IT security is no longer the responsibility of a single, specialized team. To help protect your organization from growing cyber threats, IT security should be a priority for everyone. By integrating security processes and functions into every stage of the software development lifecycle, you not only better protect your products but you also build trust with your users. Here's how you can democratize security processes and make it a shared responsibility across your organization, while giving your developers what they need to create applications quickly.
Software supply chain security tools and concepts
There are several key tools and concepts that are critical to building more secure software supply chains and application lifecycles.
Software bill of materials
The first step towards a more secure software development process is understanding the contents of your software. A software bill of materials (SBOM) provides a detailed inventory of the components used in your projects, including internally developed code and open source libraries. This transparency helps you identify and track software components, making it easier to detect known vulnerabilities. Maintaining up-to-date SBOMs helps give team members the visibility they need to address security risks proactively, collaborate effectively and maintain a strong security posture.
Dependency management
Incorporating a software composition analysis (SCA) tool into your development process is crucial for managing dependencies. These tools scan your codebase for open source components and third-party libraries, then identify known vulnerabilities that can compromise your software. Regularly analyzing software dependencies helps you catch and address potential issues early, before they can be exploited. This proactive approach increases the overall security health of your software even as new vulnerabilities are discovered in the broader ecosystem.
DevSecOps practices
DevSecOps integrates security with DevOps practices, so security concepts are considered at every stage of development and deployment. One effective DevSecOps practice is to sign and verify code, container images and other artifacts. This helps you confirm the integrity and authenticity of your software and reduce the risk of tampering or introducing malicious code into your system. This practice not only helps to safeguard your code but it also reinforces the importance of security concepts across both development and IT operations teams.
Policy-as-code approaches
Automating security policies is another vital step in democratizing software security. Policy-as-code approaches let you codify security policies and enforce them automatically throughout your development process. By implementing supply-chain levels for software artifacts (SLSA) guidelines, you can streamline policy enforcement and provide more consistent security standards across all projects. This approach reduces human error and helps security remain a top priority at all stages of the software development lifecycle.
Vendor risk management
Third-party vendors play a significant role in most software projects, and managing the associated risks is essential. Automating package verification from third-party vendors helps make sure that the software you incorporate from external sources meets your security standards. By thoroughly vetting and verifying these packages, you can better protect your software from potential vulnerabilities introduced by third-party components.
Software supply chain security best practices
Enhancing the security posture of your software supply chain requires a comprehensive approach that goes beyond just development practices. Implementing industry-accepted security practices and standards helps you improve software resilience against threats and limit potential vulnerabilities. Here are some software supply chain security best practices to consider.
Vulnerability management
Effective vulnerability management involves identifying, assessing and mitigating vulnerabilities in your software. Regular vulnerability assessments help protect your software against known threats, and by staying current with the latest security practices, you can reduce the risk of breaches and improve the security posture of your entire software supply chain.
Scanning tools and capabilities
Investing in robust scanning tools can help you more effectively identify vulnerabilities within your systems. These tools can help you detect and address security flaws before they are exploited by attackers. Regularly scanning your codebase, infrastructure and applications helps you quickly address any issues that arise. The ability to identify and mitigate vulnerabilities in real time is a critical component of a security-focused software development lifecycle.
Accurate asset inventories
Maintaining accurate IT asset and application inventories is fundamental to effective security management. An accurate inventory lets you track systems and applications in use and verify that they have the proper levels of security and are up to date in terms of patching. By keeping a detailed record of your assets, you can more quickly identify systems that require security updates or patches to reduce the risk of unaddressed vulnerabilities.
Documented response programs
Documenting your vulnerability response, disclosure and handling program is important for implementing security practices across teams and projects. A well-documented program provides clear guidelines on how to respond to security incidents so teams can act quickly and efficiently when a vulnerability is discovered.
Security-focused development
Integrating security-focused practices into your software development and maintenance pipelines helps make sure that security is always top of mind. This includes incorporating security checks into your development processes, training your teams on secure coding practices and regularly reviewing and updating your security protocols. Adopting a shift-left approach and moving security considerations earlier in the development lifecycle will help your teams identify and mitigate vulnerabilities before they reach production. Additionally, implementing runtime security helps protect against threats in production environments by providing continuous monitoring.
Increase software supply chain security with Red Hat
Democratizing security in your software development lifecycle involves getting every team to take ownership of security. Red Hat offers a suite of tools that help you build security concepts into components, processes and practices in your software supply chain from the start. You can use these tools throughout your development lifecycle—and with your existing tools and infrastructure—to adopt security best practices across your organization.
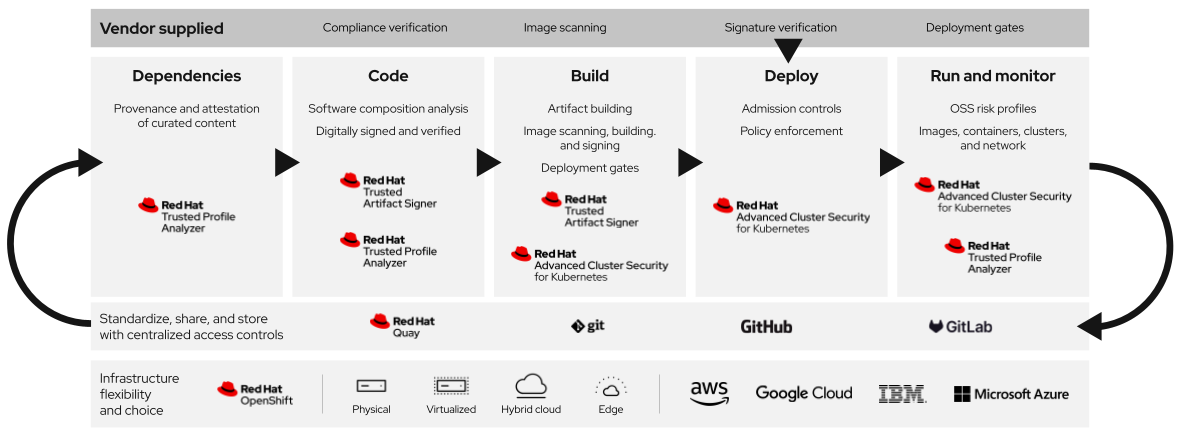
Learn how you can prevent and identify malicious code, safeguard build systems, and deploy continuous runtime monitoring with Red Hat Trusted Software Supply Chain.
Product trial
Red Hat Advanced Cluster Security Cloud Service | product trial
About the authors
Meg Foley is a Senior Principal Marketing Manager for Application Services Solutions at Red Hat. In this role, she is responsible for defining, researching, and advising customers on digital transformation and customer experience technologies and multi-product solutions. Foley has extensive experience in creating solutions that leverage AI and machine learning, integration, BPM, microservices, and lifecycle management.
Sudir Prasad is a Product Management and Engineering leader driving Secure Software Supply Chain and Data Services. His current focus is to unburden developers and enterprises in managing the risk of their open source software dependency portfolio, reducing development time and cost by remediating issues earlier in the development cycle. He wants to help customers leverage Red Hat's experience and expertise with enterprise hardening of open source in their applications.
More like this
AI trust through open collaboration: A new chapter for responsible innovation
The nervous system gets a soul: why sovereign cloud is telco’s real second act
Understanding AI Security Frameworks | Compiler
Data Security And AI | Compiler
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Virtualization
The future of enterprise virtualization for your workloads on-premise or across clouds

