I imagine I am not the only systems administrator who struggled with driving security compliance across a disparate fleet of Linux systems. It took up hours of administrative time and often required interaction with a third-party auditor to validate the results.
Let’s talk about the multiplication here: You may have a batch of systems that handle payment processing, so they are required to comply with the rules for PCI-DSS. You may have another set of systems that handle your patient’s medical records, which would fall under the purview of HIPAA. Many of these certifications require compliance in over a hundred points. Multiply that by dozens of systems in each environment, and multiply that again by multiple environments (dev, prod, etc.), and now you have thousands of line items that need to be reviewed every quarter.
For me, that took the form of an Excel spreadsheet where each sheet represented an individual server. I can’t tell you how often my laptop would lock up because Excel would crash trying to load all the data! I will show you how those spreadsheets and hours of toil can now be a practice of the past. To do so, we’ll need the Red Hat Enterprise Linux image builder and an OpenSCAP profile.
Getting setup with image builder
To get started building out our compliant golden image, we’ll need the image builder tools. There are three different image builder tools: the command line (CLI), web console and hosted service. Each option has advantages, but that is a discussion for a different day.
With RHEL 9.2, the CLI and the self-hosted versions were given added functionality to include OpenSCAP profiles into the base image! At this stage, the command line utility, composer, is a bit more straightforward when selecting a profile and exporting a blueprint.
What we’ll need first is a RHEL 9.2 server with all the necessary packages installed:
$ sudo dnf install -y osbuild-composer composer-cli cockpit-composer bash-completion scap-security-guide openscap-utils openscap-scanner Updating Subscription Management repositories. Last metadata expiration check: 0:17:24 ago on Wed Jun 7 15:27:03 2023. Package osbuild-composer-76-2.el9_2.2.x86_64 is already installed. Package weldr-client-35.9-1.el9.x86_64 is already installed. Package cockpit-composer-45-1.el9_2.noarch is already installed. Package bash-completion-1:2.11-4.el9.noarch is already installed. Package scap-security-guide-0.1.66-1.el9_1.noarch is already installed. Package openscap-utils-1:1.3.7-1.el9.x86_64 is already installed. Package openscap-scanner-1:1.3.7-1.el9.x86_64 is already installed. Dependencies resolved. Nothing to do. Complete!
Next, we need to configure our build node to include all the appropriate user groups and services:
$ sudo usermod -a -G weldr $USER # Note: You’ll need to log out and back in for this to take effect.
$ sudo systemctl enable --now cockpit.socket
$ sudo systemctl enable --now osbuild-composer.socket
$ sudo firewall-cmd --add-service=cockpit && sudo firewall-cmd --add-service=cockpit --permanent
success
success
$ source /etc/bash_completion.d/composer-cli
$ composer-cli status show
API server status:
Database version: 0
Database supported: true
Schema version: 0
API version: 1
Backend: osbuild-composer
Build: NEVRA:osbuild-composer-76-2.el9_2.2.x86_64
With that, our image builder tool is ready to use! Next, we need to select an OpenSCAP profile.
What is an OpenSCAP profile?
SCAP stands for Security Content Automation Protocol and is a standard maintained by NIST (the National Institute of Standards and Technology). In essence, SCAP is an agreed-upon framework for setting certification standards globally or across industries and verticals. OpenSCAP, by extension, is an open source project to build and maintain tools to help implement SCAP profiles.
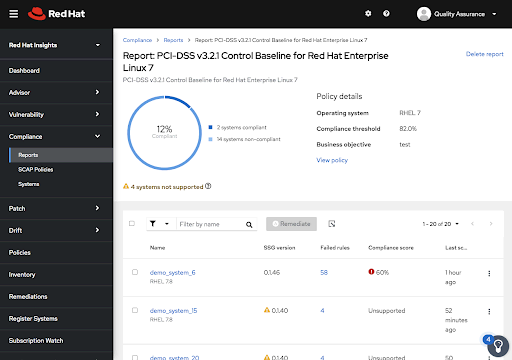
Red Hat Insights report for PCI-DSS Compliance
Red Hat has been working with various partners and organizations to make OpenSCAP tools and their dependent security profiles first-class citizens within the RHEL distribution and, by extension, our entire portfolio of tools. The recent image builder updates are the next logical step!
Now that we have configured our image builder tool, we need to select a compliance policy and export it into a format that image builder can use. There are several dozen policies to choose from. Some of the more recognizable are:
- CIS Benchmarks (Center for Internet Security)
- DISA STIG (Defense Information Systems Agency)
- PCI-DSS (protects payment card data)
- HIPAA (Health Insurance Portability and Accountability Act of 1996)
For our purposes, we will choose one of the more “generic” policies. CIS is a general-purpose compliance profile with two types (workstation and server) and two levels (1 and 2).
Back on our RHEL 9.2 server, let’s take a look at what is included in an OpenSCAP profile:
$ ls -l /usr/share/xml/scap/ssg/content/ total 22548 -rw-r--r--. 1 root root 23088822 Feb 14 07:34 ssg-rhel9-ds.xml
If we then use the oscap utility, we can take a look at the CIS-specific entries:
$ oscap info --profile cis /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
Document type: Source Data Stream
Imported: 2023-02-14T07:34:39
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-rhel9-xccdf.xml
Generated: (null)
Version: 1.3
WARNING: Datastream component 'scap_org.open-scap_cref_security-data-oval-com.redhat.rhsa-RHEL9.xml.bz2' points out to the remote 'https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml.bz2'. Use '--fetch-remote-resources' option to download it.
WARNING: Skipping 'https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml.bz2' file which is referenced from datastream
Profile
Title: CIS Red Hat Enterprise Linux 9 Benchmark for Level 2 - Server
Id: xccdf_org.ssgproject.content_profile_cis
Description: This profile defines a baseline that aligns to the "Level 2 - Server" configuration from the Center for Internet Security® Red Hat Enterprise Linux 9 Benchmark™, v1.0.0, released 2022-11-28. This profile includes Center for Internet Security® Red Hat Enterprise Linux 9 CIS Benchmarks™ content.
This provides us with some important logistical information and links to additional resources. In order to put this profile into use, we need to export the configuration into a TOML file that image builder can use:
$ oscap xccdf generate fix --profile cis --fix-type blueprint --skip-validation /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml > RHEL9-CISL2.toml
This command exports the CIS configuration into a blueprint file called RHEL9-CISL2.toml. In the next section, we’ll look at a graphical output of what this blueprint does, but first we need to ingest that blueprint into the composer-cli tool (the command version of image builder):
$ composer-cli blueprints push RHEL9-CISL2.toml
Deploying a CIS-compliant image
Now that we have set up image builder, picked a security profile and converted that profile into a blueprint, it is time to validate our image configuration, add a few custom changes and deploy a new image!
In a browser tab, navigate to https://<YOUR_SERVER_NAME>:9090/composer and log in with the user you did the previous steps. You’ll see a blueprint called “xccdf_org.ssgproject.content_profile_cis”. When you open this blueprint, you’ll notice it is not empty!
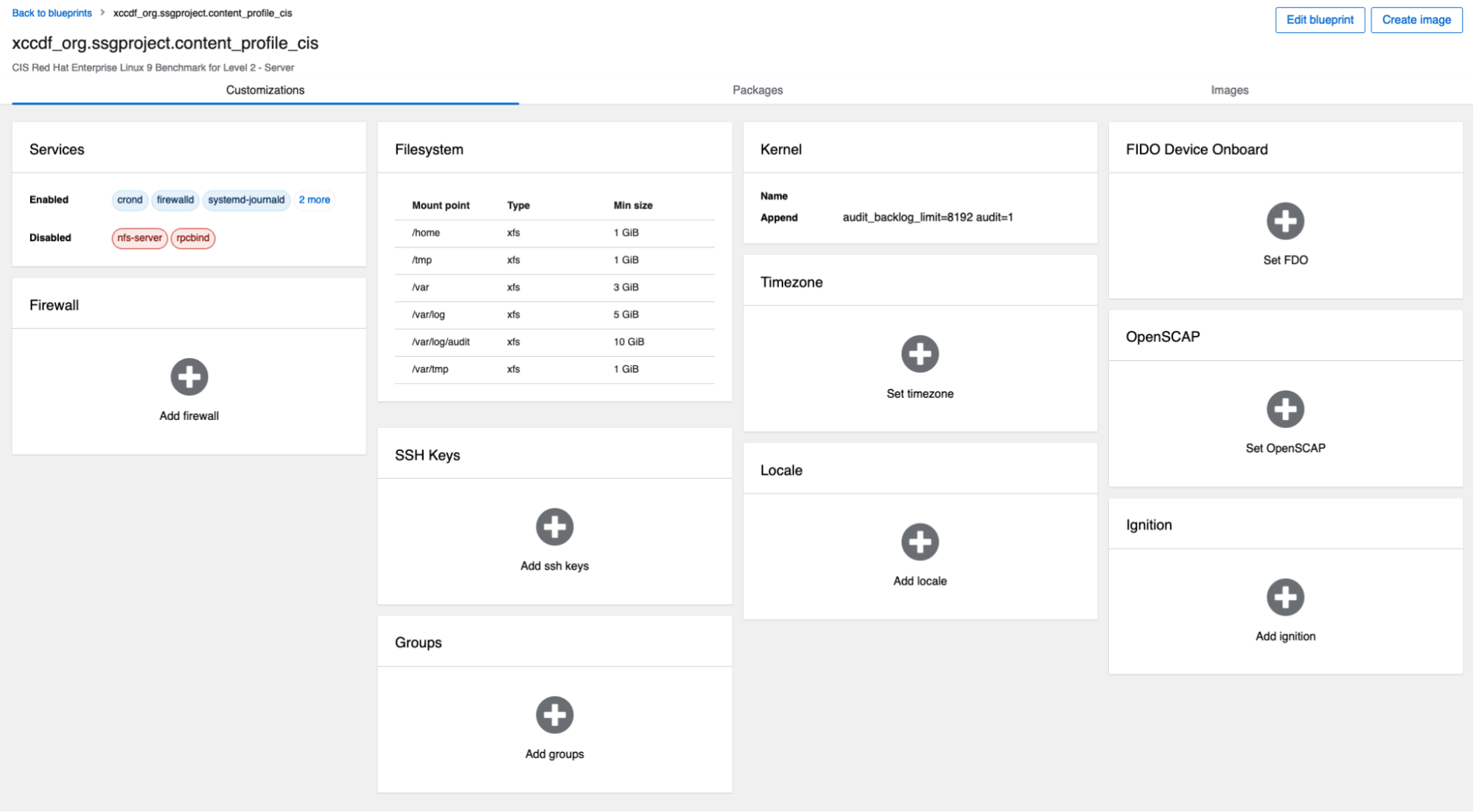
RHEL image builder CIS blueprint
There is already a custom filesystem suggested as well as several services set to be enabled or disabled. We can make a few additional changes, however, in the end only you will be able to determine what configurations need to be adjusted.

In my case, having a workload ready, for instance, Podman containers, makes sense! All the servers in the world won’t get any work done without a workload to sit on top of them. We could also create some users and groups. This is all incredibly dependent upon your use case.
Once you have your CIS-compliant base image defined, it's time to execute a build! Under the Images tab, click "Create image".

It will preselect our blueprint, and now we just need to specify an image type. Since I plan on deploying this system in my home lab, I’ll choose a QEMU image.

Click Next, then Create:
That’s it! Within a few minutes, you’ll have a CIS-ready image you can deploy on any system with libvirt. But that’s not all! You could also choose an ISO for a bare metal installer, a cloud image or a private cloud like VMware. This allows you to deploy the same image anywhere you have a footprint.
Wrap up
With a pre-defined OpenSCAP profile, it’s easier to make your system is workload ready without having to sift through dozens of pages of specifications. From here, it's only a few short steps from a vanilla image to getting your servers registered with Red Hat Insights, where you can monitor your systems’ compliance at scale!
The ability to incorporate OpenSCAP profiles and import/export your blueprint images makes RHEL image builder an even more essential tool for building out new RHEL images for deployment in your local data center, your public or private clouds or even out to the edge!
To learn more, go check out our documentation on Composing a customized RHEL system image!
About the authors
Terry Bowling has been designing and administering UNIX and GNU/Linux environments since 1999. He brings this experience to the Red Hat Enterprise Linux (RHEL) and Insights Product Management teams to provide help streamline the assembling, deployment, and management of RHEL for our customers. Experience it today at redhat.com/image-builder.
More like this
Chasing the holy grail: Why Red Hat’s Hummingbird project aims for "near zero" CVEs
Elevate your vulnerabiFrom challenge to champion: Elevate your vulnerability management strategy lity management strategy with Red Hat
Understanding AI Security Frameworks | Compiler
Data Security And AI | Compiler
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Virtualization
The future of enterprise virtualization for your workloads on-premise or across clouds

