So your organization is moving to Mastodon, and now everybody wants to be verified. For most users, a simple verification link is sufficient for identity checking, but for your corporate brand, you may want something backed up with cryptography. The technology has been in use for years, and you may already use it in chat or email. It's GnuPG, an implementation of PGP, and it's usable for Mastodon now, thanks to the open source project Keyoxide.
[ Check out this guide to boosting hybrid cloud security and protecting your business. ]
The process is simple. In fact, it's just four steps:
- Create a key pair.
- Add Ariadne Identity metadata to the key.
- Upload the key to OpenPGP.org and verify the key's email.
- Add a Keyoxide link to your organization's Mastodon profile.
Create a GPG key pair
You can create a GPG key pair using the gpg2 command from the GnuPG project:
$ gpg2 --full-generate-key
Follow the prompts until you have generated a key pair.
To get your key fingerprint, list your secret keys and find the one you've created for your organization:
$ gpg2 --list-secret-keys
The output displays your GnuPG keyring, containing at least one secret key. Locate the one you want to use for Mastodon, and find the long alphanumeric string just above a line starting with uid. That long number is your key's fingerprint. Here's an example:
sec rsa4096 2022-11-17 [SC]
22420E443871CF4313B9E90D50C9169F563E50CF
uid [ultimate] Tux <tux@example.com>
ssb rsa4096 2022-11-17 [E]
This example key's fingerprint is 22420E443871CF4313B9E90D50C9169F563E50CF. Copy that into a document because you'll need it a lot during this process.
[ Want to test your sysadmin skills? Take a skills assessment today. ]
Now you can add metadata to the key. Enter the GnuPG interface using the gpg2 --edit-key command along with the key's fingerprint:
$ gpg2 --edit-key 22420E443871CF4313B9E90D50C9169F563E50CF
At the GnuPG prompt, select the user ID (the key owner's name and email address) and designate it as the primary user. Each UID is numbered. In this example, there's only one user ID (uid [ultimate] Tux <tux@example.com>).
gpg> uid 1
gpg> primary
Add Ariadne metadata
For Keyoxide to recognize your Mastodon identity, you must add particular Ariadne metadata: The metadata must start with proof@ariadne.id= and be followed by the URL of your Mastodon profile page.
In this example, the URL is https://example.com/@tux:
gpg> notation
Enter the notation: proof@ariadne.id=http://example.com/@tux
gpg> save
Export your key and upload it to OpenPGP
Extract the public key and its metadata from your key ring:
$ gpg2 --armor --export \
22420E443871CF4313B9E90D50C9169F563E50CF > pubkey.asc
Open your web browser and navigate to keys.openpgp.org.
On the keys.openpgp.org website, click the Upload link to upload your exported key. Do this even if you have experience with GPG keys. Don't try to use --send-key to do this! This step is unique to the Keyoxide process.
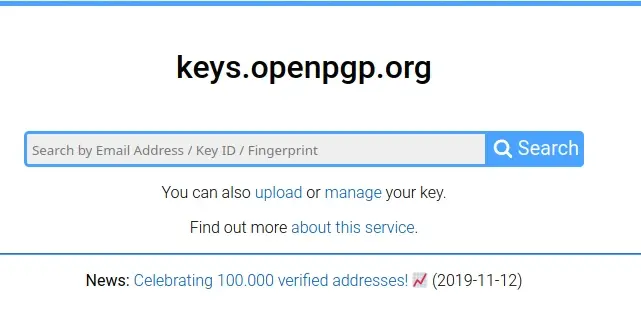
After you have uploaded your key, click the Send confirmation email button next to your email address to confirm that you own the email your key claims it belongs to. It can take 15 minutes or so, but when you receive an email from Openpgp.org, click the confirmation link to verify your email address.
Link Mastodon and Keyoxide
Now that you've set everything up, you can use Keyoxide as your verification link for Mastodon. Go to your Mastodon profile page and click the Edit profile link.
On the Edit profile page, scroll down to the Profile Metadata section. The Label field is arbitrary, so you can use terms like Verification or PGP or whatever you feel is appropriate.
In the Content field, type https://keyoxide.org/hkp/ followed by your key fingerprint. In this example, the full URL is https://keyoxide.org/hkp/22420E443871CF4313B9E90D50C9169F563E50CF.
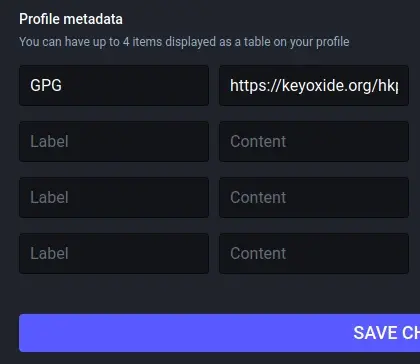
Click the Save button, and then return to your profile page.
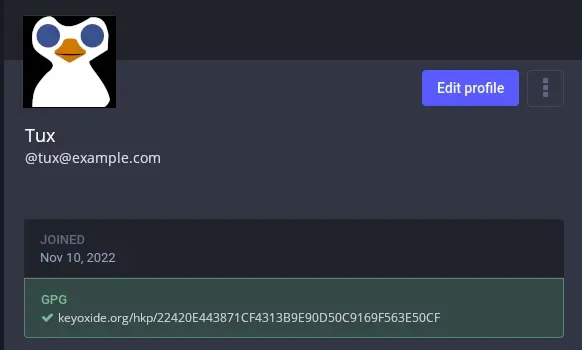
You can click the Keyoxide link in your profile to see your Keyoxide "profile" page. This page is actually just a rendering of the GnuPG key you created. Keyoxide's job is to parse your key and to be a valid destination when you need to link to it.
[ Learn how to manage your Linux environment for success. ]
Solve the identity problem
The advantage of GnuPG goes far beyond just being a destination for verification links. Thanks to digital signing, a PGP key can have an explicit chain of verification. Get your fellow sysadmins to sign your organization's key, and start building a ring of trust that goes far beyond the old blue Twitter checkmark. Help Mastodon show the internet how digital encryption, signing, and identity are supposed to work.
About the author
Seth Kenlon is a Linux geek, open source enthusiast, free culture advocate, and tabletop gamer. Between gigs in the film industry and the tech industry (not necessarily exclusive of one another), he likes to design games and hack on code (also not necessarily exclusive of one another).
More like this
MCP security: Implementing robust authentication and authorization
AI trust through open collaboration: A new chapter for responsible innovation
Post-quantum Cryptography | Compiler
Understanding AI Security Frameworks | Compiler
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Virtualization
The future of enterprise virtualization for your workloads on-premise or across clouds
