This article is the first in a two-part series. Here we take a step back and look at the evolving IT security risk landscape and how it is impacting organizations, after which we'll look at a suggested automated compliance architecture. In part two, we will demonstrate what the automated compliance architecture can look like in action when using Red Hat Insights and Red Hat Ansible Automation Platform.
Anyone who has owned or been in a car has probably seen at least one or more symbols appear on a car’s dashboard. The dashboard indicates when an issue has arisen that requires attention. You'll often find that when an issue is not addressed, it ends up consuming more of the car owner’s time and energy, and increases their levels of stress. Are those consequences worth the risk of not quickly dealing with warnings and advisories when they appear, before they have the chance to become a problem in the first place?
When it comes to your organization’s adherence to regulatory and security compliance requirements, Red Hat can perform as your dashboard and mechanic using Insights and Ansible Automation Platform, helping you stay ahead of the curve and remain compliant.
The evolving risk landscape
According to a 2020 Gartner report, 75% of CIOs are investing to improve cyber-risk mitigation, and it's likely that this figure has increased in the past couple of years. While an organization pursues improving its cyber-risk mitigation, it will at the same time have to meet compliance and regulatory requirements, adding another layer of complexity.
Security compliance determines if a system follows the rules written out in a compliance policy. There are various regulatory standards that are required on an ongoing basis. Examples include National Institute of Standards and Technology (NIST, providing guidelines on technology-related matters), Payment Card Industry Data Security Standard (PCI-DSS, for protecting yourself and customers when taking payments), among many others. The Centre of Internet Security (CIS) standard is our focus in this article. CIS is a non-profit that endeavours to safeguard public and private organizatons against cyber threats.
It is important to note that there is no such thing as a standard security policy. Policies vary across different organizations and even across systems within the same organization. Systems have different purposes, and systems can have different levels of importance. There really is no one-size-fits-all approach to security compliance.
Why should you care? When it comes to compliance, the solutions you adopt impact executives and associates throughout your organization. The considerations that each role takes into account regarding compliance varies. Let’s walk through two key personas — the Chief Information Security Officer (CISO) and the System Administrator.
A CISO’s considerations include:
Driving flexibility and agility in technologies and infrastructure while maintaining an appropriate security posture
Meeting compliance and governance requirements
Avoiding negative headlines stemming from IT outages or security breaches
A System Administrator’s (or in bigger establishments, a Security Administrator's) considerations include:
Developing and supporting organizational security standards, best practices, preventative measures and disaster recovery plans
Monitoring networks for security breaches, investigating violations as they occur
Implementing and updating software to protect data
In 2021, Gartner reported that customers lose $300,000 per hour on average during IT downtime. According to the report, the cost is dependent on many factors, including revenue, industry, duration of the outage, number of individuals impacted and the time of day that the outage occurs.
Examples of where significant monetary losses can be observed are detailed in the report — companies that rely on high-data transactions such as banks and online retail sales will see a spike in their numbers, as will services that experience an outage during a peak usage times of day. As a result, companies are looking for solutions to manage sprawl, reduce risk and better work with limited resources. Red Hat has solutions that can help to address these challenges such as Red Hat Satellite, Ansible Automation Platform and Insights.
Compliance architecture
We will now look at how some of these technologies can work together to produce a more suitable compliance architecture.
It's said that automation happens when someone meets a problem they never want to solve again. But where can you start? Red Hat works with a project on GitHub called Compliance as Code (CaC). The CaC project has a framework to develop compliance content in an automated fashion. It’s more than configuration management — it is about securing containers, operating systems, applications, container platforms and services, and demonstrating it all. This ultimately all feeds into the OpenSCAP project.
OpenSCAP is validated and certified by NIST, and is Red Hat’s chosen security scanner that is frequently used with Red Hat Enterprise Linux (RHEL) and Satellite subscriptions. OpenSCAP performs known vulnerability and security compliance scanning, and has automation support — in fact, many Ansible remediation playbooks are provided and supported by Red Hat.
Using OpenSCAP, you can go one step further and produce customizable content through the SCAP Workbench graphical interface. We understand that different organizations can have their own bespoke set of processes that look to meet set standards, and the power of the OpenSCAP platform is that it is very easy to customize policies in a way that reflects an organization's own processes. We'll show you an example of how to approach this in the second part of this series, but there are different ways to go about it.
As mentioned earlier in this article, CIS endeavors to help safeguard public and private organizations from cyber threats. One way this is done is through the implementing of CIS benchmarks — documented industry best practices for security configuring IT systems, software and networks. A benchmark profile (Figure 1) — available to view from the easily downloadable CIS Benchmarks PDFs — typically includes:
The benchmark profile overview title
Where the profile is applicable (a server or workstation) and whether it is a Level 1 or Level 2 profile, where Level 2 has more secure requirements
A description of the profile
The rationale for the benchmark profile

Figure 1: Benchmark profile 5.2.11 (CIS Red Hat Enterprise Linux 8 Benchmark v2.0.0)
Fortunately, the remediation required to meet the benchmark profile is also provided by the documentation:

Figure 2: Remediation for benchmark profile 5.2.11
Below is an example extract of how the above profile could be easily implemented using an Ansible playbook:
- name: ssh disable PermitEmptyPasswords lineinfile: state: present dest: /etc/ssh/sshd_config regexp: ^#?PermitEmptyPasswords line: PermitEmptyPassword no notify: restart sshd
How Ansible Automation Platform and OpenSCAP work together
As we have now observed how Red Hat Ansible Automation Platform can aid in compliance, how can the platformand OpenSCAP work together in an automated fashion?
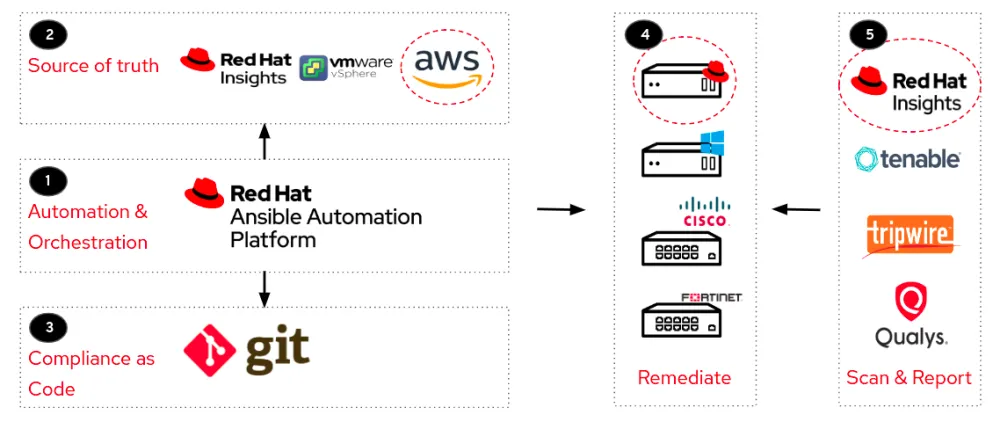
Figure 3: Automated compliance workflow
With reference to Figure 3, the envisioned workflow is as follows:
The Ansible dynamic plugin will go to the source of truth to discover the registered nodes that need to be managed
The source of truth is a required platform for your registered nodes, examples include Red Hat Insights, VMware and AWS
Code is required to actually remediate changes — the code is taken from Git, where you’re able to extract the right rules and playbooks to feed into Ansible Automation Platform
You’re now ready to remediate against any device that you want, whether it is a Linux server, Windows, Cisco, or any other device of your choosing
Finally, you’ll want to know the state that your host is in with its remediation state by conducting pre- and post-scans — you could utilize tools to give you such visibility such as OpenSCAP within Red Hat Insights, Tenable and Tripwire
The icons circled with a red dotted line in Figure 3 are what we will use for our remediation walkthrough in part two, but this workflow serves to demonstrate that the use cases are endless. You may also notice that Insights features in a couple areas of the workflow. As we will be using Insights predominantly in the remediation, it is useful to know how it helps you to proactively manage your level of compliance.
Red Hat Insights is a Software-as-a-Service (SaaS) offering available on the Hybrid Cloud Console. Insights allows you to analyze, proactively foresee what is going on across your IT estate, and triage risks that are going to prevent you from operating at your best from a technology perspective. Insights can also give you recommendations through its Advisor service, as well as automate the provided remediations.
Even if you are not the person who would be directly using Insights or administering a Red Hat environment, there is additional value that Insights brings to a business.
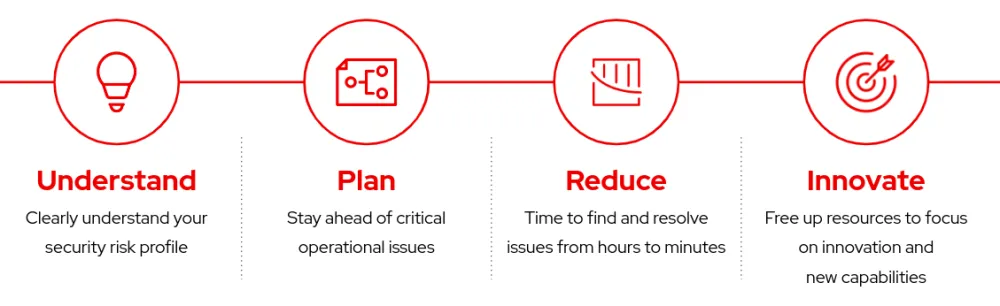
Figure 4: High-level benefits of Red Hat Insights to an organization
Need to know if the latest vulnerability affects your business? Insights can pull a list in seconds from all registered systems.
Have systems been affected by that said vulnerability? Insights will generate a playbook that you can run manually to fix them. If you'd rather automate this, you can connect Satellite to Insights with Cloud Connector and automate the remediations with the click of a button.
This ultimately helps teams move from a reactive to proactive model — instead of reacting to the incident underway, teams can proactively reduce the risk before the incident occurs, giving them the freedom to focus on more strategic and higher-value initiatives important to the business.
Compliance service within Red Hat Insights
The compliance service offered within Insights is built on OpenSCAP reporting. This helps customers assess, monitor, report and remediate internal and external regulatory and compliance requirements in their Red Hat environment.

Figure 5: Compliance service dashboard observed from Red Hat Insights console
Within the compliance service, you can evaluate a system against policies included in the system security guide for RHEL, or can create your own policy from scratch.
The compliance service will highlight if the version of OpenSCAP being used is not supported with the version of RHEL in use (Figure 5). And, if you have systems that are assigned to the host but not reporting to Insights at all, this can also be easily observed on the console.
For each policy you will be able to see the number of systems being evaluated against the policy, as well as the level of compliance to the policy. Each policy has a configurable threshold so that you can set risk thresholds at application levels.
You also have the choice to customize rules that are part of policies using the compliance service and quickly start to monitor them. Alternatively, you can use SCAP workbench to customize policies. However, if you choose to tailor policies within the SCAP workbench, Insights will be unable to check for the tailored changes — you will have to make the changes directly within Insights.
Please note, deploying OpenSCAP on RHEL is a brute force approach for each system. There are ways to scale up, however, such as using Red Hat Satellite connected to Insights with the use of Cloud Connector, allowing you to deploy many — even hundreds or thousands — of systems with relative ease.
To summarize, when it comes to your organization’s compliance management, Insights performs simultaneously as your dashboard and check up, enabling you to proactively foresee and nip those advisories in the bud with the help of your trusty mechanic, Ansible.
Learn more
About the author
Ally Kouao is a Portfolio Solution Architect based in the UK, who joined Red Hat in 2019. Her areas of interest and expertise encompass all things to do with security and automation.
More like this
IT automation with agentic AI: Introducing the MCP server for Red Hat Ansible Automation Platform
Introducing OpenShift Service Mesh 3.2 with Istio’s ambient mode
Data Security 101 | Compiler
AI Is Changing The Threat Landscape | Compiler
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Virtualization
The future of enterprise virtualization for your workloads on-premise or across clouds
