This is one story of how Red Hat Insights created a new recommendation to address a high impact vulnerability that might affect Red Hat customers. Red Hat Insights does this regularly for issues that involve Red Hat products, but what makes this one interesting is that it shows that Red Hat Insights can alert on high-visibility issues that are not delivered by Red Hat.
In this case, a 3rd party vulnerability was made public on September 16. Red Hat developed and tested a detection mechanism for the issue, then created a series of new Insights recommendations to enable our customers to detect it.
This answers two of the common questions we get about the Advisor service that is one of the services offered as a part of Red Hat Insights - how are new recommendations made, and how fast can they be created?

Red Hat Insights is a managed service that continuously analyzes platforms and applications to help enterprises manage hybrid cloud environments. Insights uses predictive analytics and deep domain expertise to reduce complex operational tasks from hours to minutes. Insights is included with your subscriptions for Red Hat Enterprise Linux, Red Hat OpenShift, and Red Hat Ansible Automation Platform.
The Advisor service is one of the most well-known services featured in Insights. This is the original Insights service where we take the knowledge and findings from Red Hat support and turn them into actionable and proactive recommendations through the Insights analytics. Insights also has a Vulnerability service, but in this instance we have a security issue that isn’t related to a CVE (Common Vulnerabilities and Exposures) in the Red Hat database. We include this issue in the Advisor service only.
How does a new recommendation get created? Let’s walk through an example using what just happened.
On September 16, news broke of an “Open Management Infrastructure Remote Code Execution Vulnerability.” Linux servers attached to certain Microsoft Azure services are exposed to this vulnerability. An HTTP/S listening port could allow remote code execution and provide root access to a server. This is a severe bug and many Linux systems, including Red Hat Enterprise Linux (RHEL) systems are affected. This is also an issue introduced in software that is not maintained by Red Hat. We want to make sure our customers are aware of it so that they can take appropriate action to protect their data and defend themselves from malevolent actors.
Once Red Hat was made aware of this vulnerability, we began assessing the impact. We got to work trying to figure out how we could make our customers aware of the problem. We immediately engaged in our process for creating a new insights recommendation for identifying the security vulnerability.
Red Hat teams around the globe worked to duplicate the exploit and document the method to find at-risk servers. A short time later Red Hat was able to create and enable new Insights recommendations highlighting multiple resolution options for Red Hat Enterprise Linux customers affected by this vulnerability.
This resulted in creating, testing, and implementing five recommendations for this issue with varying criticality based on the analysis performed by Insights.
This information will let you sort the systems and address the most critical issues based on your company’s needs.
-
If we detect that a vulnerable version of the Open Management Infrastructure (OMI) software is installed, but doesn’t appear to be running.
-
If we detect that a vulnerable version of the OMI software is installed and the process is running or the service is enabled.
-
If we detect that a vulnerable version of the OMI software is installed and is listening for connections.
-
If we detect that a vulnerable version of the OMI software is installed, is listening, and the network socket is externally accessible.
-
If we detect that a vulnerable version of the OMI software was installed by a method other than rpm. Since we can’t check the OMI software version we default to critical out of an overabundance of caution.
If you are running RHEL in Azure, please check the Insights Microsoft Azure topic as soon as possible. If you are impacted by this issue, you’ll see it listed in the list of recommendations.
If the problem does not affect you, you will need to clear the “Systems impacted 1 or more” filter to see the new recommendations listed.
Microsoft is providing remediation guidance for this issue on the Microsoft Security Response Center. This is an evolving situation and users should check the Microsoft Security Response Center for updates.

If you are already using Insights and if you have opted in to email notifications, then you would have already received an email notification about any impacted systems. Here is an example one of our team members received:
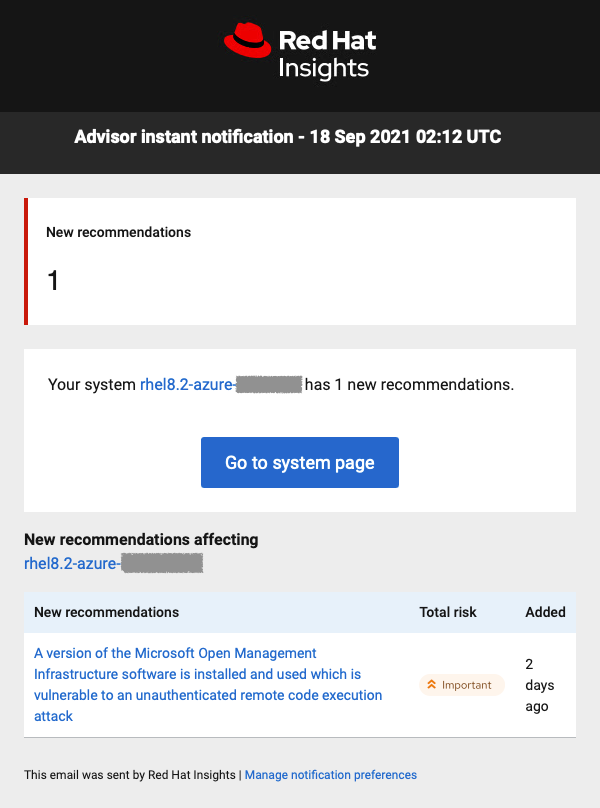
Not using Insights yet? We hope you will try it!
Registration is fast and easy. More information about how to register to Insights can be found within Insights or on the Red Hat Insights Get Started page.
Do you have questions about security and how Insights handles metadata? All of that information can be found on our Insights Data & Application Security page.
We think this is an excellent example of Red Hat’s focus on the customer: The predictive and proactive analysis of Red Hat Insights and the Hybrid Cloud Console at cloud.redhat.com enables them to better manage unexpected vulnerabilities and potential exploits.
Even if you aren’t impacted by this specific issue, it is a great example of the value that you receive from the Red Hat subscription and included capabilities like Red Hat Insights.
For more information about the OMI Vulnerability, visit the Microsoft Threat Intelligence Center blog, Hunting for OMI Vulnerability Exploitation with Azure Sentinel.
執筆者紹介
John Spinks is a Senior Principal Technical Marketing Manager for Red Hat. He acts as a subject matter expert for Red Hat Management products including Satellite and Insights. Previous experience includes almost 10 years as a Technical Marketing Engineer for NetApp in RTP, NC.
チャンネル別に見る
自動化
テクノロジー、チームおよび環境に関する IT 自動化の最新情報
AI (人工知能)
お客様が AI ワークロードをどこでも自由に実行することを可能にするプラットフォームについてのアップデート
オープン・ハイブリッドクラウド
ハイブリッドクラウドで柔軟に未来を築く方法をご確認ください。
セキュリティ
環境やテクノロジー全体に及ぶリスクを軽減する方法に関する最新情報
エッジコンピューティング
エッジでの運用を単純化するプラットフォームのアップデート
インフラストラクチャ
世界有数のエンタープライズ向け Linux プラットフォームの最新情報
アプリケーション
アプリケーションの最も困難な課題に対する Red Hat ソリューションの詳細
仮想化
オンプレミスまたは複数クラウドでのワークロードに対応するエンタープライズ仮想化の将来についてご覧ください
