. VMs are hosted on the KVM-based hypervisor and are managed using an intuitive web interface based on familiar Kubernetes APIs.
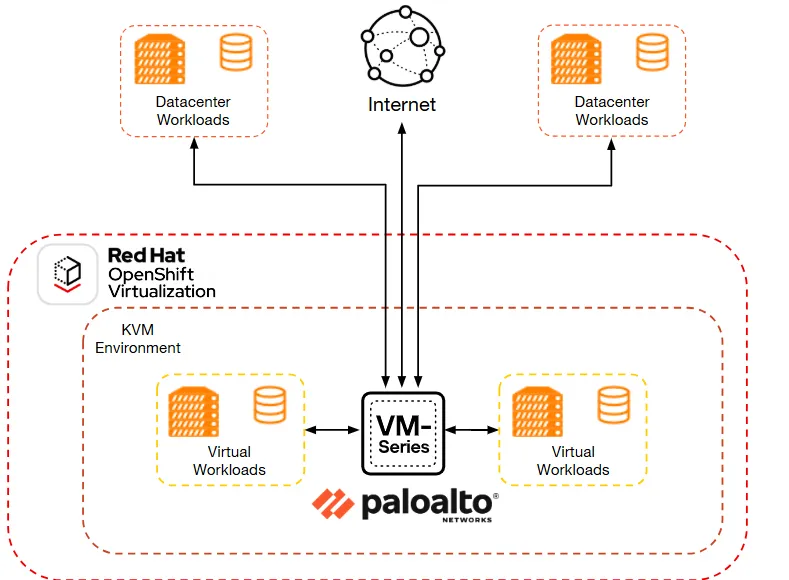
Palo Alto Networks VM-Series software firewalls extend Layer 7 threat prevention into this environment. These software firewalls enforce granular, application-level policies, perform real-time traffic inspection, and support dynamic updates via automation.
This architecture allows:
- Consistent east-west segmentation using VM-Series software firewalls to isolate traffic between VMs..
- Policy enforcement via Panorama or Strata Cloud Manager (SCM), delivering centralized, scalable management across clusters, with Red Hat Ansible Automation Platform modules enabling automated firewall provisioning and policy deployment as infrastructure shifts.
- Shared visibility across workloads, correlating OpenShift network telemetry with VM-Series traffic logs.
Red Hat OpenShift optimization with Prisma AIRS

With Prisma AIRS support for Red Hat OpenShift, customers can use Prisma AIRS to protect containerized and AI apps running on Red Hat OpenShift clusters and provide visibility and runtime security against unpatched and unknown threats, allowing them to enforce a more consistent security posture in every cloud and across hybrid cloud environments. Prisma AIRS can be managed with Panorama or Strata Cloud Manager (SCM), providing network security teams with a familiar interface and capabilities through a single-pane-of-glass console.
Red Hat OpenShift can be integrated with Prisma AIRS, providing the following customer benefits:
- Scale network security while executing digital transformation.
- Protect containerized and AI apps against known, unknown, foundational, and AI-specific threats.
- Harden the security of all applications easily with centralized management and consistent tooling.
Strategic implications
For senior technical leaders, the value of these integrations is fundamentally strategic and not merely tactical. The highlights of these values include:
- Infrastructure rationalization by collapsing VM and container management into a single platform.
- Threats are contained more effectively by applying consistent microsegmentation and inspection.
- Streamlined management and maintained security during cloud migrations or datacenter consolidations.
Security teams gain uniformity, while operations teams retain control and performance. The result is a shared control plane that reflects the hybrid nature of modern enterprise IT.
Use case: workload migration with embedded security
As organizations begin to transition away from legacy virtualization platforms to a more cloud-native architecture, migrating VMs to OpenShift Virtualization addresses a practical and strategic path toward modernization. These migrations often span multiple trust zones, requiring encrypted communications, inspection of inter-VM traffic, and revalidation of security policies.
Using OpenShift Virtualization with Prisma AIRS solves this by:
- Preserving security posture end-to-end during workload transitions.
- Securing traffic in transit with controlled ingress and egress policies enforced by VM-Series.
- Enabling license portability via Flex Credits, credits from retired firewalls that can be reassigned, simplifying provisioning at new destinations.
This lowers operational overhead and reduces the risks associated during migration windows, which are often points of elevated exposure.
Use case: centralized management and policy uniformity
One of the persistent challenges in hybrid infrastructures is enforcing a consistent security policy across disparate workload types. Containers may be managed via CI/CD pipelines, while VMs still rely on traditional deployment paths. This asymmetry often leads to fractured security postures, compounded by the fact that traditional security tools lack visibility into east-west traffic within container clusters, a critical gap as Gartner predicts over 75% of AI applications will run on containers by 2027.
OpenShift Virtualization helps address this challenge by standardizing the deployment model, bringing VMs into the same Kubernetes-native management framework used for container workloads. Rather than managing VMs separately through traditional hypervisor-specific tooling, teams can define, schedule, monitor, and scale VMs using the same APIs, declarative configurations, and automation pipelines that govern their containers.
To complete this unified approach, solutions like Prisma AIRS extend zero trust security and AI-powered threat prevention across both containerized and virtualized workloads on OpenShift. By providing runtime network protection with full visibility into intracluster traffic, Prisma AIRS enables consistent security enforcement and microsegmentation policies across all workload types, whether they're traditional containers, VMs managed through OpenShift Virtualization, or emerging AI applications. This combination means infrastructure teams no longer need to maintain parallel systems for either operations or security, achieving true consistency across their hybrid infrastructure while protecting against both known threats and zero-day attacks at the application layer.
Administrators can manage these controls via Palo Alto Networks Panorama or Strata Cloud Manager (SCM), while continuing to use OpenShift’s native tools for workload orchestration. Ansible Automation Platform can also bridge these management domains, enabling teams to automate firewall configurations and security policies within their existing CI/CD pipelines. This separation of duties helps maintain clarity while reducing tool sprawl.
Implementation notes
With this architecture, VM-Series firewalls are deployed as VMs inside OpenShift Virtualization running on KVM hypervisors. Each firewall instance can inspect traffic routed through OpenShift’s software defined network (SDN), with policies dynamically enforced based on labels, namespaces, or service identity.
This allows:
- Policy definitions that follow workloads, not IP addresses.
- Automated enforcement changes driven by GitOps workflows.
- Real-time traffic inspection, including TLS decryption, application identification (App-ID), and user ID-based access controls.
These capabilities are critical when supporting regulated workloads or environments where auditability and segmentation are non-negotiable.
Final thoughts
The hybrid infrastructure challenge isn't going away; if anything, the rapid adoption of containerized applications and AI workloads is making it more complex. Organizations need practical paths to modernize without abandoning existing investments in virtualization or compromising security.
OpenShift Virtualization provides the operational foundation by bringing VMs into the Kubernetes-native world, creating a unified platform where infrastructure teams can manage both traditional and cloud-native workloads through consistent APIs, declarative configurations, and automation pipelines. But as workloads evolve and multiply, standardization alone isn't sufficient.
This is where Palo Alto Networks' complementary security solutions complete the picture. VM-Series software firewalls deliver deep, application-aware inspection and Layer 7 policy enforcement for virtualized workloads, while Prisma AIRS extends AI-powered threat prevention and runtime protection to containerized applications, including the emerging wave of AI workloads. Both solutions can be integrated with OpenShift, providing a consistent security posture through centralized management via Panorama or Strata Cloud Manager (SCM).
The combination enables organizations to enforce uniform security policies across their entire hybrid estate, whether protecting legacy VMs during migration, securing modern microservices, or safeguarding AI applications. With Ansible Automation Platform modules bridging operational and security domains, teams can embed security into their CI/CD pipelines and GitOps workflows, making protection an integral part of the development lifecycle rather than an afterthought.
Together, these platforms deliver what enterprises actually need: a single control plane for operations and an effective security engine that adapts to workload reality, not the other way around. You get the flexibility of open infrastructure with the security assurance of zero trust, positioning your organization to handle current workloads confidently while being prepared for whatever comes next.
It's time to align infrastructure modernization with security evolution. For more information, explore these additional resources:
- [Solution Brief] VM-Series Software Firewalls and Red Hat OpenShift Virtualization
- [Webpage] Securing Red Hat Clusters with Prisma AIRS Runtime Security to Implement Zero Trust for Containerized and AI Apps
- [Blogpost] Prisma AIRS Helps Protect Containers and AI Apps Running on Red Hat OpenShift
- [Red Hat Ecosystem Catalogue] Palo Alto Networks VM-Series Software Firewalls
- [Red Hat Ecosystem Catalogue] Automate configuration with Red Hat and Palo Alto Networks
- [Webpage] Red Hat OpenShift Virtualization
- [Blog Post] Palo Alto Networks VM-Series Enhances Security for Virtualized Workloads on Red Hat OpenShift Virtualization
- [Use Case Documentation] Technology Partner Integration Guide
- [Solution Brief] Prisma AIRS and Red Hat OpenShift
Resource
15 reasons to adopt Red Hat OpenShift Virtualization
About the author
Simon is a passionate technologist, with over 25 years of experience working in the enterprise IT and cloud technologies space. Simon’s career trajectory has seen him working with a multitude of transformative technologies within the cloud and enterprise computing space, allowing him to stay at the forefront of industry trends.
Beyond his professional achievements, Simon is an advocate for technology's role in driving business innovation and efficiency. Simon's contribution to the field of enterprise IT and cloud technologies is not just through his work at Red Hat OpenShift but also through his active participation in various IT community forums, publications, and events.
More like this
Shadow-Soft shares top challenges holding organizations back from virtualization modernization
Improving VirtOps: Manage, migrate or modernize with Red Hat and Cisco
The Containers_Derby | Command Line Heroes
Can Kubernetes Help People Find Love? | Compiler
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Virtualization
The future of enterprise virtualization for your workloads on-premise or across clouds
