In many environments today, security is one of the top priorities. New information security vulnerabilities are discovered regularly, and these incidents can have a significant impact on businesses and their customers. Red Hat customers I talk to are frequently looking for tools they can use to help evaluate and secure their environments.
One of these tools is OpenSCAP, which is included in Red Hat Enterprise Linux (RHEL), and can perform compliance and vulnerability scanning on RHEL servers. Satellite makes OpenSCAP easier to use by allowing you to deploy the OpenSCAP agent to hosts, manage the OpenSCAP policies centrally, and to view OpenSCAP reports from the Satellite web interface.
A number of OpenSCAP profiles are included, such as STIG, PCI-DSS, and HIPAA, among others. It is also possible to customize the included profiles (using OpenSCAP tailoring files), or create your own custom profile specific to your environment. These compliance and vulnerability scans can be configured to run at a regular interval, and reports generated by these scans can be viewed right from the Satellite web interface.
Many of the provided profiles include shell and Ansible snippets that can be used to remediate some of the findings. For example, the OpenSCAP profile you are using might specify that the root user should not be able to login over SSH. If the server being scanned doesn’t meet this requirement, the OpenSCAP report displayed in the Satellite web interface will display a shell script or Ansible snippet that can be used to disable remote root logins so the system meets this requirement.

On Red Hat Satellite 6.5 and earlier versions, Puppet was required to deploy and configure OpenSCAP on Satellite clients. Satellite 6.6 introduces the ability to deploy and configure OpenSCAP using Ansible (and also still includes the option to use Puppet).
In this post, I will cover how to get started with OpenSCAP on Satellite 6.6 using Ansible.
Setting Up Remote Execution
Satellite uses the existing remote execution functionality to run Ansible roles on remote hosts, therefore, you must have remote execution working in the environment.
To test if remote execution is working, log in to the Satellite web interface, go to the Hosts menu, and select All Hosts. The next step is to select all of the hosts you would like to use Ansible with, go to the Select Action drop down menu, and select Schedule Remote Job. We can leave the Job category set to Ansible Commands and the Job template set to Run Command - Ansible Default. For the command, we will specify hostname as a simple test command to run, as shown:
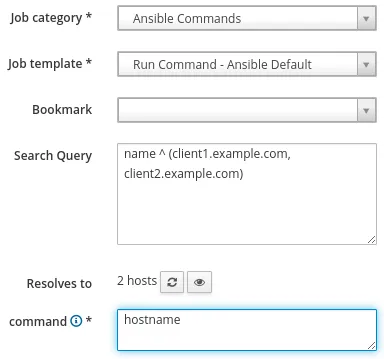
If the results for the remote job are successful on all of your hosts, then remote execution is working in your environment. If some or all of your hosts failed, you need to setup remote execution. There could be a number of issues causing a failure, but the most frequent is the SSH keys not being distributed to your hosts. See the documentation for information on how to distribute the SSH keys. Other issues that can cause remote execution failures are hostname resolution issues, remote servers being inaccessible or down, firewalls blocking SSH traffic, etc.
Other Prerequisites
In my environment, I created and published a content view that contains the RHEL 7 and Satellite Tools repositories. I then configured my Satellite clients to use this content view. It is required that the hosts using OpenSCAP have access to the Satellite Tools repository, as this is where the OpenSCAP software will be installed from.
We also need to provide some OpenSCAP content to Satellite to use for the scans. We can either use the default OpenSCAP content included in RHEL, or upload our own custom content. In this example, we will be using the built in content, and importing it into Satellite by running the following command on the Satellite host:
# foreman-rake foreman_openscap:bulk_upload:default
Once the default OpenSCAP content is imported, we can view it from the Satellite web interface by going to the Hosts menu, and selecting SCAP Contents.

Importing the Foreman SCAP Client Ansible Role and Variables
The Foreman SCAP Client Ansible role is what will deploy and configure the OpenSCAP client on our Satellite hosts. This Ansible role is included in Satellite 6.6, however, it is not imported by default as not all customers will use it.
To import this Ansible Role, from the Satellite web interface, select the Configure menu item, and then Roles. Click on the Import from <Satellite or capsule hostname> button as shown in the screenshot:
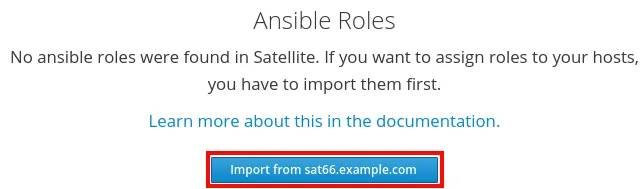
A list of Ansible Roles available to be imported will be displayed. Check the box for theforeman.foreman_scap_client and click the Update button, as shown:

Next, we need to import the Ansible Variables for this role. To do this, select the Configure menu, and select Variables (under the Ansible heading). From here, click on the Import from <Satellite hostname> button as shown in the screenshot:
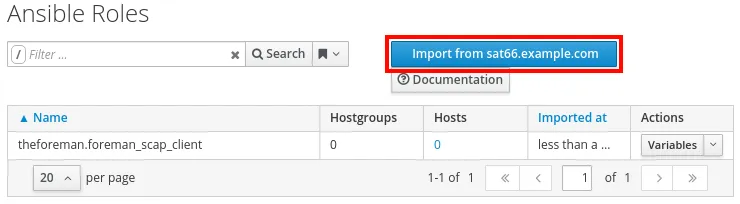
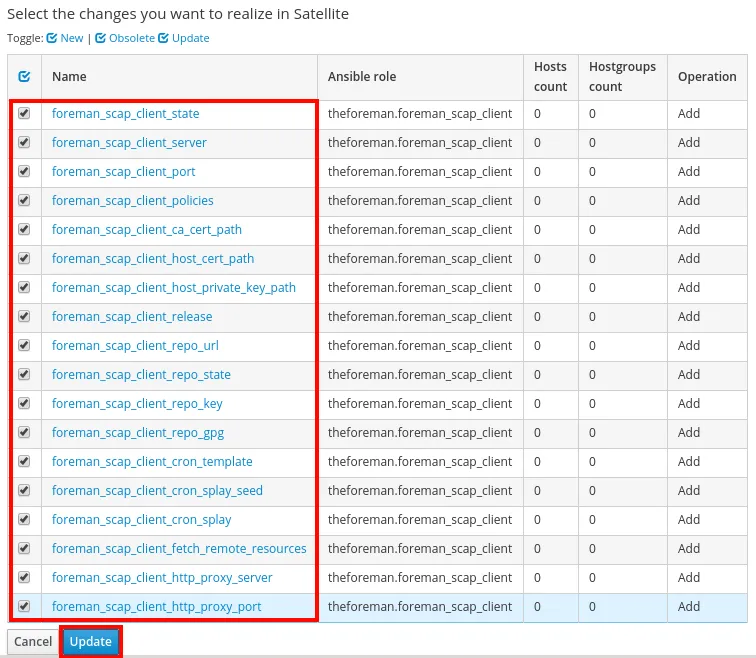
A list of Ansible variables available to be imported is shown. Select all of the foreman_scap_client variables, and click update:
Creating a Host Group
Our next task will be to create a Host Group in Satellite, or to update an existing Host Group. A Host Group, among other functionalities, provides the ability to assign the theforeman.foreman_scap_client Ansible role to a group of hosts.
To create the Host Group go to the Configure menu and select Host Groups. You then click the blue Create Host Group button in the upper right side of the page. In this example, we will give the Host Group a name of OpenSCAP Clients, and select the appropriate Lifecycle Environment, Content View, Content Source, and OpenSCAP Capsule, as shown in this screenshot:
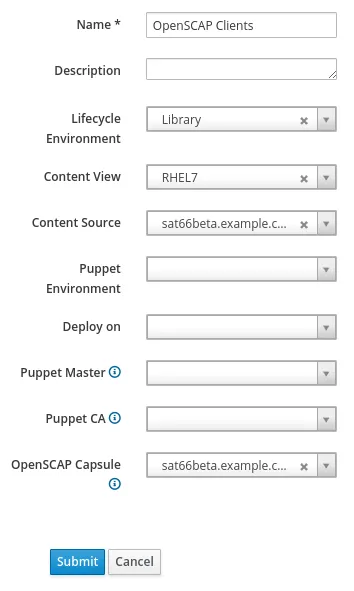
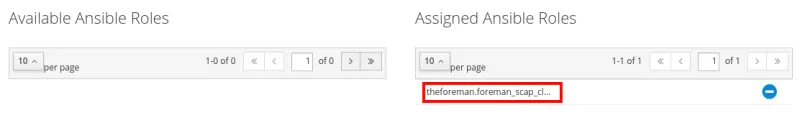
The next step will be to click on the Ansible Roles tab and add the theforeman.foreman_scap_client role by selecting the plus sign under Available Ansible Roles, which moves it to Assigned Ansible Roles:
Also check the Organizations and Locations tabs and ensure the proper items are selected for your environment.
Finally, click the Submit button to create the Host Group.
Assigning Hosts to Host Group
Now that the Host Group has been created, we need to assign the Satellite Hosts we want to use OpenSCAP to be included in the Host Group.
To do this, go to the Hosts menu item, and select All Hosts. You then select the hosts to add and click the Select Action drop down menu, and click Change Group. In this example, I will be working with the client1.example.com and client2.example.com hosts, as shown in the screenshot:
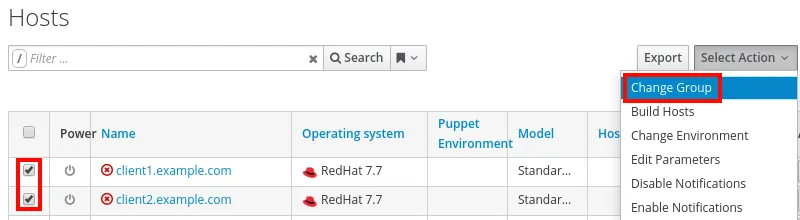
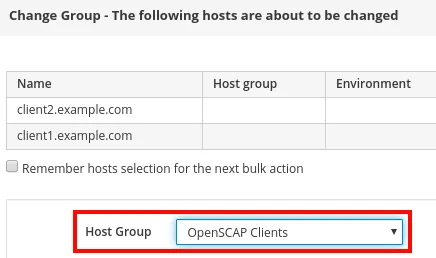
The Change Group window will pop up, and you can select OpenSCAP Clients from the Host Group dropdown menu, then click Submit:
Creating the OpenSCAP Policy in Satellite
The next step in the process is to create a OpenSCAP Policy within Satellite. This policy will define which SCAP content, XCCDF profile, and tailoring file to use. It will also define the schedule the scans should be run on.
To do this, go to the Hosts menu, and select Policies (under the Compliance header). You’ll then click on the New Policy button, which will bring up a wizard screen with several steps.
The first prompt asks which deployment option should be used for this compliance policy. We will select Ansible:
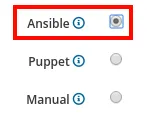
The next prompt will ask for a name and description for the policy. In this example, we will name it STIG.
On the SCAP Content prompt, we need to specify which SCAP content and XCCDF Profile to use, and an optional tailoring file to use. In this example, we will specify the Red Hat rhel7 default content, the DISA STIG for Red Hat Enterprise Linux 7, and will not specify a tailoring file, as shown:

Next, we will specify that the policy should be run weekly on Wednesdays:

On the next two prompts, we will specify the appropriate Locations and Organizations.
Finally, on the last prompt, we will select our OpenSCAP Clients Host Group, as shown, and click Submit:
Running the Foreman SCAP Client Ansible Role
We are now ready to run the theforeman.foreman_scap_client Ansible role on our Satellite hosts in the OpenSCAP Clients host group. This Ansible role will install and configure the OpenSCAP agent on these Satellite hosts, and also set up the appropriate cron job per the schedule we specified in the OpenSCAP policy we previously created.
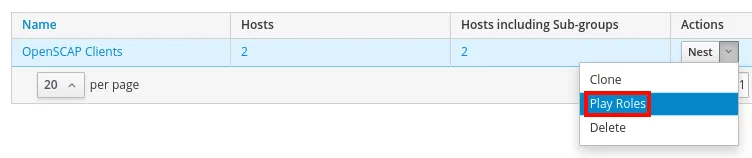
To run the Ansible role on all the hosts in the Host Group, we can go to the Configure menu and select Host Groups. We can then press the down arrow under Actions for the OpenSCAP Clients Group, and select Play Roles:
You will need to verify the Ansible role successfully completes on the hosts, as indicated by the green result:
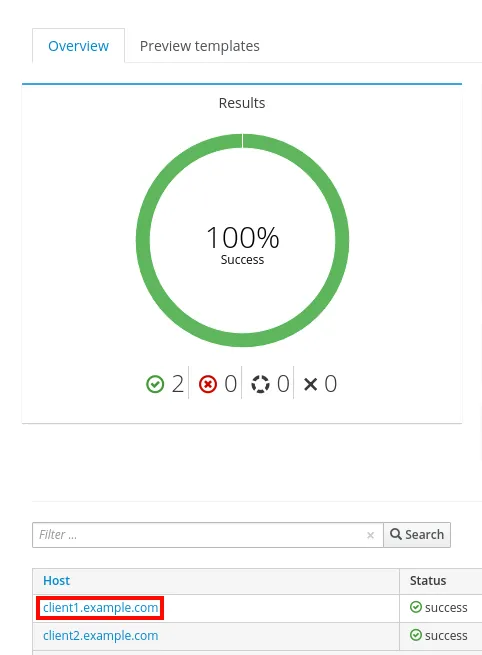
If you click on a host at the bottom of the screen, you can see the details of the Ansible role run:
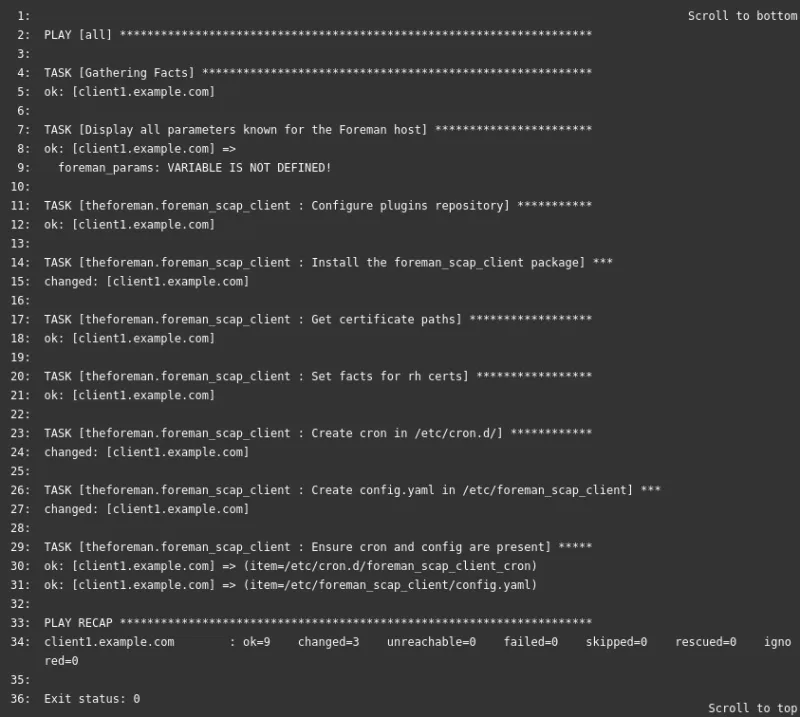
Verifying Hosts were Configured for OpenSCAP
We will now login to client1.example.com and verify it was configured for OpenSCAP by Ansible. We can use the yum history and yum history info commands to determine which packages were installed when the Ansible role ran:
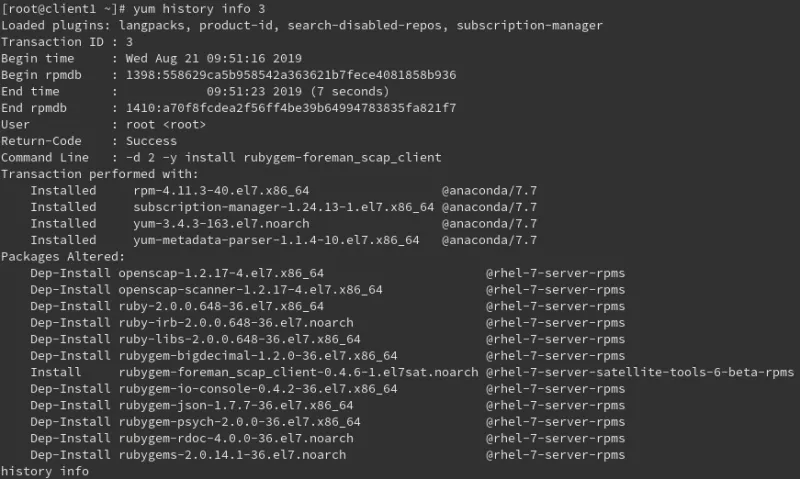
We can see that the rubygem-foreman_scap_client package was installed from the Satellite Tools repository, and that there were several dependencies installed from the RHEL 7 servers repository.
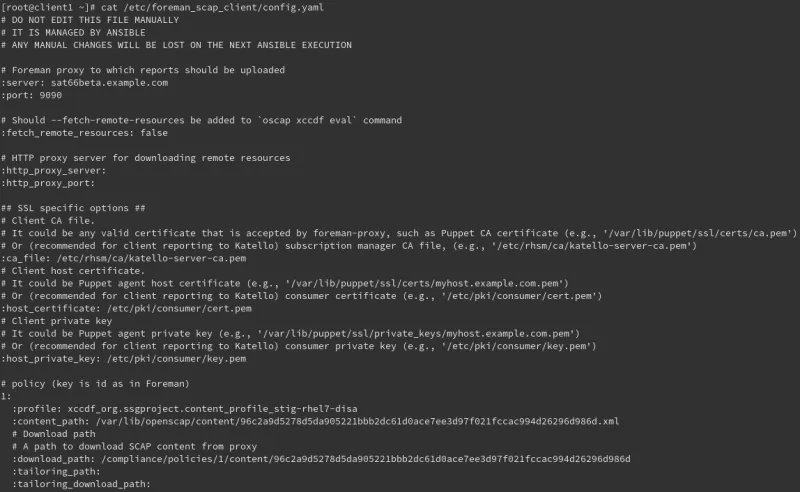
Ansible also created the /etc/foreman_scap_client/config.yaml file, which was configured to upload the report to the Satellite server, and use the STIG profile we specified in the Compliance Policy earlier:
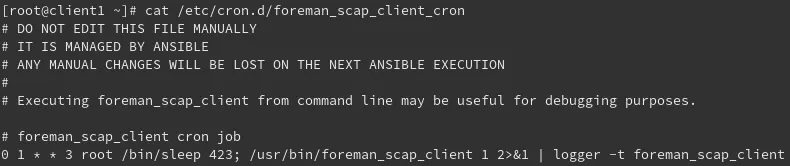
We can also see a /etc/cron.d/foreman_scap_client_cron file was created and set up to run the scan every Wednesday as we specified in the Compliance Policy earlier:
We can wait until next Wednesday for the scan to run, or we can manually run the command from the cron configuration to kick off a scan immediately. In this example, I ran the command specified manually in the cron file:
# /usr/bin/foreman_scap_client 1 2>&1 | logger -t foreman_scap_client
This will run the scan and upload the results to Satellite. In the next section, we will view the report.
Viewing the Compliance Report from Satellite
We can view the report that was uploaded to Satellite by going to the Hosts menu and selecting Reports (under the Compliance header).
All of the available reports will be listed, as well as a summary of how many checks passed, failed, or had other results, as shown.
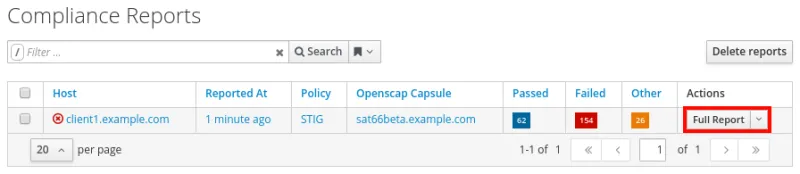
If we click on Full Report under the Actions column, we can see the details of the report.

We can then scroll through the report and see the rules that were evaluated. In this example, we will select the Disable SSH Root Login item to see more details for this rule.

At the bottom of this screen, we can click the show link to display a remediation shell script, or remediation Ansible snippet, either of which would remediate this issue.
Summary and Closing
OpenSCAP is a useful, powerful tool to scan servers for compliance and vulnerability assessments. Satellite offers the ability to deploy OpenSCAP clients, and with Satellite 6.6, the option to do this with Ansible is now available.
About the author
Brian Smith is a product manager at Red Hat focused on RHEL automation and management. He has been at Red Hat since 2018, previously working with public sector customers as a technical account manager (TAM).
More like this
Redefining automation governance: From execution to observability at Bradesco
More than meets the eye: Behind the scenes of Red Hat Enterprise Linux 10 (Part 5)
Technically Speaking | Taming AI agents with observability
How Do We Make Updates Less Annoying? | Compiler
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Virtualization
The future of enterprise virtualization for your workloads on-premise or across clouds
